

A sophisticated black-hat SEO poisoning campaign has compromised over 150 Indian government websites and financial institutions, redirecting millions of users to fraudulent gambling platforms promoting rummy and high-risk “investment” games.
The operation, exploits vulnerabilities in government portals (.gov.in) and educational domains (.ac.in), leveraging search engine manipulation to siphon users toward scam websites.
Threat actors injected malicious JavaScript code into vulnerable government websites, including state portals, to hijack search engine rankings.
The script identifies traffic originating from search engines like Google and redirects mobile users to gambling platforms such as indorummy[.]net and teenpattionline[.]game, while displaying error pages to desktop users to evade detection.

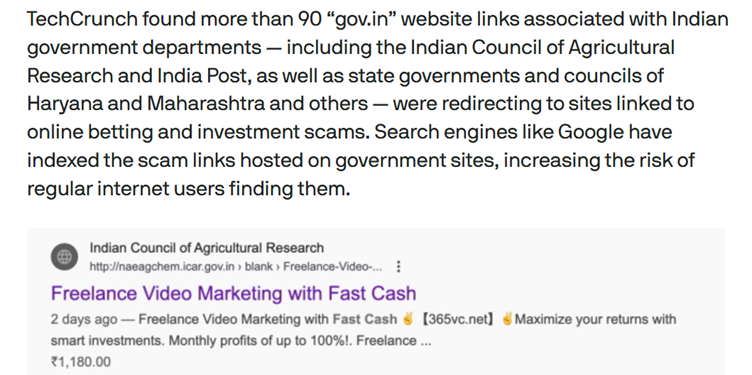
One compromised Kerala government webpage, for instance, was altered to include hidden keywords like “instant personal loans” and “low-interest credit cards” tied to major Indian banks.
Users searching for legitimate financial services are funneled to pages promoting rummy games disguised as “investment opportunities”.
Analysts found over 12,000 spam pages leveraging .shtml and .aspx file uploads on government servers, with content mirroring Indonesian casino templates to bypass regional filters.
The campaign employs multi-layered evasion tactics:
Attackers host malicious domains through Cloudflare’s CDN and AWS infrastructure, masking their origin servers.
Domains like rummydeity[.]cc and crickexlive[.]vip resolve to IPs in Cloudflare’s 104.21.x.x range, complicating takedown efforts.
Secondary domains hosted on Amazon Web Services (18.160.46.x) further disperse the infrastructure, with phishing kits mimicking legitimate banking portals.
Financial and Social Impact on Indian Users
The scam capitalizes on India’s online gambling boom, luring users with fake “referral bonuses” (₹20–80 per sign-up) and “VIP tiers” promising higher returns.
Victims must deposit funds to withdraw earnings, a hallmark of Ponzi schemes. CloudSEK’s analysis of indorummy[.]net revealed embedded SMS phishing templates and fake customer service chatbots that harvest financial data.
Social media complaints surged after the campaign was flagged on LinkedIn and X in late 2024.
Users reported losing ₹50,000–₹2 lakh after initial “wins,” with withdrawal requests blocked unless additional deposits were made.
Despite reports to CERT-In and Google’s Web Risk team, takedowns lag due to the scale of spoofed domains.
Each spam page requires manual review to avoid accidental removal of legitimate content.
The campaign mirrors a 2024 Malaysian incident where government sites were backlinked to casino platforms, underscoring cross-border risks.
Cybersecurity experts urge organizations to:
Google has delisted 2,300 malicious pages since January 2025, but ephemeral domains and encrypted traffic pose ongoing hurdles.
With losses exceeding ₹200 crore annually, this campaign highlights the critical need for proactive defense mechanisms in India’s digital governance infrastructure.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free
Brinker, an innovative narrative intelligence platform dedicated to combating disinformation and influence campaigns, has been…
A recent investigation by cybersecurity researchers has uncovered a large-scale malware campaign leveraging the DeepSeek…
A recent malware campaign has been observed targeting the First Ukrainian International Bank (PUMB), utilizing…
A newly discovered malware, dubbed Trojan.Arcanum, is targeting enthusiasts of tarot, astrology, and other esoteric…
A sophisticated phishing campaign orchestrated by a Russian-speaking threat actor has been uncovered, revealing the…
A sophisticated malware campaign has compromised over 1,500 PostgreSQL servers, leveraging fileless techniques to deploy…