

DeepSeek iOS app—a highly popular AI assistant recently crowned as the top iOS app since its January 25 release—has been discovered to transmit sensitive user data to ByteDance servers without encryption.
The security flaws, uncovered by mobile app security firm NowSecure, have prompted swift reactions from governments, enterprises, and cybersecurity experts worldwide.
The findings paint a sobering picture of the app’s vulnerabilities and its risk to users’ sensitive information.
NowSecure’s comprehensive assessment of the DeepSeek iOS app has exposed alarming security issues affecting millions of users worldwide, including individuals, enterprise employees, and government officials.
Despite its meteoric rise in popularity, the app harbors critical vulnerabilities that make it a significant threat to data privacy.

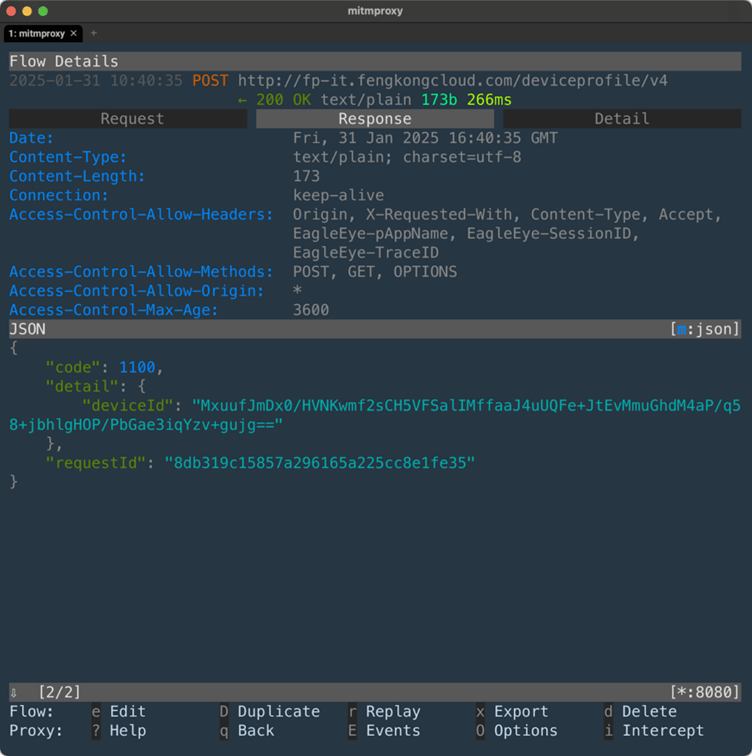
Key Findings:
One of the report’s most alarming revelations is the direct transmission of user data to ByteDance servers, facilitated through its Volcengine cloud service.
ByteDance’s connection to the Chinese government and its legal obligations under PRC surveillance laws have heightened fears of state-driven data access and surveillance.
While ByteDance has repeatedly denied allegations of data sharing with the Chinese government, regulatory agencies and governments remain deeply wary.
The DeepSeek app’s practices may further fuel geopolitical tensions in the realm of digital data privacy.
The fallout has been swift and sweeping. Several governments and organizations, including the U.S. military and state agencies, have issued immediate bans on the app to safeguard national security.
Enterprises have taken similar actions, prohibiting its use on managed and Bring Your Device (BYOD) environments.
For affected users, uninstalling the app and resetting credentials used within it are necessary first steps to protect personal and organizational data.
The revelations have also reignited debate around app store accountability. While Apple enforces strict app review policies, critics argue that security flaws like those in DeepSeek highlight the limitations of existing safeguards.
“Apple and Google must step up their app vetting processes to prevent apps with severe security risks from reaching consumers,” cybersecurity expert Dr. Amelia Jensen said.
“Mobile apps are an unprotected attack surface, and as DeepSeek shows, even widely popular apps can be compromised.”
The DeepSeek debacle underscores the urgent need for stricter data privacy measures, secure app design, and vigilant oversight in the digital age.
As more organizations banish the app, its vulnerabilities serve as a stark warning about the high stakes of mobile app security in a globally interconnected network.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free
The European Union has escalated its response to Russia’s ongoing campaign of hybrid threats, announcing…
Venice.ai has rapidly emerged as a disruptive force in the AI landscape, positioning itself as…
Deep Instinct’s GenAI-powered assistant, DIANNA, has identified a sophisticated new malware strain dubbed BypassERWDirectSyscallShellcodeLoader. This…
A major cybersecurity incident has come to light after researcher Jeremiah Fowler discovered a publicly…
A disturbing new formjacking malware has emerged, specifically targeting WooCommerce-based e-commerce sites to steal sensitive…
A security vulnerability was recently discovered in GitLab Duo, the AI-powered coding assistant integrated into…