

Cybersecurity researchers have uncovered a major flaw in the Windows BitLocker encryption system, allowing attackers to access encrypted data without requiring physical disassembly of the target laptop.
The exploit, named “bitpixie”, demonstrates how attackers can extract the disk encryption key, bypassing Microsoft’s well-known security features such as Secure Boot and the Trusted Platform Module (TPM).
This breakthrough raises significant concerns about the security of modern devices relying on BitLocker for data protection.

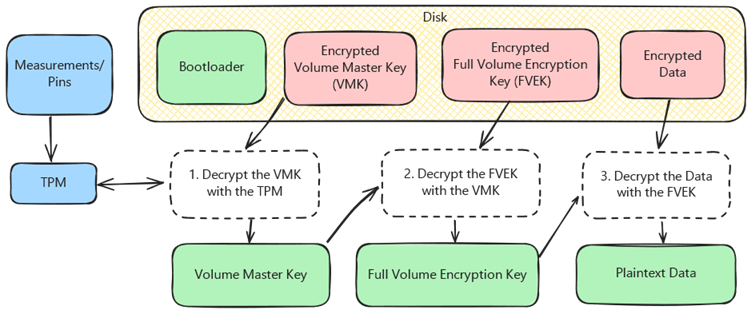
The vulnerability lies in the Windows Boot Manager, a critical component responsible for the decryption of BitLocker-protected disks during the boot process.
According to the detailed analysis by researcher Thomas Weber and others at Neodyme, the bug stems from improper handling of encryption keys during specific boot scenarios.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free
In a recovery boot scenario known as PXE Soft Reboot, encryption keys like the Volume Master Key (VMK) are not adequately wiped from memory, leaving them accessible to attackers under certain conditions.
The exploit leverages the ability to downgrade the Windows Boot Manager to an older, vulnerable version, bypassing modern security updates. By exploiting this flaw, attackers can gain access to the VMK, a critical cryptographic key used to decrypt the entire drive.
Contrary to traditional hardware-based side-channel attacks, this method does not require opening the device or tampering with its internal components. All an attacker needs is:
By simply plugging a LAN cable into the device, booting it into recovery mode, and downgrading the bootloader, attackers can decrypt the drive and access sensitive data — all while leaving the laptop intact and sealed.
1. Bootloader Downgrade
The first step is downgrading the Boot Manager to a version susceptible to the vulnerability.
This can be achieved through PXE booting into a specially crafted environment. Older versions of the bootloader, signed by Microsoft before November 2022, are widely available online or can be extracted from older Windows installations.
2. Fallback Boot
The process involves triggering a failed boot by serving a custom Boot Configuration Data (BCD) file. This configuration forces the bootloader into recovery mode, initiating the PXE reboot flow while leaving the critical VMK in memory.
3. Scanning for the VMK
Once the bootloader fails, attackers can load a separate operating system (such as Linux) and scan the system’s physical memory for the VMK.
Tools like dislocker were employed to locate the encryption key, which becomes accessible due to the improper memory handling in the recovery boot sequence.
4. Decrypting the BitLocker Partition
With the VMK extracted, attackers can mount the encrypted partition and gain full read/write access to the sensitive data stored on the drive. This bypasses all user authentication, effectively rendering the encryption useless.
Devices Affected
The vulnerability affects a wide range of Windows devices running BitLocker with the default “Device Encryption” feature that relies on Secure Boot for disk unsealing.
Systems configured in this way automatically unlock the drive during bootup without requiring user interaction.Key requirements for an attack include:
Notably, Microsoft enabled this default configuration for all Windows 11 devices signed into a Microsoft account with the 24H2 update, expanding the attack’s scope.
Although the vulnerability (CVE-2023-21563) was initially identified in August 2022, Microsoft has struggled to implement a comprehensive fix.
While newer versions of the bootloader have patched the flaw, the design of Secure Boot allows attackers to downgrade to older, vulnerable bootloaders.
This limitation has persisted because Secure Boot does not fully validate the integrity of the bootloader or enforce downgrade protections by default.
Efforts to patch the issue, such as the July 2024 update (KB5025885), introduced additional security features but also created compatibility challenges, forcing a rollback of the fix.
Mitigation Strategies
For end users and organizations relying on BitLocker for data security, researchers recommend taking the following precautions to mitigate the risk:
1. Enable Pre-Boot Authentication
Configuring BitLocker to require a pre-boot PIN or password ensures that additional user input is required to unlock the disk. This approach enhances security but reduces convenience for users.
2. Adjust PCR Configuration
Modifying the Platform Configuration Registers (PCRs) used by the TPM to validate boot integrity can prevent bootloader downgrades. However, this may lead to more frequent BitLocker recovery prompts after system updates.
3. Apply Microsoft’s Update
Applying update KB5025885 is a crucial step. This update introduces new Secure Boot certificates and revokes old ones, preventing the use of vulnerable bootloaders. Note that this process can be technically complex and is not fully automated.
4. Disable PXE Boot
While disabling PXE boot entirely can block this specific attack vector, attackers might still find alternative ways to enable it. A more robust approach involves enforcing physical security measures, such as locking down BIOS/UEFI settings with a password.
The bitpixie exploit serves as an alarming reminder of the trade-offs between convenience and security in modern systems.
While BitLocker remains a valuable feature for protecting data, relying solely on default configurations may provide a false sense of security.
Enterprises, in particular, must act promptly to apply mitigations and educate users about best practices for securing their devices.
Meanwhile, Microsoft faces mounting pressure to enhance the Secure Boot ecosystem to address downgrade vulnerabilities comprehensively.For now, as researcher Thomas Weber aptly concluded, “the necessary downgrade of the bootloader is fairly easy to perform.”
Until security measures evolve, attackers with physical access to devices will continue to find ways to exploit inherent flaws in the system.
Integrating Application Security into Your CI/CD Workflows Using Jenkins & Jira -> Free Webinar
Cisco Talos has uncovered an ongoing cyber campaign by the Gamaredon threat actor group, targeting…
Researchers have uncovered a dangerous new mobile banking Trojan dubbed Crocodilus actively targeting financial institutions…
From WannaCry to the MGM Resorts Hack, ransomware remains one of the most damaging cyberthreats…
Cybersecurity researchers have discovered a sophisticated phishing-as-a-service (PhaaS) platform, dubbed "Morphing Meerkat," that leverages DNS…
A recently identified Remote Access Trojan (RAT) has raised alarms within the cybersecurity community due…
PJobRAT, an Android Remote Access Trojan (RAT) first identified in 2019, has resurfaced in a…