

A critical cybersecurity alert has been issued following the active exploitation of a Server-Side Request Forgery (SSRF) vulnerability in OpenAI’s ChatGPT infrastructure.
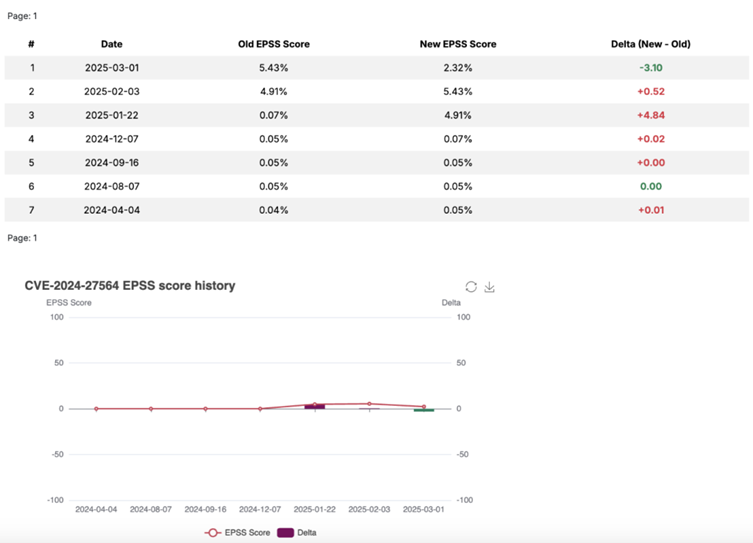
According to the Veriti report, the vulnerability, identified as CVE-2024-27564, has been weaponized by attackers in real-world attacks, highlighting the dangers of underestimating medium-severity vulnerabilities.
CVE-2024-27564 allows attackers to inject malicious URLs into application input parameters, forcing the system to make unintended requests.
Despite being classified as a medium-severity vulnerability, it has been used in over 10,479 attack attempts from a single malicious IP, according to research by Veriti.
Key Findings

Financial institutions are particularly vulnerable as they heavily rely on AI-powered services and API integrations.
These SSRF attacks can lead to data breaches, unauthorized transactions, regulatory penalties, and reputational damage. Ignoring medium-severity vulnerabilities can have costly consequences, especially for high-value financial organizations.
Security teams often focus on patching critical and high-severity vulnerabilities, overlooking medium-severity ones.
However, attackers exploit any available vulnerability regardless of its ranked severity. The exploitation trends change frequently; a once-neglected vulnerability can quickly become a preferred attack vector.
Automated attacks scan for weaknesses, not severity scores, and misconfigured systems provide easy entry points, even for well-secured networks.
CVE-2024-27564 serves as a stark reminder that no vulnerability is too small to ignore. Attackers exploit whatever weaknesses they can find, which makes it crucial for organizations to remediate all vulnerabilities, regardless of their severity rating.
The emphasis should be on ensuring that all systems, particularly those with critical data such as financial institutions, are properly configured to prevent SSRF attacks.
This includes regularly reviewing and updating IPS, WAF, and firewall settings to protect against emerging threats.
The exploitation of CVE-2024-27564 highlights the importance of proactive cybersecurity measures.
Organizations must prioritize a comprehensive approach to vulnerability management, recognizing that even medium-severity vulnerabilities can become significant threats if exploited.
By doing so, they can safeguard their infrastructure and protect sensitive information from falling into the wrong hands.
Are you from SOC/DFIR Teams? – Analyse Malware Incidents & get live Access with ANY.RUN -> Start Now for Free.
DocuSign has emerged as a cornerstone for over 1.6 million customers worldwide, including 95% of…
In a landmark initiative, international cybersecurity agencies have released a comprehensive series of publications to…
A severe security flaw has been identified in the TI WooCommerce Wishlist plugin, a widely…
Microsoft Threat Intelligence Center (MSTIC) has issued a critical warning about a cluster of global…
A recent investigation by security analysts has uncovered a persistent phishing campaign targeting Italian and…
Threat actors have exploited a critical Remote Code Execution (RCE) vulnerability, identified as CVE-2025-32432, in…