Home Search
two-factor authentication - search results
If you're not happy with the results, please do another search
A New Weaponized Browser Extension Bypass Two-factor Authentication
A New Weaponized Browser Extension Bypass Two-factor Authentication. A new malware strain known as the cybersecurity analysts at Trustwave SpiderLabs recently discovered Rilide.This...
Twitter Limits Two-Factor Authentication Using SMS Only For Blue Subscribers
Twitter has recently made an announcement regarding its two-factor authentication (2FA) service. The company has disclosed that the privilege of using this service will...
Facebook & Instagram Flaw Let Anyone Bypass Two-factor Authentication
The lack of rate-limiting in Instagram was discovered by Gtm Mänôz, a security researcher from Kathmandu, Nepal. This flaw could have allowed an attacker to...
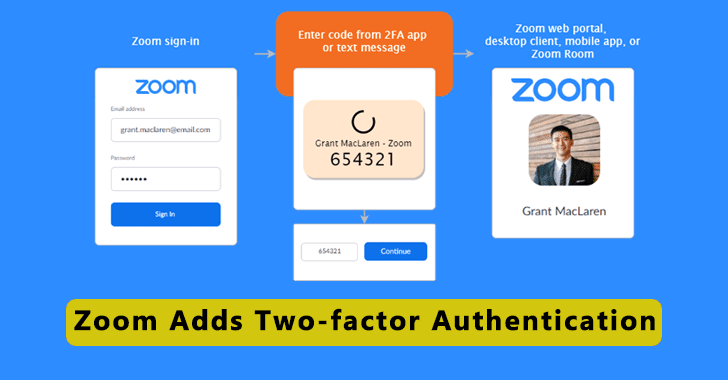
Zoom Adds Two-factor Authentication Available for all Users
Zoom announced Two-Factor Authentication (2FA) for all users that let admins and organizations prevent security breaches & data thefts.The 2FA brings an additional security...
Malicious Apps from Google PlayStore Bypassing SMS-Based Two-Factor Authentication and Steal OTPs in SMS
Researchers discovered new malicious Android apps from Google Play Store bypassing SMS-based two-factor authentication (2FA) mechanisms and steal the OTP without SMS's permission.Google recently...
Now Use Your Android Phone as a Physical Security Key – Google’s New Advanced...
Google announced a new Two-factor authentication method let Android Phone to be used as a physical security key when users log into a Google...
Phishing Campaigns Targeting Google and Yahoo Accounts To Bypassing Two-Factor Authentication
Several phishing campaigns targeting hundreds of individuals across the Middle East and North Africa. The attacker targers HRDs, journalists, political actors.Amnesty International published a...
Hackers can Bypass Two-Factor Authentication with Phishing Attack
Two-factor authentication is an additional layer of security on top of the username and password. It makes it harder for attackers to gain access...
ReelPhish – A Real-Time Advanced Two-Factor Authentication Phishing Tool
Security Firm FireEye Released a new Phishing tool called ReelPhish to simplifies the real-time Phishing attack that is designed to be run on the attacker’s...
How Selfie Authentication Process Improve the Security Along With Other Authentication Methods
Digital identity has two different domains – one is identity proofing and the other is authentication, where both have been unique to each other...












.webp)