

Cyber attack prevention for Small businesses very has to get serious about their cybersecurity. Hackers are now actively Performing Targeted cyber attack due to their weak security. In fact, 43 percent of cyberattacks today are aimed at smaller firms.
Unfortunately, falling victim to cyberattacks can be devastating. Cyberattacks can cause downtime, damaged reputation, and lost revenue that most small businesses struggle to bounce back also cyber attack prevention is quite a challenging part for small scale businesses.
On the upside, if you’re a small business owner, know that it’s possible for you to improve your security. Security solutions providers are making their security tools more affordable for small companies.
It’s now possible to subscribe to cloud-based antimalware and firewall services that can provide similar protection to what large enterprises already enjoy.
Aside from these more conventional solutions, even more, advanced measures such as breach and attack simulation (BAS) are now becoming more accessible to small businesses.
BAS can help you check if any cyber attack prevention and security solution or measure you deploy actually works.
BAS platform Cymulate, for instance, allows you to comprehensively check your defensive perimeter for potential vulnerabilities by launching simulated attacks against it.
The various multi-vector tests can probe firewalls for potential gaps and even endpoint security solutions if they can readily detect malicious payloads.

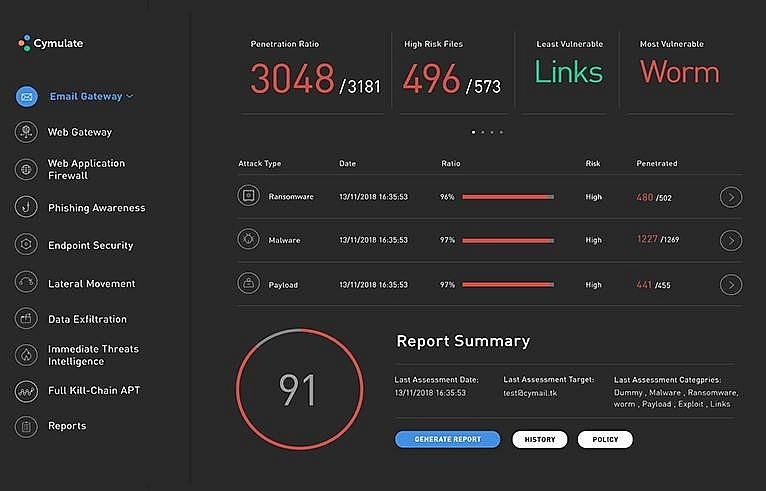
It can even perform simulated phishing attacks to see which users are likely to fall for social engineering attacks.
By knowing these pitfalls, you will be able to make the necessary adjustments or changes to plug the gaps.
Mind you, the threat is real. It’s not unlikely for hackers to be targeting your company right now. As such, you must implement stringent security measures that can thwart even complex threats.
Here are five steps you can take to ensure that your company’s data is protected.
1 – Determine a Baseline of Security Needs
2 – Invest in Capable Security Solutions
3 – Implement Strict Access Controls
4 – Schedule Backups and Regularly Update Software
5- Train and Educate Employees
It’s easy for business owners to get overwhelmed by the multitude of security solutions for cyber attack prevention being marketed to small businesses.
It’s important for you to first understand what your business needs are so that you’d know what kind of IT infrastructure would be needed to support these needs. It’s easy to waste your precious resources by going over the top in your IT and security spending.
Understand which business areas have to be supported by technology. This way, you’ll be able to identify what software and hardware will you be needing. In addition, know where your data will reside.
Will you be using an on-premises server or cloud storage? From this clear picture of your infrastructure, it would be possible to identify what security solutions are needed to protect each of these components.
If your small office network only has three workstations, acquiring security solutions built for large enterprises such as IT management platforms or even security information and event management (SIEM) tools can be quite excessive.
You will most likely not be able to realize your return on investment if you simply acquire tools without aligning them to your situation.
Regardless of size, however, it’s important for you to check the status of your defenses. This is where BAS comes in handy. For cyber attack prevention, Cymulate can perform a comprehensive audit of all endpoints and components for vulnerabilities.
It only takes one faulty endpoint for you to fall victim to a cyberattack even with a small office network.
