

The Socket Research Team has uncovered a malicious npm package@ton-wallet/create designed to steal sensitive cryptocurrency wallet keys from developers and users in the TON blockchain ecosystem.
TON, originally developed by Telegram, is a growing platform for decentralized applications (dApps), smart contracts, and cryptocurrency transactions.

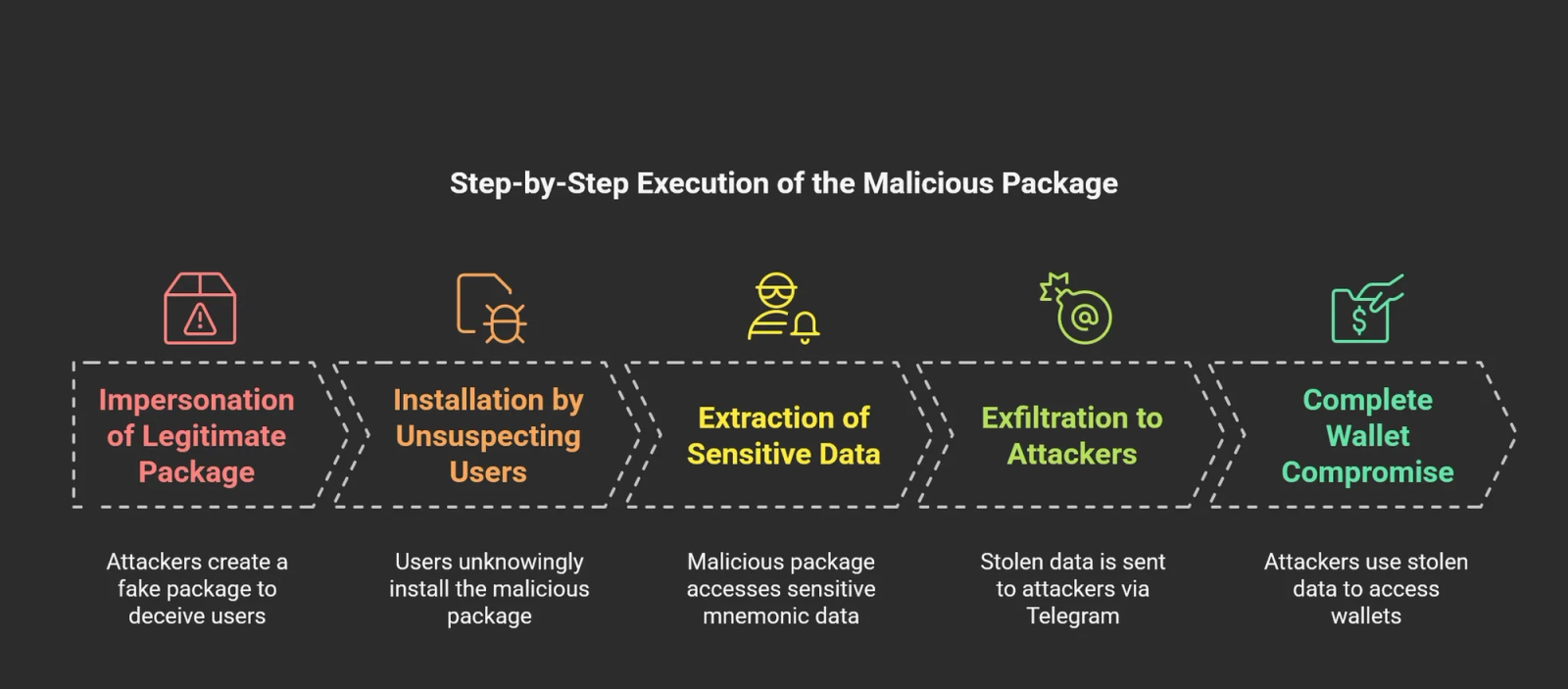
The malicious package impersonated the legitimate @ton/ton package and remained undetected for six months, posing significant risks to the software supply chain.
The legitimate @ton/ton package is widely trusted and boasts over 64,000 weekly downloads, making it a prime target for attackers seeking to exploit its credibility.

.webp)
By mimicking the naming convention of the trusted package, the malicious @ton-wallet/create deceived developers into integrating it into their projects.
Once installed, the package exfiltrated mnemonic phrases critical keys used to access cryptocurrency wallets via an attacker-controlled Telegram bot.
At the core of this attack lies the exploitation of the process.env.MNEMONIC environment variable, a common method for storing sensitive secrets in Node.js applications.
Mnemonic phrases, typically consisting of 12 or 24 words, provide full access to cryptocurrency wallets.
The malicious package silently captured these phrases and transmitted them to a Telegram bot using hardcoded credentials.
The attack script embedded in the package was straightforward yet effective.
It used the node-telegram-bot-api library to send stolen data directly to an attacker’s Telegram chat.
This method allowed attackers to bypass detection mechanisms while maintaining real-time access to compromised wallet keys.
The stolen mnemonics granted attackers full control over users’ digital assets, leading to potential financial losses.
The impact of this supply chain attack extends across multiple groups:
With over one million active users in the TON ecosystem, the scale of this attack underscores the critical need for enhanced security measures in open-source software development.
To counter such threats, developers are urged to adopt proactive security measures:
The Socket Research Team has reported @ton-wallet/create to npm for removal, preventing further exploitation.
This incident serves as a stark reminder of the vulnerabilities inherent in open-source ecosystems and highlights the importance of safeguarding software supply chains against emerging threats.
Free Webinar: Better SOC with Interactive Malware Sandbox for Incident Response, and Threat Hunting - Register Here
NVIDIA has issued an urgent security advisory addressing three high-severity vulnerabilities in its NeMo Framework,…
Cisco has issued a high-severity advisory (cisco-sa-erlang-otp-ssh-xyZZy) warning of a critical remote code execution (RCE)…
Enterprises and managed service providers globally are now facing urgent security concerns following the disclosure…
Security researcher Alessandro Sgreccia (aka "rainpwn") has revealed a set of critical vulnerabilities in Zyxel’s…
A high-severity denial-of-service (DoS) vulnerability in Redis, tracked as CVE-2025-21605, allows unauthenticated attackers to crash servers…
Google’s Mandiant team has released its M-Trends 2025 report, highlighting the increasing sophistication of threat…