

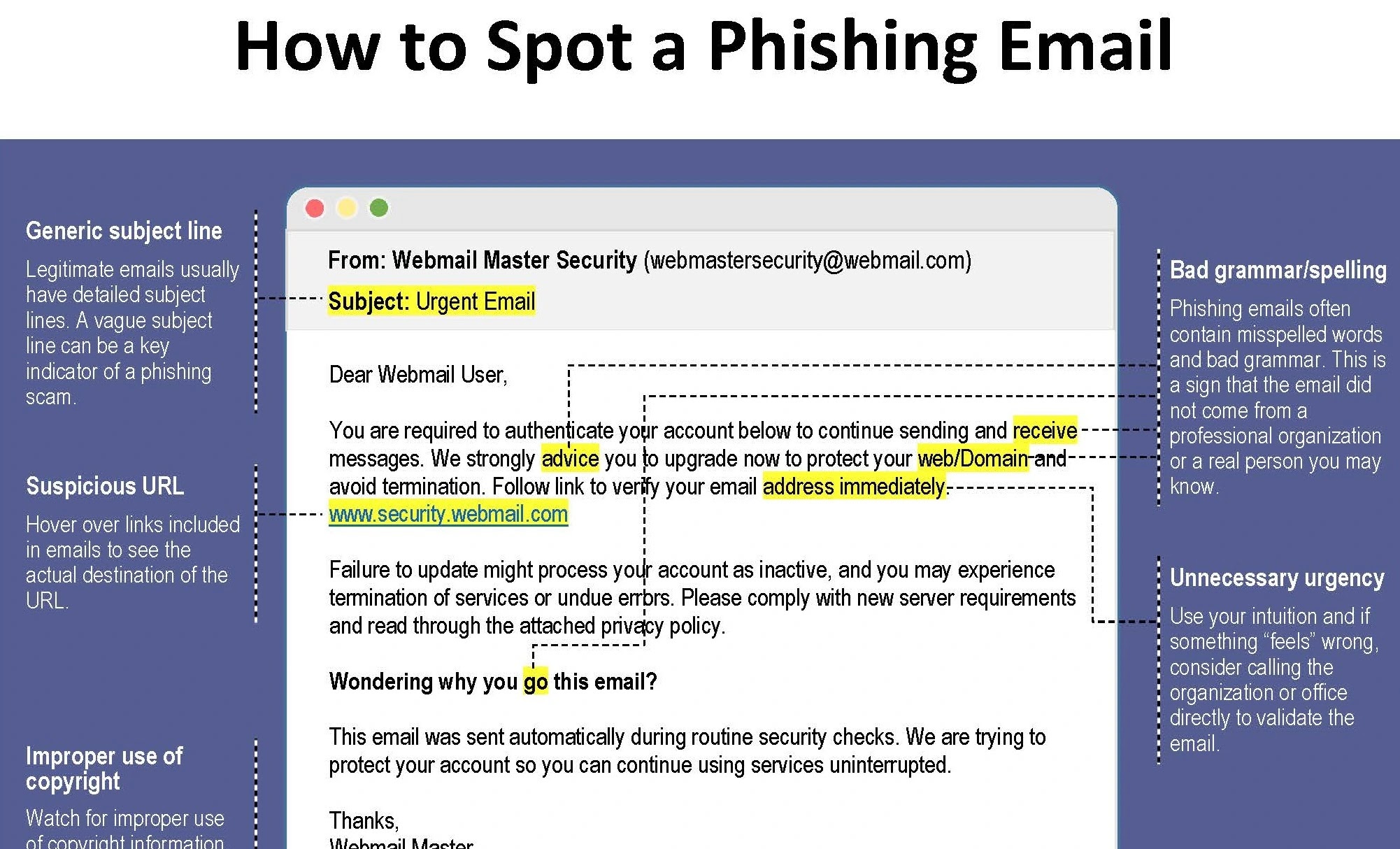
Cybercriminals use email phishing as one form of cybercrime to deceive victims into disclosing personal information like passwords, credit card details, or Social Security numbers.
To accomplish this, they send emails that seem to be from reliable sources, like banks, credit card companies, or even close friends or relatives.
According to the Trustifi ThreatScan Report 2023, an in-depth analysis of 1.3 million emails exposes the staggering number of threats evading conventional gateway solutions. Download Free Report.
Frequently, the emails include a link that, when clicked, directs the recipient to a fake webpage that mimics the official website.
Criminals can steal the information the victim enters on fictitious websites.
