

A new family of Android Ransomware dubbed Android/Filecoder.C distributed various online forums and further uses the victim’s contact list to SMS with a malicious link.
ESET detected the ransomware activity since July 12th, 2019, “Due to narrow targeting and flaws in both execution of the campaign and implementation of its encryption, the impact of this new ransomware is limited.”
The ransomware distributed in two methods, through online forums and SMS messages. The threat actors post or comment the ransomware download links on Reddit or XDA Developers forums.
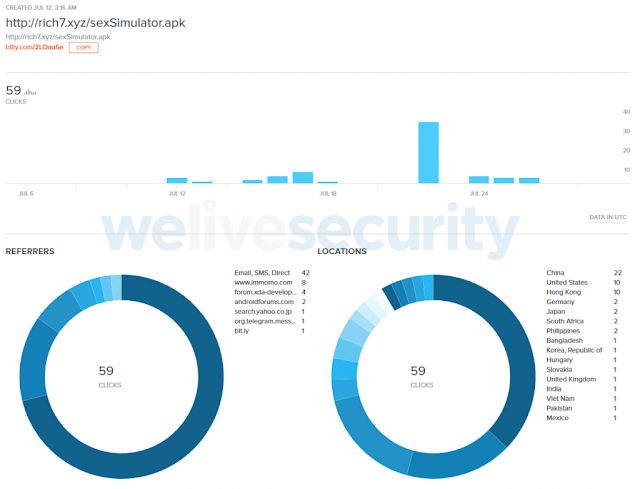
To lure the victim’s the threat actors post the porn-related or tech-related or QR codes that bound with the malicious apps. The attackers also hide the link by using URL shorteners, the bitly shared on Reddit shows it received 59 clicks till now from different countries and link created on Jun 11, 2019.

Also, the ransomware spreads via message, if it infects one device then scans for the victim’s contact list and spreads the malicious links to all the contacts.
By clicking on the link in the SMS, it downloads the malicious file and the victim’s need to install the app, once installed “it displays whatever is promised in the posts distributing it, but it’s intended purpose is C&C communication, spreading malicious messages and implementing the encryption/decryption mechanism,” reads ESET report.
42 languages, C&C and Bitcoin addresses hardcoded in the ransomware, before encrypting the device it spreads the links to all the victim’s, next the ransomware access file storage to start with the encryption process.
Researchers noted that the “files can still be recovered, due to flawed encryption. Also, according to our analysis, there is nothing in the ransomware’s code to support the claim that the affected data will be lost after 72 hours.”
It encrypts the following file types
“.doc”, “.docx”, “.xls”, “.xlsx”, “.ppt”, “.pptx”, “.pst”, “.ost”, “.msg”,
“.eml”, “.vsd”, “.vsdx”, “.txt”, “.csv”, “.rtf”, “.123”, “.wks”, “.wk1”,
“.pdf”, “.dwg”, “.onetoc2”, “.snt”, “.jpeg”, “.jpg”, “.docb”, “.docm”,
“.dot”, “.dotm”, “.dotx”, “.xlsm”, “.xlsb”, “.xlw”, “.xlt”, “.xlm”,
“.xlc”, “.xltx”, “.xltm”, “.pptm”, “.pot”, “.pps”, “.ppsm”, “.ppsx”,
“.ppam”, “.potx”, “.potm”, “.edb”, “.hwp”, “.602”, “.sxi”, “.sti”,
“.sldx”, “.sldm”, “.sldm”, “.vdi”, “.vmdk”, “.vmx”, “.gpg”, “.aes”,
“.ARC”, “.PAQ”, “.bz2”, “.tbk”, “.bak”, “.tar”, “.tgz”, “.gz”, “.7z”,
“.rar”, “.zip”, “.backup”, “.iso”, “.vcd”, “.bmp”, “.png”, “.gif”,
“.raw”, “.cgm”, “.tif”, “.tiff”, “.nef”, “.psd”, “.ai”, “.svg”, “.djvu”,
“.m4u”, “.m3u”, “.mid”, “.wma”, “.flv”, “.3g2”, “.mkv”, “.3gp”,
“.mp4”, “.mov”, “.avi”, “.asf”, “.mpeg”, “.vob”, “.mpg”, “.wmv”,
“.fla”, “.swf”, “.wav”, “.mp3”, “.sh”, “.class”, “.jar”, “.java”, “.rb”,
“.asp”, “.php”, “.jsp”, “.brd”, “.sch”, “.dch”, “.dip”, “.pl”, “.vb”,
“.vbs”, “.ps1”, “.bat”, “.cmd”, “.js”, “.asm”, “.h”, “.pas”, “.cpp”,
“.c”, “.cs”, “.suo”, “.sln”, “.ldf”, “.mdf”, “.ibd”, “.myi”, “.myd”,
“.frm”, “.odb”, “.dbf”, “.db”, “.mdb”, “.accdb”, “.sql”,
“.sqlitedb”, “.sqlite3”, “.asc”, “.lay6”, “.lay”, “.mml”, “.sxm”,
“.otg”, “.odg”, “.uop”, “.std”, “.sxd”, “.otp”, “.odp”, “.wb2”,
“.slk”, “.dif”, “.stc”, “.sxc”, “.ots”, “.ods”, “.3dm”, “.max”,
“.3ds”, “.uot”, “.stw”, “.sxw”, “.ott”, “.odt”, “.pem”, “.p12”,
“.csr”, “.crt”, “.key”, “.pfx”, “.der”
This ransomware doesn’t lock the screen like other ransomware and it won’t encrypt following directories “.cache”, “tmp”, or “temp” and “.zip” or “.rar” over 50 MB and “.jpeg”, “.jpg” and “.png” file less than 150kb. Once the file encryption completed it appends .seven extension to the file and asks users to pay ransom to unlock the files.
But according to ESET researchers, the files can be decrypted without paying the ransom, ” it would be possible to decrypt files without paying the ransom by changing the encryption algorithm to a decryption algorithm. All that is needed is the UserID (see Figure 13) provided by the ransomware, and the ransomware’s APK file in case its authors change the hardcoded key value. So far, we have seen the same value in all samples of the Android/Filecoder.C ransomware.”
Android ransomware spotted almost after 2 years, the previous one that went wild was LOKIBOT which infected many victims and earned more than $1.5 Million around the world.
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity updates also you can take the Best Cybersecurity course online to keep yourself updated.
A new malware named "RustoBot" has been discovered exploiting vulnerabilities in various router models to…
Researchers have uncovered a sophisticated new variant of the notorious Lumma InfoStealer malware, employing advanced…
The notorious Magecart group has been identified by the Yarix Incident Response Team as the…
Cybersecurity in Japan has hit a new low as the Financial Services Agency (FSA) reports…
The Federal Bureau of Investigation (FBI) has issued a warning regarding an emerging scam where…
The Cybersecurity and Infrastructure Security Agency (CISA) has alerted its threat hunting teams to immediately…