

Microsoft’s ongoing efforts to enhance user experience in Windows 11 have introduced native support for a variety of new archive formats via the KB5031455 update.
While these changes have streamlined user workflows, they have also inadvertently opened Pandora’s box in the realm of cybersecurity, linking the operating system to potential vulnerabilities stemming from its reliance on libarchive, an open-source library used for handling multiple archive file formats.
Before October 2023, Windows 11 natively supported only ZIP files, categorized as “Compressed (zipped) Folder.”

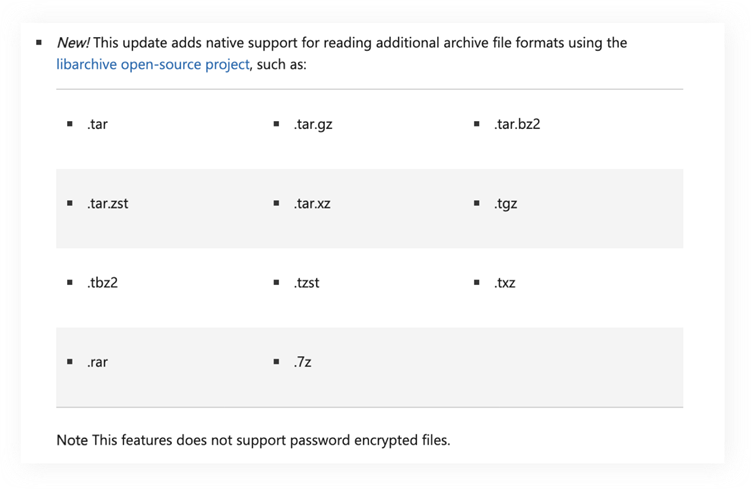
The KB5031455 update expanded this feature to include 11 additional formats, including RAR, 7z, and TAR.
The changes were welcomed by users who no longer needed third-party tools like WinRAR or 7-Zip to handle these formats.
Underneath this user-friendly facade lies a technical shift. File Explorer now uses two distinct mechanisms: zipfldr.dll for handling ZIP files and archiveint.dll, which integrates libarchive, for managing the newly supported formats.
While libarchive is a robust library tested across platforms like Linux, macOS, and BSD, it has introduced significant security concerns.
Libarchive, despite its maturity and extensive fuzz testing through Google’s OSS-Fuzz program, has shown cracks in its armor.
Recent research uncovered several serious security vulnerabilities tied to its use in Windows 11, including those already patched by Microsoft and others that persisted due to delays in addressing them upstream in libarchive.
Key Vulnerabilities Discovered:
Although it required precise user interaction, such as navigating deep archive structures and opening specific files, the exploit underscored poor filename filtering.
By exploiting Windows’ handling of absolute paths in archives, attackers could write temporary files outside their intended directories, potentially enabling data manipulation.
The integration of libarchive has significantly expanded the software’s attack surface.
Researchers noted that, in theory, Windows 11 could support over 91 decillion (10^33) archive format combinations due to libarchive’s ability to chain filters and formats.
While this flexibility theoretically enables broad compatibility, it also dramatically increases the likelihood of unanticipated security flaws.
Despite continuous fuzz testing, libarchive’s oversight of certain file formats and its reliance on CRC checks posed challenges for automated vulnerability detection.
Even after vulnerabilities like CVE-2024-20696 and CVE-2024-20697 were found, a disconnect between Microsoft and the libarchive maintainers led to a “Half-day” scenario, where vulnerabilities patched in Microsoft’s fork of libarchive went unaddressed upstream for months.
The lack of immediate CVE issuance and public awareness further delayed the deployment of critical patches, leaving downstream users and projects vulnerable.
The delay highlights the risks inherent in the fragmented nature of open-source software development when integrated into proprietary systems.
As Windows 11 users enjoy the convenience of handling multiple archive formats directly in File Explorer, it is crucial to remember that such luxury must come with vigilance.
Keeping systems up to date and monitoring emerging vulnerabilities remain essential steps for mitigating risks in an ever-evolving cybersecurity landscape.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free
A new project has exposed a critical attack vector that exploits protocol vulnerabilities to disrupt…
A threat actor known as #LongNight has reportedly put up for sale remote code execution…
Ivanti disclosed two critical vulnerabilities, identified as CVE-2025-4427 and CVE-2025-4428, affecting Ivanti Endpoint Manager Mobile…
Hackers are increasingly targeting macOS users with malicious clones of Ledger Live, the popular application…
The European Union has escalated its response to Russia’s ongoing campaign of hybrid threats, announcing…
Venice.ai has rapidly emerged as a disruptive force in the AI landscape, positioning itself as…