

Cybersecurity experts have uncovered how hackers use Cascading Style Sheets (CSS) to deceive spam filters and monitor user behavior.
This sophisticated technique allows malicious actors to remain under the radar while gaining insights into user preferences and actions.
The abuse of CSS for both evasion and tracking poses substantial threats to privacy and security.
Threat actors have developed several methods to exploit CSS for evading detection.
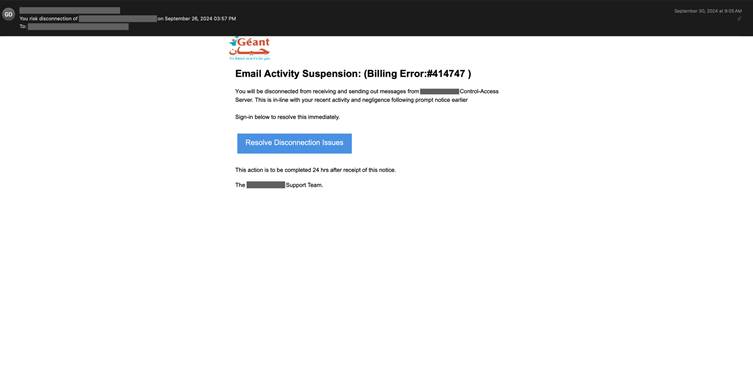
One of these methods involves using CSS properties like text-indent and opacity to conceal content within emails.
This “hidden text salting” technique allows attackers to add irrelevant text or code that is not visible to recipients but can trick spam filters into misclassifying the email as legitimate, as per a report by Talos Intelligence.
For instance, by setting the text-indent property to a large negative value (e.g., -9999px), attackers can move unwanted text far beyond the visible area of the email.
This hidden content can include gibberish characters inserted between legitimate words in the email body, making it difficult for detection engines to identify the true intent of the message.

Additionally, setting the font size to an extremely small value or the text color to transparent ensures that the hidden content remains invisible to human eyes.
Another technique involves using the opacity property to make certain elements completely transparent, thus hiding them from view while maintaining their presence in the email code.
This approach can be used in both the email body and preheader sections to deceive spam filters and make the email appear less suspicious.
Beyond evading filters, CSS is also being used to track users’ actions and preferences. Email clients’ varying support for CSS rules enables attackers to fingerprint recipients’ systems and hardware.
This can include detecting screen sizes, resolutions, and color schemes, providing valuable information that can be used to tailor phishing campaigns or marketing strategies.
An example of this tracking involves using the CSS media at-rule to record when an email is viewed or printed.
By embedding tracking images or URLs that log specific events (e.g., when the email is opened in a particular client), attackers can gather detailed data about user engagement and preferences.
This information can be used to optimize future campaigns or enhance the effectiveness of targeted attacks.
Furthermore, CSS can be used to fingerprint operating systems based on the availability of specific fonts.
For instance, using a font like Segoe UI, which is common in Windows, and a media rule that applies different styles if Helvetica Neue is available (typically found on macOS), attackers can determine which operating system a recipient is using.
This information can be used to tailor malicious content to the recipient’s environment.
To address these security and privacy threats, several mitigation strategies can be employed:
The exploitation of CSS for nefarious purposes underscores the evolving nature of cyber threats.
As attackers continue to innovate, both individuals and organizations must stay informed and implement robust security measures to protect against these sophisticated tactics.
Are you from SOC/DFIR Teams? – Analyse Malware Incidents & get live Access with ANY.RUN -> Start Now for Free.
Verizon Business's 2025 Data Breach Investigations Report (DBIR), released on April 24, 2025, paints a…
A recent cyber espionage campaign by the notorious Lazarus Advanced Persistent Threat (APT) group, tracked…
In a alarming cybersecurity breach uncovered by Cisco Talos in 2023, a critical infrastructure enterprise…
In a startling revelation from Microsoft Threat Intelligence, threat actors are increasingly targeting unsecured Kubernetes…
A recently uncovered cyberattack campaign has brought steganography back into the spotlight, showcasing the creative…
Threat actors exploited a zero-day vulnerability in Ivanti Connect Secure, identified as CVE-2025-0282, to deploy…