

A new and sophisticated phishing scam has been uncovered, leveraging Microsoft 365 domains to trick users into compromising their PayPal accounts.
The attack exploits legitimate-looking sender addresses and URLs, making it harder for victims to recognize the phishing attempt.
Security experts, including Chief Information Security Officers (CISOs), have raised alarms about the growing menace, urging caution and vigilance, shared by Fortinet.

Investigate Real-World Malicious Links, Malware & Phishing Attacks With ANY.RUN – Try for Free
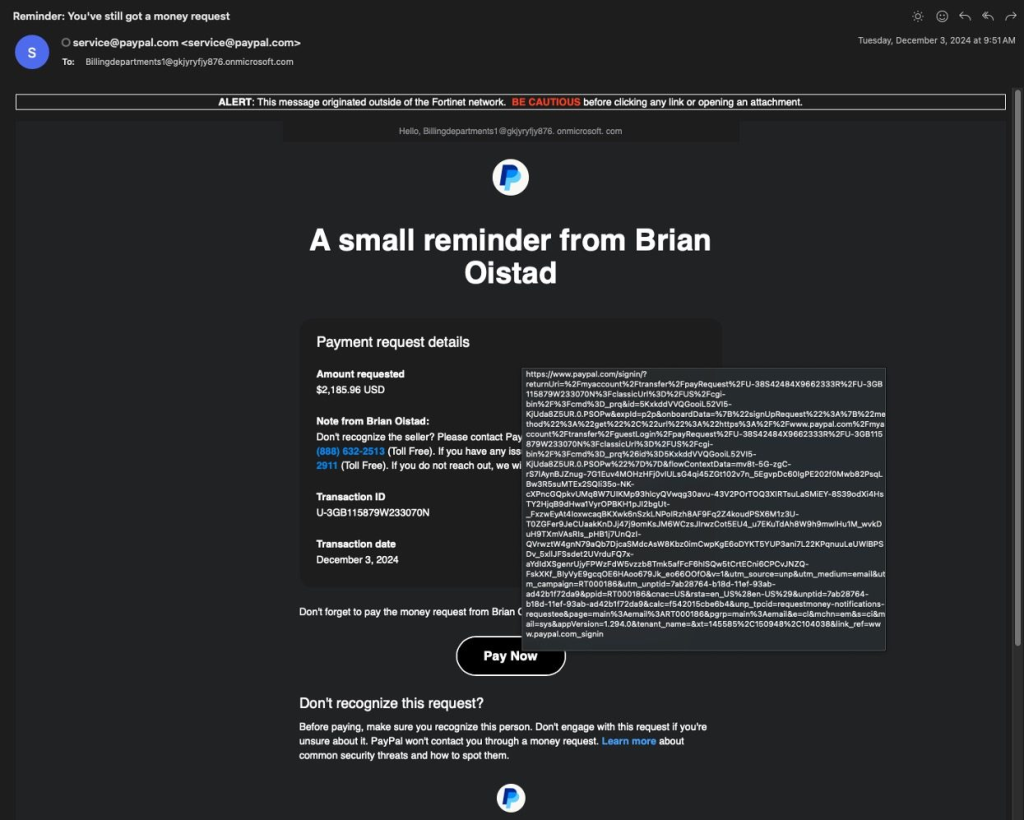
This phishing campaign uses Microsoft 365’s free trial domains to craft authentic-looking email addresses.
Once a scammer registers a trial domain, they set up deceptive distribution lists with obscure addresses resembling legitimate ones.
For example, an email might appear to originate from “Billingdepartments1[@]gkjyryfjy876.onmicrosoft.com,” which at first glance might look credible to unsuspecting users. Here’s the scam’s modus operandi step-by-step:
The cleverness of this attack lies in its leveraging of legitimate technologies. By using free Microsoft 365 test domains, the scammers bypass conventional detection systems.
The distribution list feature further obfuscates the true sender, creating plausible deniability. Even PayPal’s phishing detection instructions would fail to flag this method.
Most dangerously, the phishing email’s sender address and links appear authentic, and the email passes standard security checks. This raises the stakes, as even tech-savvy users might fall for the scam.
Experts urge vigilance when handling payment requests, even from seemingly legitimate sources. Here are some safety recommendations:
As attackers continue to innovate, staying informed and cautious is vital. PayPal users, especially those handling corporate accounts, must prioritize cybersecurity to avoid falling victim to threats like these.
Find this News Interesting! Follow us on Google News, LinkedIn, and X to Get Instant Updates!
Brinker, an innovative narrative intelligence platform dedicated to combating disinformation and influence campaigns, has been…
A recent investigation by cybersecurity researchers has uncovered a large-scale malware campaign leveraging the DeepSeek…
A recent malware campaign has been observed targeting the First Ukrainian International Bank (PUMB), utilizing…
A newly discovered malware, dubbed Trojan.Arcanum, is targeting enthusiasts of tarot, astrology, and other esoteric…
A sophisticated phishing campaign orchestrated by a Russian-speaking threat actor has been uncovered, revealing the…
A sophisticated malware campaign has compromised over 1,500 PostgreSQL servers, leveraging fileless techniques to deploy…