Because targeted phishing emails can be very convincing, it is critical to watch out for the following warning signs:

According to statistics, 81% of organizations have seen an increase in phishing emails since 2020, with an estimated 3.4 billion emails sent every day.
Data breaches and other financial losses cost individuals and companies billions of dollars annually.
Depending on the location, it impacts people and organizations globally with varying frequency and approaches.
Increasingly skilled phishing attackers use social engineering, deep fakes, and tailored strategies to circumvent traditional security measures.
In this case, automatically disabling access to compromised accounts with Trustifi’s AI-based account takeover protection helps to prevent sensitive data exposure.
Trustifi’s Advanced threat protection prevents the widest spectrum of sophisticated attacks before they reach a user’s mailbox. Try Trustifi Free Threat Scan with Sophisticated AI-Powered Email Protection .
AI-generated phishing emails are a sophisticated and evolving cybersecurity threat. These emails use artificial intelligence to craft messages that are highly personalized and convincing, often mimicking the style and tone of legitimate correspondence from trusted sources such as banks, service providers, or even colleagues and friends. The primary goal is to deceive recipients into divulging sensitive information, clicking on malicious links, or downloading infected attachments.
The use of AI in phishing campaigns allows for several advancements in the effectiveness of these attacks:
To protect against AI-generated phishing emails, it’s essential to employ a combination of advanced cybersecurity technologies, such as AI-based threat detection systems, and user education to recognize and respond to phishing attempts. Strategies include scrutinizing the sender’s email address for slight abnormalities, avoiding clicking on links or downloading attachments from unsolicited emails, and verifying the legitimacy of requests for sensitive information through alternative communication channels.
Worrying About Sophisticated Email Threats? – Deploy Email Managed Detection & Response in Your IT Environment.
The battle against email phishing utilizes several critical AI techniques, all of which are vital in identifying and foiling these malicious attempts:
It enables AI to decipher and evaluate email content’s semantic meaning. AI systems that have been trained on enormous email datasets are able to recognize questionable terms, expressions, and sentence patterns that are frequently employed in phishing scams.
NLP also assists in sentiment and tone analysis, identifying deceptive language or urgency frequently employed in phishing emails.
Allows AI to gradually increase the accuracy of its detections by learning from data. Artificial intelligence (ML) algorithms examine past attempts at phishing and authentic emails, spotting trends and characteristics that set them apart.
The models get better at identifying fresh phishing techniques and adjusting to changing threats as more data is added.
In order to detect irregularities and possible forgeries used in phishing attempts, deep learning models can examine not only the content of emails but also visual components like logos and formatting.
AI can analyze sender information, header data, and metadata in addition to the content of emails.
Artificial intelligence (AI) can detect unusual departures from standard operating procedures, such as emails that appear to be sent from strange places or have inconsistent sender addresses, which may be signs of spoofing attempts.
Implementing AI-powered email security solutions can secure your business from today’s most dangerous email threats, such as Email Tracking, Blocking, Modifying, Phishing, Account takeover, Business Email Compromise, Malware, & Ransomware – Request Free Demo.
Trustifi is a leading cyber security firm that provides top-notch email encryption, data loss prevention, and hosting solutions on a software-as-a-service platform.
Trustifi is a leading provider in the email security market, offering highly effective solutions to protect clients’ emails from cyber attacks. Our products are designed to be user-friendly and easy to deploy, ensuring maximum security for your email communications.
Trustifi offers a comprehensive email security solution that includes both inbound and outbound protection. Our system is equipped with multiple layers of security to ensure the safety of your emails. Additionally, we provide advanced features that are based on internal metrics, third-party integrations, and artificial intelligence. With Trustifi, you can enjoy all these benefits from a single vendor.
Cybercriminals continue to use email phishing as an attack, and their strategies are always changing.
In the struggle against these malicious emails, artificial intelligence (AI) based email security solutions is becoming a more potent tool. To counteract email phishing, AI can be applied as follows:
| Outbound Shield | Rest easy knowing emails are automatically delivered securely and in compliance with easily-enabled Data Classification and Data Loss Prevention standards. Implementation takes minutes with automatic Office 365, Exchange on-premise, and Google Workspace interfaces. |
| Inbound Shield | Trustifi’s Powerful multi-layered screening protects your company from targeted attacks. Analyze, identify, and categorize sophisticated Phishing, Malicious, SPAM, and Gray emails. |
| Email Managed Detection and Response | Our professional email security specialists can handle threat response and support your IT/Sec teams. |
| Advanced Cloud Mail Archiving | Cloud-based email access is safe and convenient. Set controls and permissions to track and record user activity. Sharing data, cases, and inquiries with particular receivers is easy with sophisticated authentication and real-time monitoring. |
| Account Take-over Protection | AI Engines detect and inform users when monitoring volume, context, devices, geo-location, kind of sent emails, and more have hacked their mailboxes. |
To Prevent businesses from sophisticated phishing Attacks, Trusitifi’s AI-powered email security solution Stops 99% of phishing attacks missed by other email security solutions.