Investing in capable security tools is an obvious step for you to take in beefing up your cybersecurity. Endpoint protection such as antimalware and antiviruses and network security tools such as firewalls are among the essential solutions you should be implementing.
You may have to look beyond free tools and invest in more advanced solutions that can detect and combat advanced threats.
Fortunately, many enterprise-grade solutions are now available through the cloud. They can be easily acquired through flexible and affordable subscriptions. Most feature easy integrations that even an ordinary tech-literate user can implement them without much fuss.
You must also be able to test and check the effectiveness of these tools. BAS can routinely check the performance of your security measures.
Cymulate allows you to schedule and automate tests to see if your antiviruses or firewalls are screening threats and attacks as intended and thus creating to build a cyber threat assessment profile.
Hackers use various methods to gain access to your computers and online accounts. Among the common techniques they use is brute forcing where they use vast numbers of username and password combinations to find a match to an existing user account.
Hackers usually have an extensive database of commonly used passwords so if one of your accounts happen to use a combination that’s in their list, that account will easily be breached.
Brute forcing will less likely be successful if you use passphrases. Instead of using words with special symbols and capitals, phrases are longer and hard to guess but can still be easily remembered.
Enabling two-factor authentication is one of the cyber attack prevention methods that can also add an extra layer of account protection. An additional access requirement such as a one-time password (OTP) sent to an email account or mobile phone can impede hackers even if they already cracked the username and password combination.
It’s also important to discourage credentials reuse. Users who use the same password for their personal and professional accounts are putting both your company and themselves at risk.
You can use a password manager to create and manage strong, unique passwords for every account. This way, you’d also be able to track who gets access to specific accounts and components in your infrastructure.
Even with capable security solutions, it’s also prudent to prepare for breaches. Some hackers are cruel enough to not just steal data but destroy users’ copies as well. To prevent your data from getting absolutely destroyed, scheduled and maintain backups.
You can use a secure cloud storage solution that mirrors the documents found on your local computers. Most solutions allow you to restore your data in case they’re corrupted due to a malware attack.
Attacks that can potentially damage and steal sensitive information can also be avoided if you use updated software. Updates usually address vulnerabilities that hackers can easily exploit.
So, for cyber attack prevention don’t dismiss update notifications and just click the “remind me later” button. Most applications now have an automatic update feature. You or your IT team can configure installed applications and operating systems to update automatically. You can also send a company-wide reminder to employees for software that needs to be updated manually.
Social engineering attacks such as phishing continue to be among the popular ways hackers try to gain access into systems. In fact, 57 percent of small businesses that were attacked said they were phishing victims. You must ensure that your employees will not easily fall for these scams.
Cymulate can be configured to perform simulated phishing attacks to your actual email system. These simulated phishing emails can even be configured to use well-crafted and cleverly disguised templates to more capably test your staff members’ ability to spot fraudulent emails.
The tests are able to identify which specific user accounts fall for such attacks. This way, you will be able to perform the necessary intervention and train your staff.
Conducting cybersecurity training should be part of your on-boarding process. Through training, everyone would understand the seriousness of even just one small mistake can cause.
Regular training will also help your employees develop a security-first mindset. They’d know how to manage and use security tools effectively, spot phishing attacks, and detect suspicious activities in a network.
Most small businesses can’t afford to suffer a major security breach. Thus, building a strong security perimeter that can combat modern threats should be one of your top priorities.
Following these steps, while not entire foolproof, can greatly enhance your cybersecurity and reduce the possibility of getting hacked. Ultimately, doing your due diligence can help you safeguard sensitive data and can save your company from harm.
A newly identified phishing campaign is targeting unsuspecting users by masquerading as urgent Zoom meeting…
A newly identified piece of malware, dubbed the "Hannibal Stealer," has emerged as a significant…
Advanced persistent threat (APT) groups with ties to China have become persistent players in the…
Cache timing side-channel attacks have been used to circumvent Kernel Address Space Layout Randomization (KASLR)…
Cybersecurity researchers have unearthed a sophisticated attack leveraging AutoIT, a long-standing scripting language known for…
A disturbing 67% of businesses in eight worldwide markets—the US, UK, Spain, the Netherlands, Germany,…