

A recent open-source investigation has uncovered one of the largest exposures of US government data to cyber threats.
More than 150 government database servers are currently exposed to the internet, leaving sensitive personal and national security information at an unprecedented risk of cyberattacks.
The investigation, conducted using data from Shodan, a tool often referred to as the “Google of internet-connected devices,” identified over 2,000 instances of exposed government database servers since early 2025.
These servers, typically hidden behind robust security measures, have been linked to federal agencies using Microsoft’s Azure Gov Cloud, including the Department of Agriculture, Department of Education, Department of Energy, and several others.

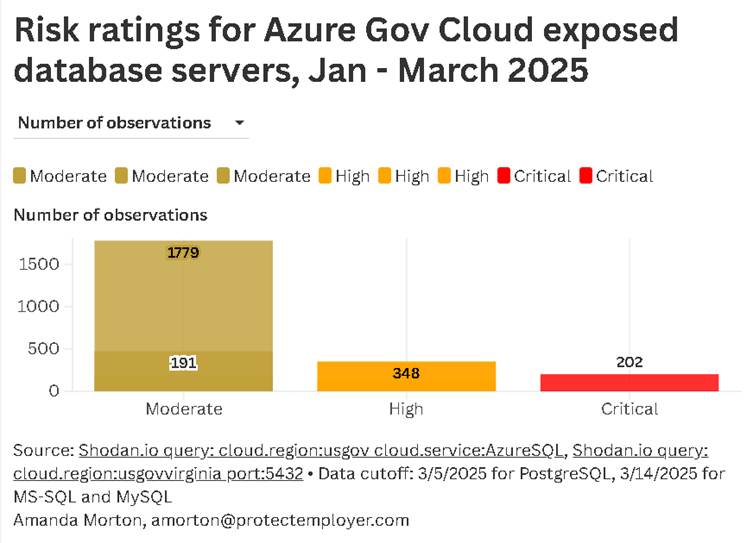
The exposure involves critical database ports (like 1433 for SQL Server, 3306 for MySQL, and 5432 for PostgreSQL) that are directly accessible from the internet, contrary to best practices where such access should be strictly controlled.
This vulnerability not only allows automated scanning tools to detect these servers but also exposes them to constant brute-force attacks and attacks utilizing known exploits.
Even without full access, attackers can gather intelligence for future, more sophisticated breaches.
The data at risk includes Social Security numbers, medical histories, bank account details, tax records, and other potentially damaging personal information.
If compromised, this data could be used in identity theft, financial fraud, or even to deny healthcare to patients. Additionally, sensitive military technology could be stolen, impacting national security and the economy.
Moreover, survivors of domestic violence may face severe personal risks if their addresses are leaked, while critical national infrastructure could be targeted by state-backed ransomware gangs.
Recent events, such as the breach of US telecoms by Chinese intelligence and ransomware attacks by groups like Black Basta, highlight the potential scale of threats.
The report highlights three major findings:
The report suggests that these vulnerabilities may be linked to a rapid data centralization effort by the government, prioritizing speed over security.
It calls for immediate actions, such as Congressional hearings to review security practices and inspector general audits to ensure compliance with federal security standards.
Citizens are urged to contact their representatives and demand greater accountability for data protection.
This issue transcends politics; it’s about safeguarding every American’s privacy and security in a digital world.
The U.S. government is facing an unprecedented cybersecurity crisis, with vital data left exposed and vulnerable to cyber threats.
Immediate remedial action is crucial to prevent what could be one of the most devastating data breaches in U.S. history.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free
A startling discovery by BeyondTrust researchers has unveiled a critical vulnerability in Microsoft Entra ID…
The Cofense Phishing Defense Center has uncovered a highly strategic phishing campaign that leverages Google…
Cybersecurity researchers from Trustwave’s Threat Intelligence Team have uncovered a large-scale phishing campaign orchestrated by…
Cisco Talos has uncovered a series of malicious threats masquerading as legitimate AI tool installers,…
Pure Crypter, a well-known malware-as-a-service (MaaS) loader, has been recognized as a crucial tool for…
A recent discovery by security researchers at BeyondTrust has revealed a critical, yet by-design, security…