

A sweeping wave of suspicious online activity is putting organizations on alert as hackers ramp up their efforts to probe vulnerabilities in Ivanti Connect Secure (ICS) and Ivanti Pulse Secure (IPS) VPN systems.
Cybersecurity firm GreyNoise has identified a dramatic nine-fold increase in suspicious scanning activity, suggesting coordinated reconnaissance that could foreshadow future exploitation.
According to GreyNoise, more than 230 unique IP addresses targeted ICS and IPS VPN endpoints on April 18 alone—a sharp escalation from the typical daily average of fewer than 30.

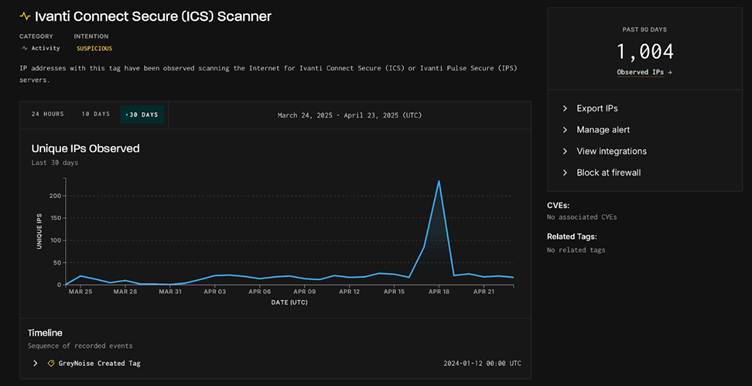
Even more concerning, over the past 90 days, the number of unique IPs involved in similar activity soared to 1,004.
“This isn’t just isolated noise,” a GreyNoise spokesperson explained. “Spikes like this are often the prelude to more serious threats, particularly as attackers look for new vulnerabilities before they’re publicly disclosed.”
The cybersecurity firm’s analysis paints a detailed picture of the infrastructure behind these probes:
Importantly, all identified IPs are “not spoofable,” meaning attackers are not attempting to disguise their origin—a sign of confidence or automation in their approach.
The scans are not limited to a single region. The top source countries for these scanning activities are the U.S., Germany, and the Netherlands, while the top destinations are organizations based in the U.S., Germany, and the U.K. This global footprint underscores the broad appeal of Ivanti systems as a target for cybercriminals.
Ivanti Connect Secure and Pulse Secure VPNs are widely used for enterprise remote access. Their strategic role makes them an attractive target for hackers, particularly as organizations continue to rely on remote work.
While no specific vulnerabilities (CVEs) have been publicly linked to this latest scanning campaign, past incidents show that such reconnaissance is often a harbinger of forthcoming attacks.
History shows that spikes in scanning activity often lead to active exploitation, sometimes before a new vulnerability is even discovered.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!
Gunra Ransomware, has surfaced as a formidable threat in April 2025, targeting Windows systems across…
Cybersecurity firm Sansec has uncovered a sophisticated supply chain attack that has compromised 21 popular…
The financially motivated threat group Venom Spider, also tracked as TA4557, has shifted its focus…
The Russian-based threat group RomCom, also known as Storm-0978, Tropical Scorpius, and Void Rabisu, has…
The Seqrite Labs APT team has uncovered a sophisticated cyber campaign by the Pakistan-linked Transparent…
The LUMMAC.V2 infostealer malware, also known as Lumma or Lummastealer, has emerged as a significant…