Scenario: Searching email content for questionable wording, such as threats, urgency, or attempts at impersonation.
Example: An email with grammatical errors purporting to be from your bank, and requesting quick action is identified by an AI model. It indicates that it might be a phishing attempt.
Trusitifi catches over 90% of sophisticated phishing attacks that traditional email security platforms miss.
Scenario: Tracking the ways in which specific users send emails and spotting changes from their usual conduct.
Example: The AI marks email correspondence from an employee that sends a sudden surge of correspondence to odd recipients as possibly suspicious activity, requiring additional examination.
Scenario: Applying artificial intelligence to analyze attachments in a virtual setting before their arrival on users’ devices.
Example: AI opens unseen attachments in emails in a sandbox and looks for malware by analyzing the attachment’s behavior. Before it reaches the user, malicious content is blocked.
Scenario: To more accurately identify spam, AI goes beyond conventional keyword-based filtering and looks at user behavior, email content, and sender reputation.
Example: By filtering out spam emails proactively, an AI model recognizes emails that look like legitimate marketing messages but do not have the sender’s usual content or personalization.
Scenario: Recognizing private information in emails, such as social security or credit card numbers, and putting the proper security measures in place.
Example: AI recognizes and encodes sensitive data in emails before sending them to prevent unwanted access in the event of a breach.
When it comes to analyzing intricate email features, AI outperforms conventional rule-based filters. It goes beyond just keywords and looks at things like sentiment, sentence structure, and contextual details like the relationship between the sender and the recipient.
Because of its multiple layers, this approach minimizes false positives and negatives and improves the accuracy of phishing attempt detection.
It offers personalized security that goes beyond simple filtering by examining email usage patterns and behavior patterns to spot anomalies unique to each user.
By automatically improving their detection capabilities, they provide a dynamic and constantly-improving defense system as they examine more data and come across fresh phishing attempts.
Ideal for large businesses and email service providers, as traditional approaches find it difficult to handle heavy traffic volumes.
Phishing data, including fresh attack strategies and patterns, and automatically modify their detection systems to provide proactive defense against new threats and zero-day exploits.
Save time, money, and mitigate risks, all while increasing your organization’s overall email security posture using Trustifis’ Email Managed and Detection Response tool.
If you’re in need of additional security for your current email setup or a comprehensive suite solution, Trustifi’s expertise and user-friendly approach will surpass your expectations. Let’s explore a tailored email security plan that aligns perfectly with your requirements.
Artificial intelligence (AI) has emerged as a potent weapon on the defensive in the ongoing battle against email phishing.
Even the most sophisticated phishing attempts are difficult for traditional filters to detect; AI goes deeper, examining complex email features, sentiment, and context.
With its dynamic shield against ever-evolving threats, this cutting-edge technology provides personalized security, adjusts to individual behavior, and learns continuously. There are, nevertheless, restrictions.
Attackers may take advantage of blind spots, biases may skew detection, and false positives and negatives may happen.
Openness, moral reflection, and continuous development are necessary to overcome these constraints.
Ultimately, AI is not a silver bullet. Training and human awareness are still vital.
Yet we can tip the odds considerably in favor of a safer and more secure email experience if we use AI wisely and effectively.
You can try AI-powered Protection for Business Email Security from Trusitifi to stop sophisticated attacks before they reach a user’s inbox. Request a Free Demo.
Secure Ideas, a premier provider of penetration testing and security consulting services, proudly announces its…
Symantec has recently identified a sophisticated phishing campaign targeting users of Monex Securities (マネックス証券), a…
In a concerning development, CERT-UA, Ukraine's Computer Emergency Response Team, has reported a series of…
Hunters International, a ransomware group suspected to be a rebrand of the infamous Hive ransomware,…
In a recent cyberattack attributed to the Qilin ransomware group, threat actors successfully compromised a…
A newly uncovered cyber-espionage campaign, dubbed Operation HollowQuill, has been identified as targeting academic, governmental,…