

A new highly effective phishing technique targeting Gmail and other services has been gaining popularity during the past year among attackers. Over the past few weeks there have been reports of experienced technical users being hit by this.
This attack is currently being used to target Gmail customers and is also targeting other services.
The way the attack works is that an attacker will send an email to your Gmail account. That email may come from someone you know who has had their account hacked using this technique. It may also include something that looks like an image of an attachment you recognize from the sender.
You click on the image, expecting Gmail to give you a preview of the attachment. Instead, a new tab opens up and you are prompted by Gmail to sign in again. You glance at the location bar and you see accounts.google.com in there. It looks like this….

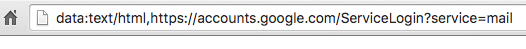
“You are probably thinking you’re too smart to fall for this: It turns out that this attack has caught, or almost caught several technical users who have either tweeted, blogged or commented about it,” Maunder says.
“It is being used right now with a high success rate … this technique can be used to steal credentials from many other platforms with many variations in the basic technique.”
A commenter on Hacker News describes in clear terms what they experienced over the holiday break once they signed in to the fake page:
“The attackers log in to your account immediately once they get the credentials, and they use one of your actual attachments, along with one of your actual subject lines, and send it to people in your contact list.
For example, they went into one student’s account, pulled an attachment with an athletic team practice schedule, generated the screenshot, and then paired that with a subject line that was tangentially related, and emailed it to the other members of the athletic team.”
When you sign in to any service, check the browser location bar and verify the protocol, then verify the hostname. It should look like this in Chrome when signing into Gmail or Google:
Make sure there is nothing before the hostname ‘accounts.google.com’ other than ‘https://’ and the lock symbol. You should also take special note of the green color and lock symbol that appears on the left. If you can’t verify the protocol and verify the hostname, stop and consider what you just clicked on to get to that sign-in page.
Enable two factor authentication if it is available on every service that you use. GMail calls this “2- step verification” and you can find out how to enable it on this page.
Enabling two factor authentication makes it much more difficult for an attacker to sign into a service that you use, even if they manage to steal your password using this technique. Wordfence Founder/CEO Maunder says.
Verizon Business's 2025 Data Breach Investigations Report (DBIR), released on April 24, 2025, paints a…
A recent cyber espionage campaign by the notorious Lazarus Advanced Persistent Threat (APT) group, tracked…
In a alarming cybersecurity breach uncovered by Cisco Talos in 2023, a critical infrastructure enterprise…
In a startling revelation from Microsoft Threat Intelligence, threat actors are increasingly targeting unsecured Kubernetes…
A recently uncovered cyberattack campaign has brought steganography back into the spotlight, showcasing the creative…
Threat actors exploited a zero-day vulnerability in Ivanti Connect Secure, identified as CVE-2025-0282, to deploy…