

Cybersecurity analysts have issued a high-priority warning after several incidents revealed active exploitation of SAP NetWeaver, the widely deployed enterprise integration platform.
Attackers have leveraged an unreported 0-day vulnerability to deploy web shells, which give them remote command execution capabilities and persistent backdoor access even on fully patched systems.
The exposure centers around the /developmentserver/metadatauploader endpoint, a feature intended for legitimate SAP application configuration.
ReliaQuest investigators observed attackers uploading “JSP webshells” to publicly accessible directories by abusing this endpoint through specially crafted POST requests.

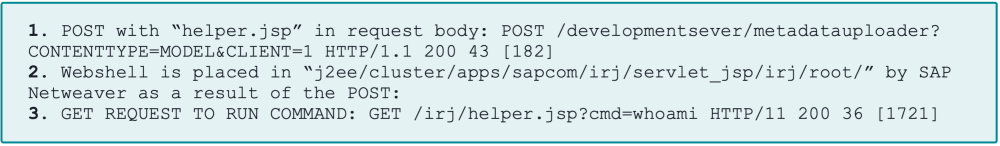
The uploaded files, typically disguised as innocuous names like helper.jsp or cache.jsp, allowed attackers to run arbitrary system commands via simple GET requests.
A critical question arises: is this related to a known Remote File Inclusion (RFI) flaw, such as CVE-2017-9844, which previously allowed remote command execution through Java object serialization? Or is it an entirely new, unreported vulnerability?
Notably, several victim environments had the latest patches for CVE-2017-9844, indicating the likely presence of an undisclosed RFI issue.
This uncertainty dramatically increases the urgency for organizations to step up their defenses.
After gaining access, attackers employed advanced post-exploitation techniques to entrench themselves further:
Investigators believe some attackers may be operating as initial access brokers, obtaining and then selling privileged access to compromised SAP NetWeaver systems to other cybercriminals.
With SAP NetWeaver commonly found in government agencies and global enterprises, these attacks substantially increase the risk of data theft, business disruption, and further systemic compromise.
The rapid deployment of webshells and sophisticated C2 frameworks signals a new wave of threat activity targeting even hardened SAP infrastructures.
Defense Recommendations
Until SAP issues an official advisory or patch, rapid response and vigilant monitoring remain critical to safeguarding against this 0-day exploitation trend.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!
A startling discovery by BeyondTrust researchers has unveiled a critical vulnerability in Microsoft Entra ID…
The Cofense Phishing Defense Center has uncovered a highly strategic phishing campaign that leverages Google…
Cybersecurity researchers from Trustwave’s Threat Intelligence Team have uncovered a large-scale phishing campaign orchestrated by…
Cisco Talos has uncovered a series of malicious threats masquerading as legitimate AI tool installers,…
Pure Crypter, a well-known malware-as-a-service (MaaS) loader, has been recognized as a crucial tool for…
A recent discovery by security researchers at BeyondTrust has revealed a critical, yet by-design, security…