

A sophisticated cyber campaign orchestrated by the Chinese Advanced Persistent Threat (APT) group, Silver Fox, has been uncovered, targeting healthcare services in North America.
The attackers exploited Philips DICOM Viewer software to deploy malicious payloads, including a backdoor remote access tool (RAT), a keylogger, and a crypto miner.
This campaign highlights the evolving tactics of cybercriminals targeting critical sectors like healthcare.
The Silver Fox group employed trojanized versions of MediaViewerLauncher.exe, the executable for Philips DICOM Viewer, as their primary attack vector.
These malicious samples were submitted to VirusTotal from the United States and Canada between December 2024 and January 2025.
The malware cluster demonstrated advanced evasion techniques, including PowerShell exclusions to bypass Windows Defender and encrypted payloads to avoid detection.
The infection process began with reconnaissance activities using native Windows utilities such as ping.exe and ipconfig.exe.
Following this, the malware contacted an Alibaba Cloud bucket to download encrypted payloads disguised as image files.
According to ForeScout, these payloads were decrypted into executable files that included TrueSightKiller (used to disable antivirus software), a backdoor (ValleyRAT), a keylogger, and a crypto miner.

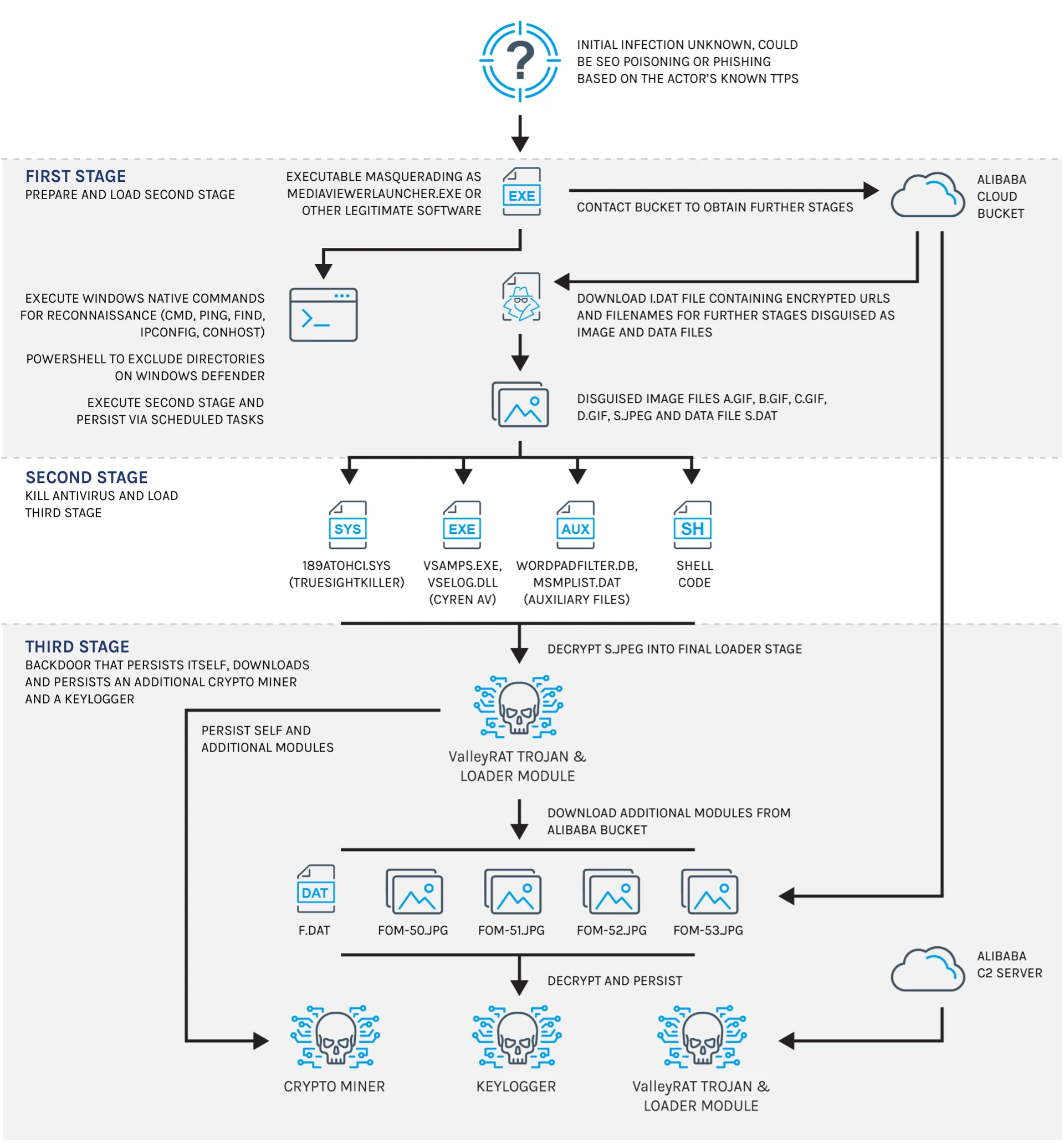
Each stage of the malware was designed to evade detection through obfuscation techniques like API hashing and indirect control flow manipulation.
Once deployed, the ValleyRAT backdoor established communication with a command-and-control (C2) server hosted on Alibaba Cloud.
This allowed attackers to maintain persistent access to compromised systems while simultaneously logging user activity and exploiting system resources for cryptocurrency mining.
Silver Fox’s campaign underscores the vulnerability of healthcare organizations to cyber threats beyond ransomware.
By targeting medical applications like DICOM viewers, which are often used by patients to access their medical images, the attackers exploit potential entry points into healthcare networks.
Infected patient devices brought into hospitals or connected through telehealth services could serve as conduits for further network compromise.
This campaign also marks an evolution in Silver Fox’s tactics.
Historically focused on Chinese-speaking victims and governmental institutions, the group has expanded its scope to include sectors such as finance, e-commerce, and now healthcare.
Their use of advanced techniques like DLL sideloading, process injection, and driver-based antivirus evasion reflects their growing sophistication.
To counter such threats, healthcare delivery organizations (HDOs) should adopt robust cybersecurity measures:
This incident serves as a stark reminder of the need for heightened vigilance in securing healthcare systems against emerging cyber threats.
Collect Threat Intelligence on the Latest Malware and Phishing Attacks with ANY.RUN TI Lookup -> Try for free
DocuSign has emerged as a cornerstone for over 1.6 million customers worldwide, including 95% of…
In a landmark initiative, international cybersecurity agencies have released a comprehensive series of publications to…
A severe security flaw has been identified in the TI WooCommerce Wishlist plugin, a widely…
Microsoft Threat Intelligence Center (MSTIC) has issued a critical warning about a cluster of global…
A recent investigation by security analysts has uncovered a persistent phishing campaign targeting Italian and…
Threat actors have exploited a critical Remote Code Execution (RCE) vulnerability, identified as CVE-2025-32432, in…