

It’s been reported recently that the ModifiedElephant APT Hacker group remains secret for years using advanced sophisticated techniques. And the cybersecurity researchers of SentinelLabs have asserted these specified details regarding the advanced persistent threat (APT) actor group ModifiedElephant.
However, they have been implementing their techniques and conducting different attacks for a decade. The threat actors of this group used tactics that generally allowed it to operate in utmost secrecy.
And all this is being done by the threat actors outwardly connecting the dots of the cybersecurity companies during their attack.
The main objective of this threat group ModifiedElephant is very long-term surveillance. However, this implements a delivery of evidence that is a file that incriminates all the targeted crimes.
That’s why the analysts have done proper research and found that this threat group has targeted hundreds of groups and individuals. This includes:-

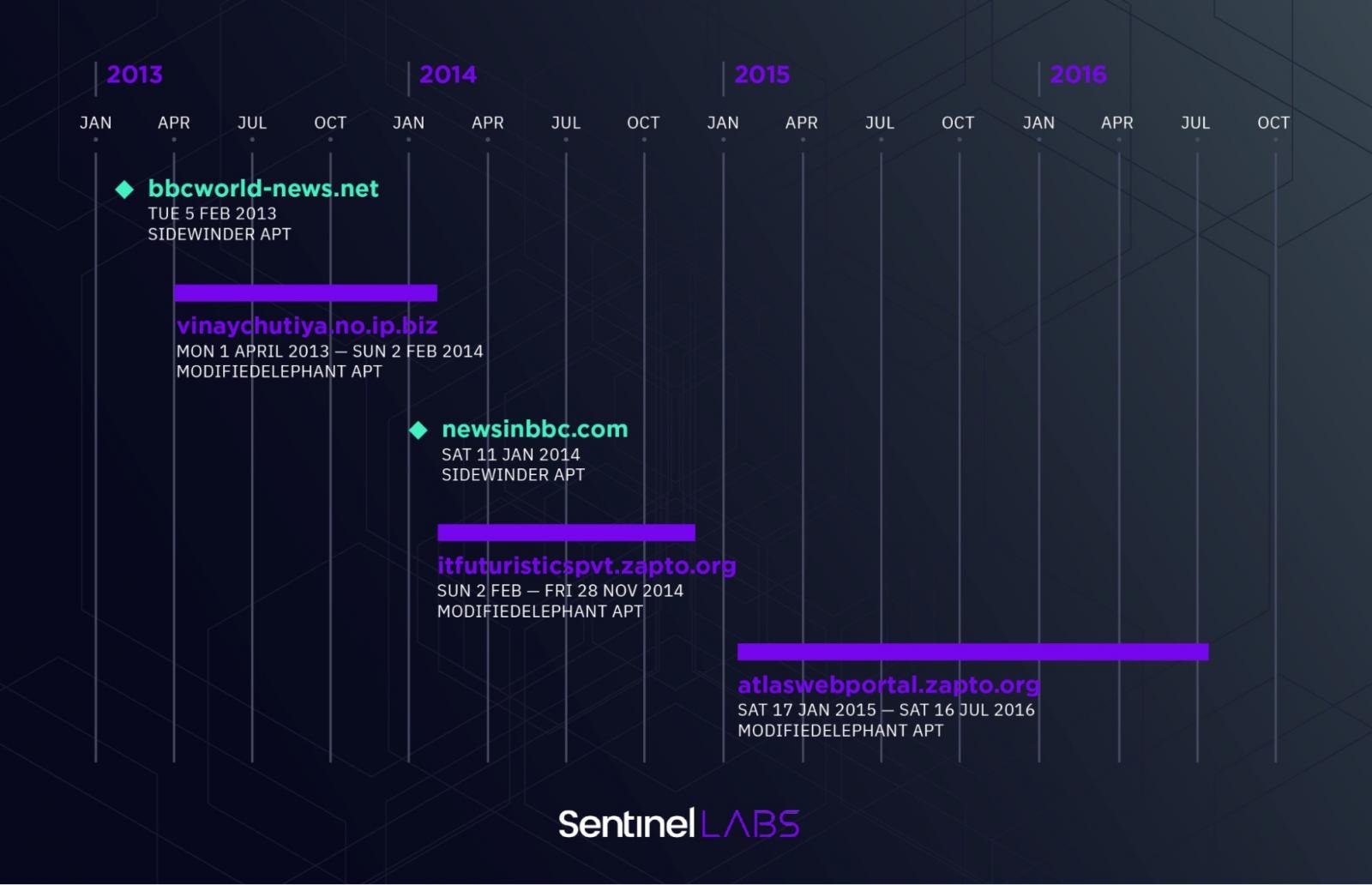
As we said above that this threat group has been conducting several attacks over a decade, and for this reason only we have mentioned some of the campaigns that have been operated as well as conducted by the ModifiedElephant:-
After having a proper investigation, the experts have claimed that they had not found any link that would say that the operators had been using any backdoor.
Due to this, we can say that the threat actors have not used any custom backdoors in any of their operations. And the malware that has been found in the campaigns are:-
However, these Trojans are publicly available and are being used by several threat actors.
While the ModifiedElephant hacker group has been on the radar for a very long time, the security analysts are trying to find all the key links, and therefore they took it as a challenge.
Till now, ModifiedElephant has aligned itself with the Indian State interests, and not only this but it has been noted that there is a correlation between ModifiedElephant attacks and the arrest of individuals in different politically charged cases.
This kind of threat attack is very unsudden, and one must stay alert so that this kind of threat group cannot implement their planned operation.
Moreover, the experts have detected all the possible key links, and they are still searching, as there are still many questions regarding these threat actors and their operations.
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity updates.
Researchers have uncovered early indicators of malicious infrastructure linked to APT34, also known as OilRig,…
A sophisticated phishing campaign has been uncovered by Fortinet’s FortiGuard Labs, targeting Windows users with…
Researchers have exposed a sophisticated cyberattack technique dubbed the "Cookie-Bite Attack," which allows adversaries to…
A critical security vulnerability in Synology’s Network File System (NFS) service, tracked as CVE-2025-1021, has…
In a development for cybersecurity, large language models (LLMs) are being weaponized by malicious actors…
A sophisticated backdoor has been uncovered targeting major organizations across Russia, including government bodies, financial…