

Cloudflare has announced that it will shift its APIs to HTTPS-only connections, effectively closing all HTTP ports.
This strategic decision aims to protect sensitive data from being intercepted by unauthorized parties during transmission.
The change marks a crucial step forward in the company’s mission to safeguard users’ privacy and ensure the integrity of online communications.
Cleartext HTTP poses a significant risk because it transmits data unencrypted, making it vulnerable to eavesdropping by network intermediaries such as ISPs, Wi-Fi hotspot providers, or malicious actors on shared networks.
Even if a server redirects HTTP requests to HTTPS, sensitive information such as API tokens might already have been transmitted in plaintext, exposing it to potential interception.

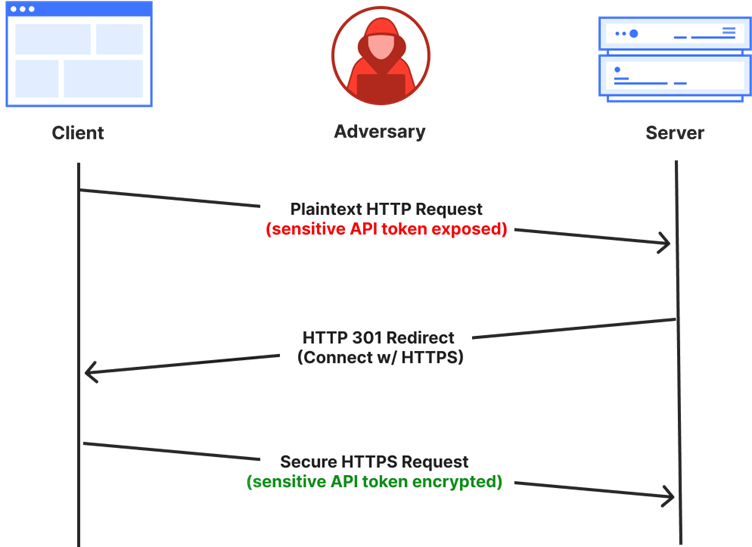
For instance, imagine a client making an initial HTTP request to access Cloudflare’s API. If this request includes a secret API key, the key could be exposed before the server has a chance to redirect or reject the request.
This highlights the need for a more proactive approach to security, one that prevents such exposures altogether.
To address this risk, Cloudflare is taking a preventive approach by closing all HTTP ports used for plaintext communication on its API endpoint, api.cloudflare.com.
This means that any attempt to connect via HTTP will be rejected at the network level before any application-layer data is exchanged. By doing so, Cloudflare eliminates the window of opportunity for sensitive data to be exposed.
This change is not limited to just protecting sensitive client data; it also simplifies operational security. Without the need to continuously monitor and rotate compromised credentials, the overall security posture becomes more robust and efficient.
Implementing this change on a global scale required careful planning. Cloudflare faced two significant challenges: Firstly, there are still a considerable number of devices and software that rely on plaintext HTTP connections.
Closing all HTTP ports entirely could disrupt services for these clients. Secondly, traditional socket management posed scalability issues, particularly when dealing with multiple IP addresses.
Cloudflare addressed these challenges using tools like Tubular, which allows flexible and efficient management of network endpoints.
Tubular’s ability to decouple sockets from specific IP addresses enabled Cloudflare to effectively manage traffic across its vast network without the historical limitations posed by the BSD Sockets API.
The company also leveraged Topaz to dynamically assign IP addresses for HTTPS-only interfaces, ensuring that API traffic was routed correctly.
A new DNS policy was implemented to ensure that only secure IP addresses are returned for API-related queries, further reinforcing the HTTPS-only approach.
By moving to an HTTPS-only model for its APIs and closing all HTTP ports, Cloudflare is setting a strong precedent for securing online communications.
This proactive approach not only enhances security but also simplifies operations by reducing the need for continuous credential rotation.
As the Internet continues to evolve, such measures will become increasingly essential in protecting user privacy and ensuring the integrity of digital interactions.
Cloudflare’s initiative is a step towards a safer Internet, where security is not an added cost but a fundamental aspect of every online interaction.
With its commitment to providing free security features, Cloudflare aims to make a better Internet accessible to everyone.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free
An INTERPOL-led operation, dubbed "Operation Red Card," has resulted in the arrest of over 306…
CleanStack is a novel stack protection mechanism designed to combat memory corruption attacks, which have…
A recent cyber espionage operation by a China-nexus threat actor, dubbed "Weaver Ant," has been…
The Federal Communications Commission (FCC) has initiated a new investigation into Chinese entities previously identified…
VanHelsingRaaS, a newly launched ransomware-as-a-service (RaaS) program, has quickly gained traction in the cybercrime ecosystem.…
A critical vulnerability in the popular WordPress plugin GamiPress has been uncovered, leaving users exposed…