

Hackers have been targeting Microsoft Copilot, a newly launched Generative AI assistant, to carry out sophisticated phishing attacks.
This campaign highlights the risks associated with the widespread adoption of Microsoft services and the challenges that come with introducing new technologies to employees, as per a report by Cofense.
Microsoft Copilot, similar to OpenAI’s ChatGPT, is designed to assist users with tasks such as transcribing emails and drafting documents in Microsoft Word.

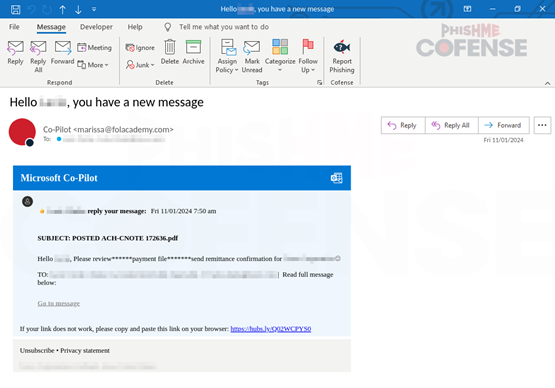
However, its novelty has created an environment where employees may not be fully familiar with its features, making them more susceptible to phishing attempts.
To combat these threats, companies need to educate employees about their use of new services like Microsoft Copilot.
This includes communicating whether these services are provided free of charge or will incur costs.
IT departments should distribute guidance that includes visual examples of legitimate communications to help employees identify potential phishing attempts.
By ensuring that employees are well-informed and aware of the official communications they should expect from Microsoft, workplaces can significantly reduce the risk of falling prey to such sophisticated phishing attacks.
As technology continues to evolve and incorporate more AI tools, vigilance and education are critical components in maintaining digital security.
The exploitation of Microsoft Copilot by hackers underscores the importance of keeping employees informed about the tools and services they use.
As businesses adopt more advanced technologies, they must also prioritize cybersecurity education to protect against emerging threats.
Are you from SOC/DFIR Teams? – Analyse Malware Incidents & get live Access with ANY.RUN -> Start Now for Free.
A new project has exposed a critical attack vector that exploits protocol vulnerabilities to disrupt…
A threat actor known as #LongNight has reportedly put up for sale remote code execution…
Ivanti disclosed two critical vulnerabilities, identified as CVE-2025-4427 and CVE-2025-4428, affecting Ivanti Endpoint Manager Mobile…
Hackers are increasingly targeting macOS users with malicious clones of Ledger Live, the popular application…
The European Union has escalated its response to Russia’s ongoing campaign of hybrid threats, announcing…
Venice.ai has rapidly emerged as a disruptive force in the AI landscape, positioning itself as…