

A recently discovered vulnerability in the AWS Systems Manager (SSM) Agent, a cornerstone of Amazon Web Services (AWS) used for managing EC2 instances and on-premises servers, has raised critical security concerns.
This security flaw, identified as a Path Traversal vulnerability, allows attackers to execute malicious code with root privileges, potentially leading to privilege escalation and unauthorized access to sensitive systems.
According to the Cymulate report, the issue originates from insufficient input validation in the ValidatePluginId function located in the pluginutil.go file of the SSM Agent.

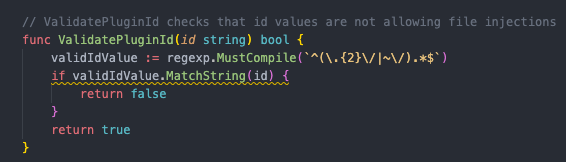
This function is responsible for checking and validating plugin IDs specified in SSM Documents—JSON or YAML-based templates that define tasks to configure or manage systems.
Improper sanitization of the plugin IDs enables attackers to include malicious path traversal sequences (such as ../) to manipulate the file system.

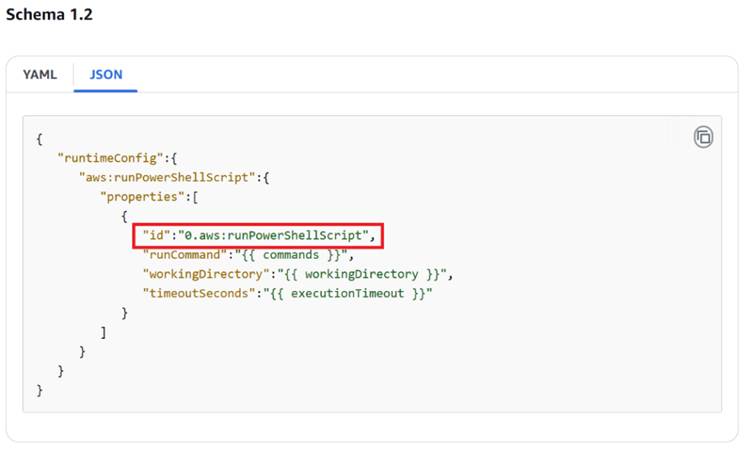
When an SSM Document is executed, the SSM Agent dynamically creates directories named after the plugin ID and executes scripts within them using root privileges.
Due to flawed validation, attackers can craft a malicious plugin ID that directs the agent to create unintended directories and execute commands outside the expected secure locations.
For instance, this could result in scripts being executed in sensitive areas such as /tmp/.
The vulnerability permits attackers to utilize a crafted plugin ID when creating an SSM Document. This input is processed by the SSM Agent to create directories and files in unintended locations.
For example, if the plugin ID contains ../../../../../malicious_directory, the agent interprets this input as a directive to create directories outside its intended scope.
As a result, files such as _script.sh can be executed in arbitrary locations with elevated privileges.
Successful exploitation could enable attackers to:
AWS should take immediate action to address this vulnerability by:
This vulnerability underscores the importance of input validation in preventing exploitation.
Organizations using AWS Systems Manager should remain vigilant, apply security updates promptly, and monitor their systems closely to mitigate potential risks.
At the time of writing, AWS has yet to release a patch, but swift action is anticipated to safeguard its users and infrastructure.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!
The Sekoia TDR (Threat Detection & Research) team has reported on a sophisticated network infrastructure…
The Socket Threat Research Team has unearthed a trio of malicious packages, two hosted on…
Hackers are now exploiting a legitimate Microsoft utility, mavinject.exe, to inject malicious DLLs into unsuspecting…
Small and midsized businesses (SMBs) continue to be prime targets for cybercriminals, with network edge…
Joining Criminal IP at Booth S-634 | South Expo, Moscone Center | April 28 –…
Cybersecurity researchers have uncovered critical SQL injection vulnerabilities in four TP-Link router models, enabling attackers…