

Serious security vulnerabilities have been uncovered in the popular social media and content-sharing app, RedNote, compromising the privacy and security of millions of users globally.
Researchers revealed critical flaws allowing attackers to intercept sensitive user data, access device files, and exploit insecure encryption mechanisms on iOS and Android platforms.
The app’s use of inadequate cryptographic protocols and insecure network practices form the basis of these alarming revelations.
The security flaws were identified by researchers across multiple versions of the RedNote app.
These vulnerabilities affect versions downloaded from app stores, such as the Google Play Store, Apple App Store, Xiaomi Mi Store, and the RedNote website.
Researchers discovered the issues using advanced static and dynamic analysis tools, including Frida, IDA Pro, and Wireshark, to reverse-engineer app components and analyze traffic patterns. Below are the primary findings:
1. Browsing Behavior Observable to Eavesdroppers
Researchers found that user-generated traffic, including image and video file requests, was transmitted over unencrypted HTTP connections instead of HTTPS.

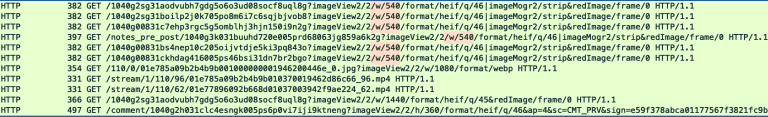
This flaw enables any network eavesdropper to track users’ browsing activity on the app.
Content delivery network (CDN) requests for preview thumbnails and other media files were entirely exposed, compromising user privacy.
2. Remote File Access Vulnerability in Android Versions
One of the more alarming vulnerabilities allows network attackers to read the contents of files stored on Android devices.
This issue is caused by RedNote’s improper encryption and authentication when fetching “cloud configuration files.”
Attackers in a “man-in-the-middle” (MITM) network position can inject and manipulate these configuration files.
Through a proof-of-concept (PoC) attack, researchers demonstrated how injected malicious rules could perform file reading and denial-of-service attacks.
The attack relies on RedNote’s use of an SDK, NEXTDATA (also called Shumei), which identifies rooted or emulated devices.
The SDK decrypts configuration payloads using weak cryptographic implementations that employ static keys.
3. Device Metadata Leaked via Insecure Encryption
Both RedNote’s Android and iOS versions leak sensitive device metadata due to inadequate network encryption.
The app transmits data such as device model, MAC addresses, RAM size, and carrier details using either insecure HTTPS implementations or no encryption at all.
Insecure cryptographic practices, like the use of AES-ECB and improperly padded RSA encryption, open the door for attackers to intercept, modify, or spoof transmitted data.
4. Google Play Store Version Slightly Safer
Interestingly, the RedNote version downloaded from the Google Play Store avoids the remote file reading issue seen in other Android distributions.
Nevertheless, the browsing behavior tracking issue persists across all platforms, making every user vulnerable to eavesdropping.
Researchers disclosed these vulnerabilities by CitizenLab, to the relevant SDK vendors (NEXTDATA and MobTech) in November 2024.
However, as of February 2025, neither vendor has issued a formal response or patch. The lack of acknowledgment raises concerns regarding RedNote’s commitment to user security.
These revelations underscore the importance of adopting robust encryption protocols, ensuring end-to-end HTTPS communication, and validating TLS certificates in app development.
Experts recommend that RedNote users avoid using the app, especially on untrusted networks, until the company addresses these flaws.
The RedNote vulnerabilities highlight the dangers of weak cybersecurity practices in widely used applications. Until developers take necessary actions, users must remain vigilant to protect their data and devices.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free
Gunra Ransomware, has surfaced as a formidable threat in April 2025, targeting Windows systems across…
Cybersecurity firm Sansec has uncovered a sophisticated supply chain attack that has compromised 21 popular…
The financially motivated threat group Venom Spider, also tracked as TA4557, has shifted its focus…
The Russian-based threat group RomCom, also known as Storm-0978, Tropical Scorpius, and Void Rabisu, has…
The Seqrite Labs APT team has uncovered a sophisticated cyber campaign by the Pakistan-linked Transparent…
The LUMMAC.V2 infostealer malware, also known as Lumma or Lummastealer, has emerged as a significant…