

CISA and Palo Alto Networks are scrambling to contain widespread exploitation of a critical authentication bypass vulnerability (CVE-2025-0108) affecting firewall devices running unpatched PAN-OS software.
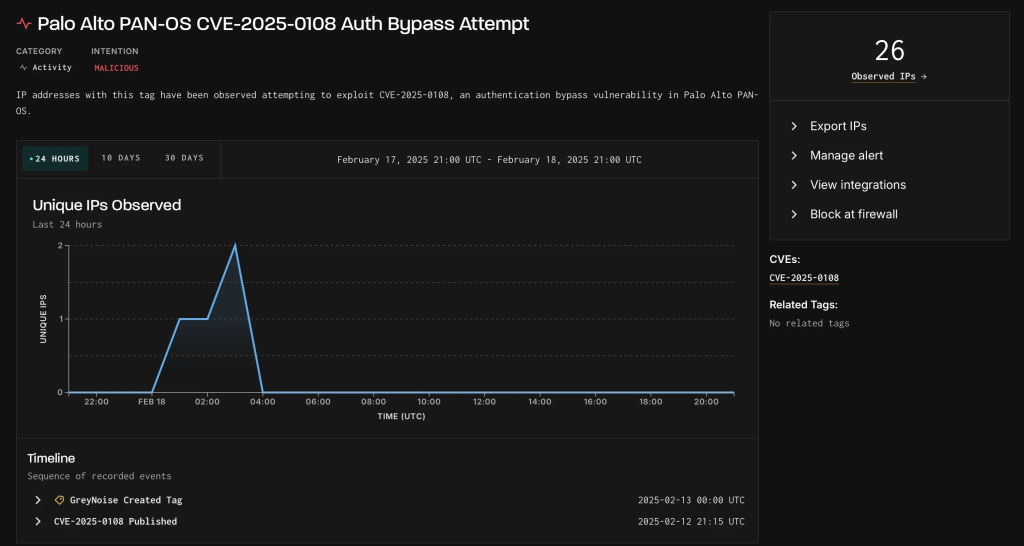
The Cybersecurity and Infrastructure Security Agency (CISA) added the flaw to its Known Exploited Vulnerabilities Catalog on February 19, 2025, following a 900% surge in attack attempts over five days.
CVE-2025-0108 (CVSSv3.1: 7.8) enables unauthenticated attackers with network access to the PAN-OS management interface to bypass authentication checks and execute specific PHP scripts.
Though not directly permitting remote code execution, the flaw allows access to sensitive administrative functions that could expose credentials, configuration data, and system logs.
Palo Alto Networks confirmed that when chained with CVE-2024-9474—a privilege escalation vulnerability patched in November 2024—attackers achieve full device control.
Affected versions include PAN-OS 10.1 (pre-10.1.14-h9), 10.2 (pre-10.2.13-h3), 11.1 (pre-11.1.6-h1), and 11.2 (pre-11.2.4-h4).
According to the Cyber Security News report, malicious activity escalated from 2 IPs on February 13 to 25 by February 18, with 63% of traffic originating from U.S.-based nodes camouflaged behind cloud hosting providers.

Attackers leverage publicly available proof-of-concept exploits derived from technical details published by Assetnote researchers, who identified the flaw while analyzing historical PAN-OS vulnerabilities.
Palo Alto’s updated advisory warns that threat actors primarily target internet-facing management interfaces, often deploying web shells for persistent access.
CISA mandates federal agencies to patch systems by March 6, 2025, while urging private enterprises to immediately:
Shubham Shah of Assetnote emphasized the flaw’s role as an entry point for multi-stage attacks: “This isn’t just about bypassing login screens—teams must assume breached devices will be weaponized via secondary exploits”.
The campaign mirrors tactics used in late 2024 attacks exploiting CVE-2024-0012, where compromised firewalls served as springboards for ransomware deployment.
With over 250,000 Palo Alto firewalls globally, unpatched devices pose systemic risks to energy grids, financial networks, and healthcare systems.
CISA’s alert aligns with its “Secure by Design” initiative pressuring vendors to eliminate default internet-exposed management interfaces.
As Steven Thai, Palo Alto’s senior security advisor, warned: “Every hour without patching increases the likelihood of catastrophic network breaches”.
The escalation underscores the urgent need for coordinated vulnerability disclosure and enhanced monitoring of network infrastructure.
Cybersecurity teams are advised to hunt for anomalous HTTP POST requests to /sslmgr endpoints—a key exploitation indicator. With threat actors actively refining their tactics, the window for mitigation continues to narrow rapidly.
Free Webinar: Better SOC with Interactive Malware Sandbox for Incident Response, and Threat Hunting - Register Here
Brinker, an innovative narrative intelligence platform dedicated to combating disinformation and influence campaigns, has been…
A recent investigation by cybersecurity researchers has uncovered a large-scale malware campaign leveraging the DeepSeek…
A recent malware campaign has been observed targeting the First Ukrainian International Bank (PUMB), utilizing…
A newly discovered malware, dubbed Trojan.Arcanum, is targeting enthusiasts of tarot, astrology, and other esoteric…
A sophisticated phishing campaign orchestrated by a Russian-speaking threat actor has been uncovered, revealing the…
A sophisticated malware campaign has compromised over 1,500 PostgreSQL servers, leveraging fileless techniques to deploy…