

A recent discovery has revealed a potential supply chain attack vulnerability in GitHub’s CodeQL repositories, which could have led to wide-ranging consequences for hundreds of thousands of GitHub users.
The exploit hinges on a publicly exposed secret found in a GitHub Actions workflow artifact, which, if utilized by an attacker, could allow malicious code execution in multiple repositories.
Despite GitHub’s assertions that no compromise occurred, the severity of this vulnerability highlights the ongoing challenges in maintaining the security of continuous integration and continuous delivery (CI/CD) environments.
CodeQL is GitHub’s powerful code analysis engine designed to identify vulnerabilities in repository code.
It has been instrumental in discovering several hundred CVEs, protecting organizations from potential breaches. However, this same critical role makes it an attractive target for attackers looking to exploit vulnerabilities.
GitHub Actions, on the other hand, is the platform’s CI/CD tool. It automates workflows for building, testing, and deploying code across repositories.
These workflows often rely on tokens like the GITHUB_TOKEN to authenticate and interact with GitHub. Tokens with high privileges pose significant risks if compromised.

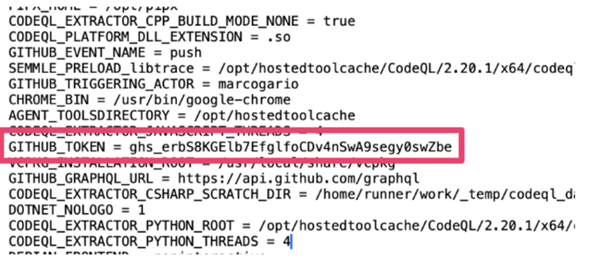
In January 2025, security researchers embarked on a project to explore potential vulnerabilities in GitHub Actions workflows.
This investigation used a custom-built Actions Artifact Secrets Scanner, which downloaded and scanned GitHub Actions artifacts for exposed secrets.
The scanner uncovered a GitHub App installation token buried within an artifact from the github/codeql-action repository. This token, although valid for only a short duration, had full write permissions.
The exposed secret posed a risk because it was stored in an artifact uploaded during a workflow job using the v4 artifact upload API.
This allowed potential attackers to retrieve the artifact and extract the token before the workflow job completed. The crux of the vulnerability was the race against time: attackers had about two seconds to exploit the token before it expired.
To demonstrate the exploit’s potential, researchers created a Python script named artifact_racer.py.
This tool continuously monitored the github/codeql-action repository for specific workflows, downloaded associated artifacts when detected, extracted the GITHUB_TOKEN, and used it to create a new branch and push an empty file to the branch.
The successful execution of these actions within the two-second window confirmed that an attacker could indeed exploit the vulnerability for malicious purposes.
The implications of this vulnerability are far-reaching. If an attacker could manipulate the github/codeql-action repository by adding malicious code and tags, they could compromise hundreds of thousands of repositories that enable CodeQL.
This could involve:
The discovery was responsibly disclosed to GitHub, which investigated and acknowledged the vulnerability as CVE-2025-24362.
Despite no reported compromises, the situation highlights the importance of vigilant monitoring and secure practices in managing CI/CD environments.
The “CodeQLEAKED” incident underscores the challenges in securing complex software ecosystems like GitHub.
It emphasizes the need for robust secret management practices, timely vulnerability disclosure, and strict monitoring of workflow artifacts to prevent similar supply chain attacks.
As code repositories increasingly depend on automation tools like GitHub Actions and analysis engines like CodeQL, ensuring their integrity is crucial for protecting intellectual property and maintaining security across digital ecosystems.
Are you from SOC/DFIR Teams? – Analyse Malware, Phishing Incidents & get live Access with ANY.RUN -> Start Now for Free.
Cisco Talos has uncovered an ongoing cyber campaign by the Gamaredon threat actor group, targeting…
Researchers have uncovered a dangerous new mobile banking Trojan dubbed Crocodilus actively targeting financial institutions…
From WannaCry to the MGM Resorts Hack, ransomware remains one of the most damaging cyberthreats…
Cybersecurity researchers have discovered a sophisticated phishing-as-a-service (PhaaS) platform, dubbed "Morphing Meerkat," that leverages DNS…
A recently identified Remote Access Trojan (RAT) has raised alarms within the cybersecurity community due…
PJobRAT, an Android Remote Access Trojan (RAT) first identified in 2019, has resurfaced in a…