

A new extension for Burp Suite has been released, integrating the powerful secret scanning capabilities of TruffleHog.
This innovative integration aims to enhance the detection of live, exploitable credentials within HTTP traffic, making it a valuable tool for security professionals.
In this article, we will delve into the features, usage, and benefits of the TruffleHog Burp Suite extension.
TruffleHog is a widely recognized command-line tool designed to find and verify sensitive information in data streams, including Git repositories.
By integrating TruffleHog with Burp Suite, developers, and security professionals can seamlessly identify and exploit critical secrets embedded in web traffic.
Why Integrate TruffleHog with Burp Suite?
The integration was motivated by the surprising prevalence of hardcoded sensitive information, such as AWS credentials, in web applications.
A recent discovery of over 12,000 live secrets in public web traffic underscored the need for a more robust solution to detect these vulnerabilities.
Burp Suite, known for analyzing HTTP traffic, is the perfect platform to leverage TruffleHog’s capabilities.
Installation
Using the TruffleHog Burp Suite extension involves a straightforward two-step process:
Configuration and Usage
The TruffleHog Burp Suite extension offers several key benefits:
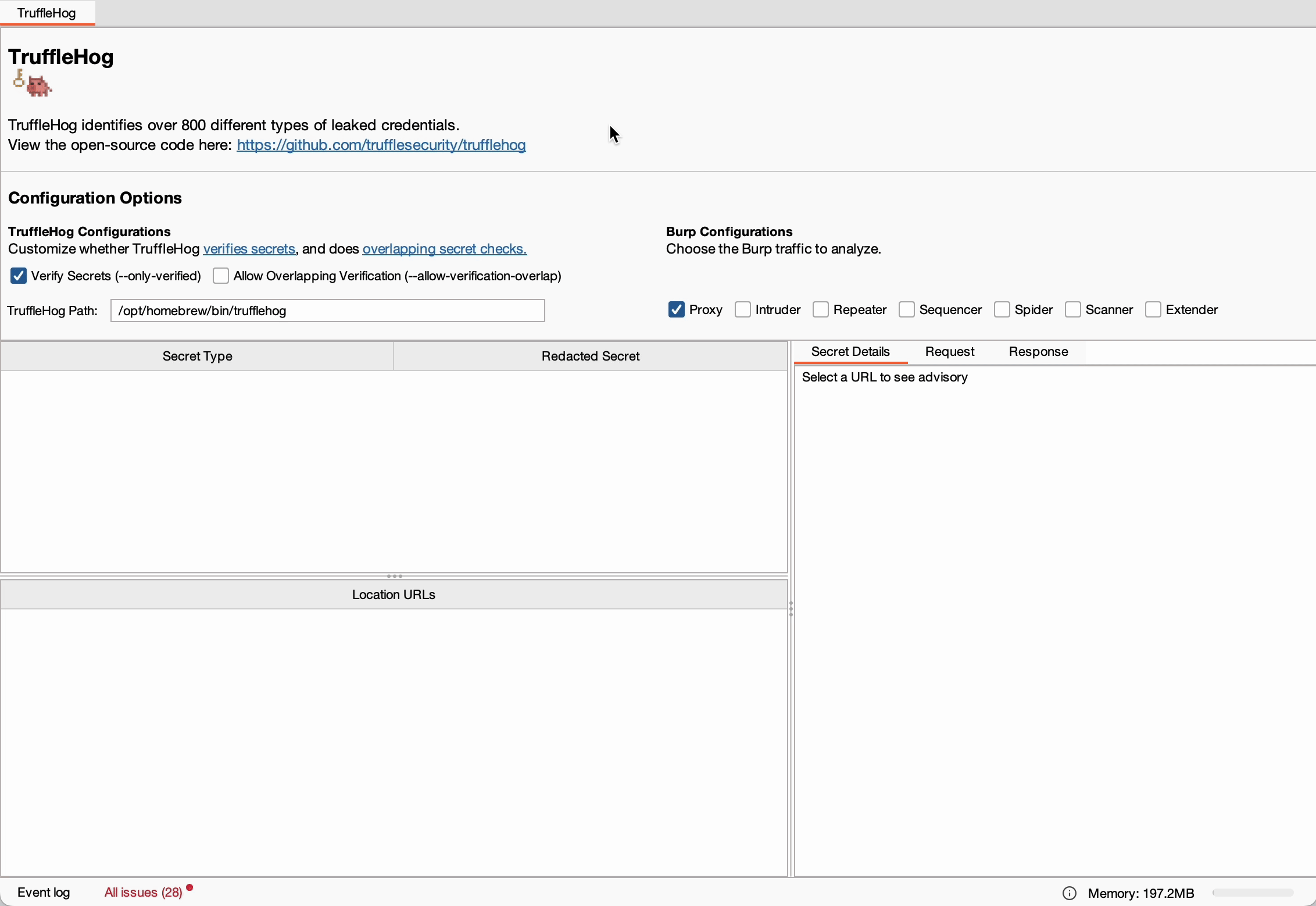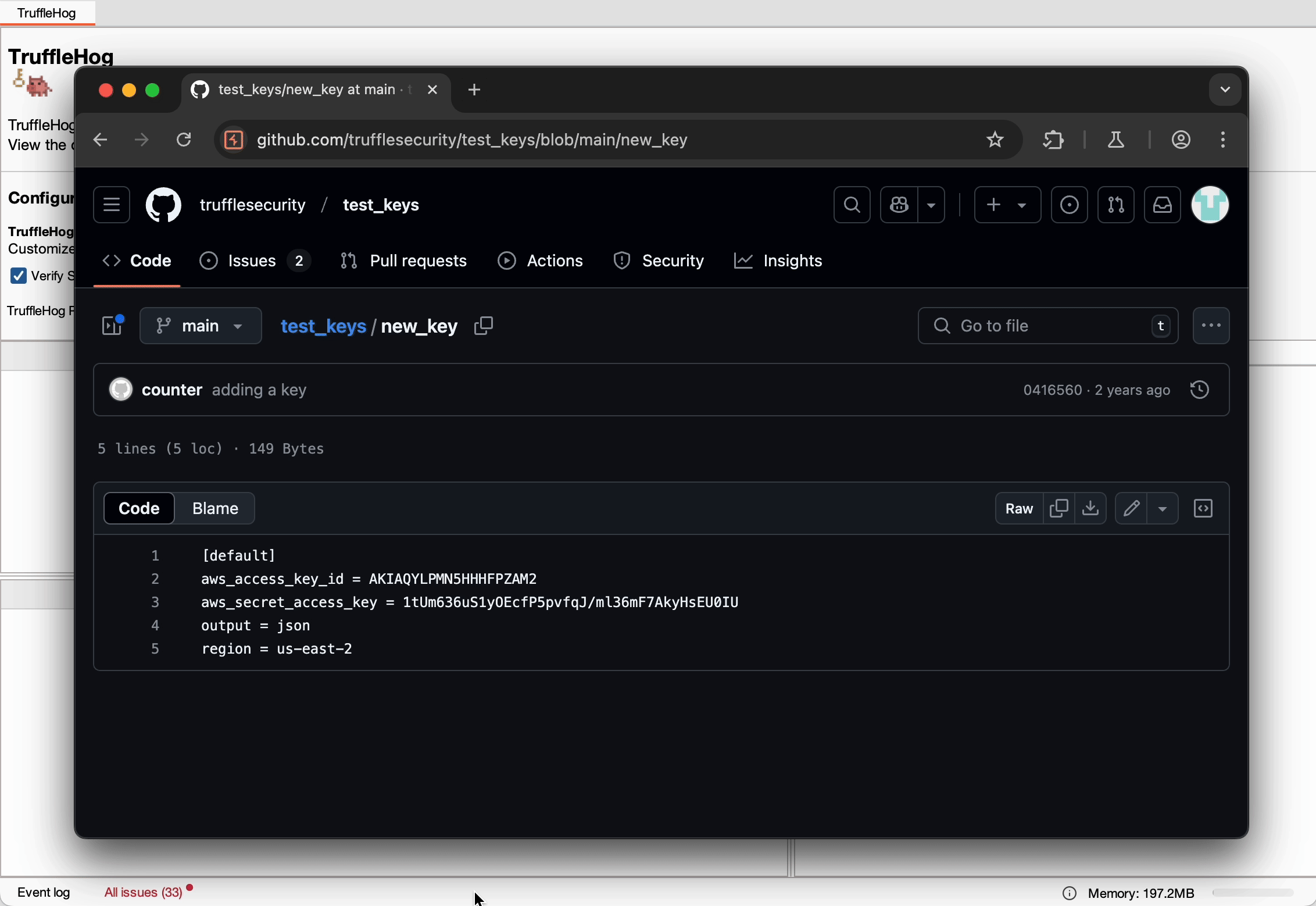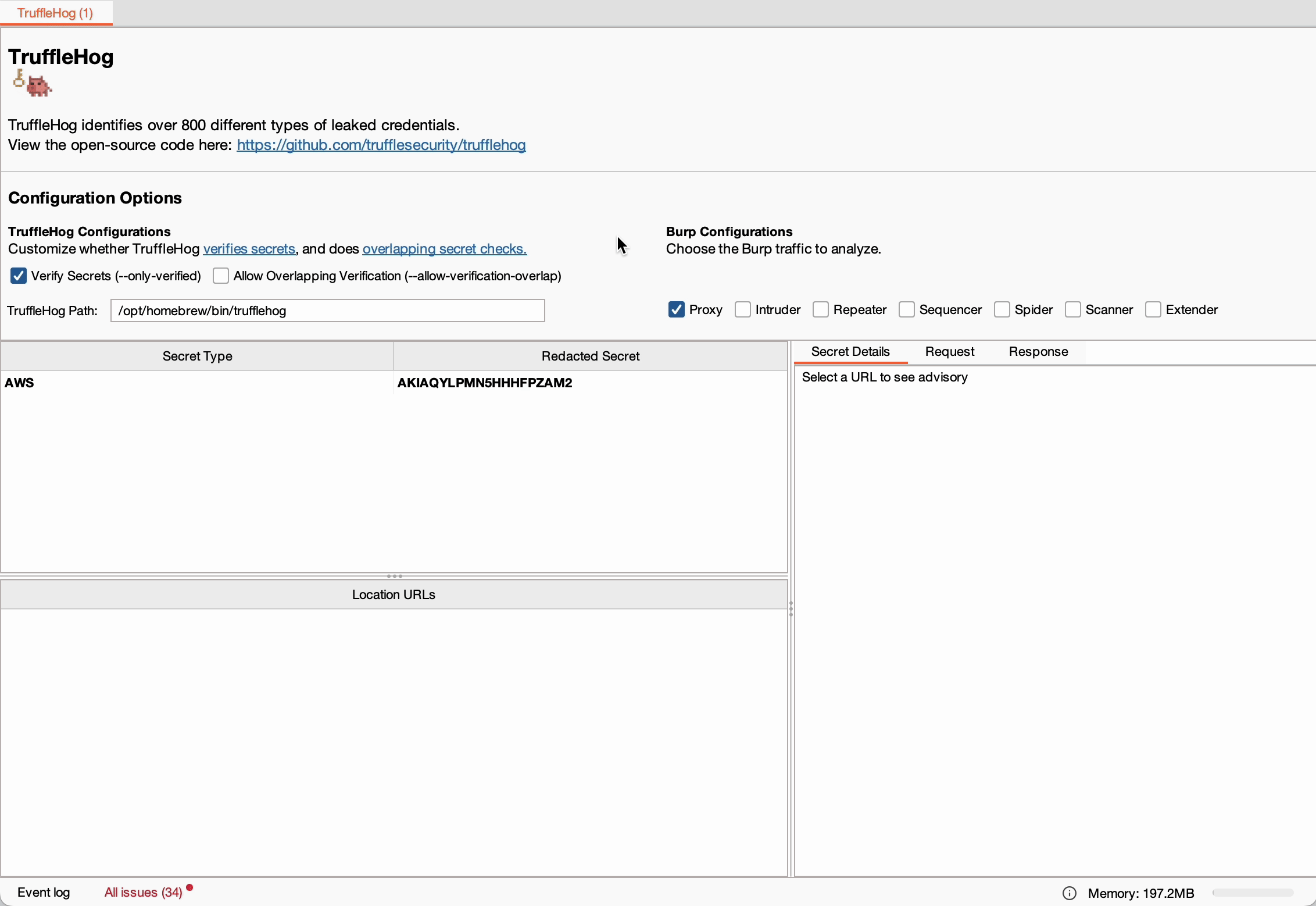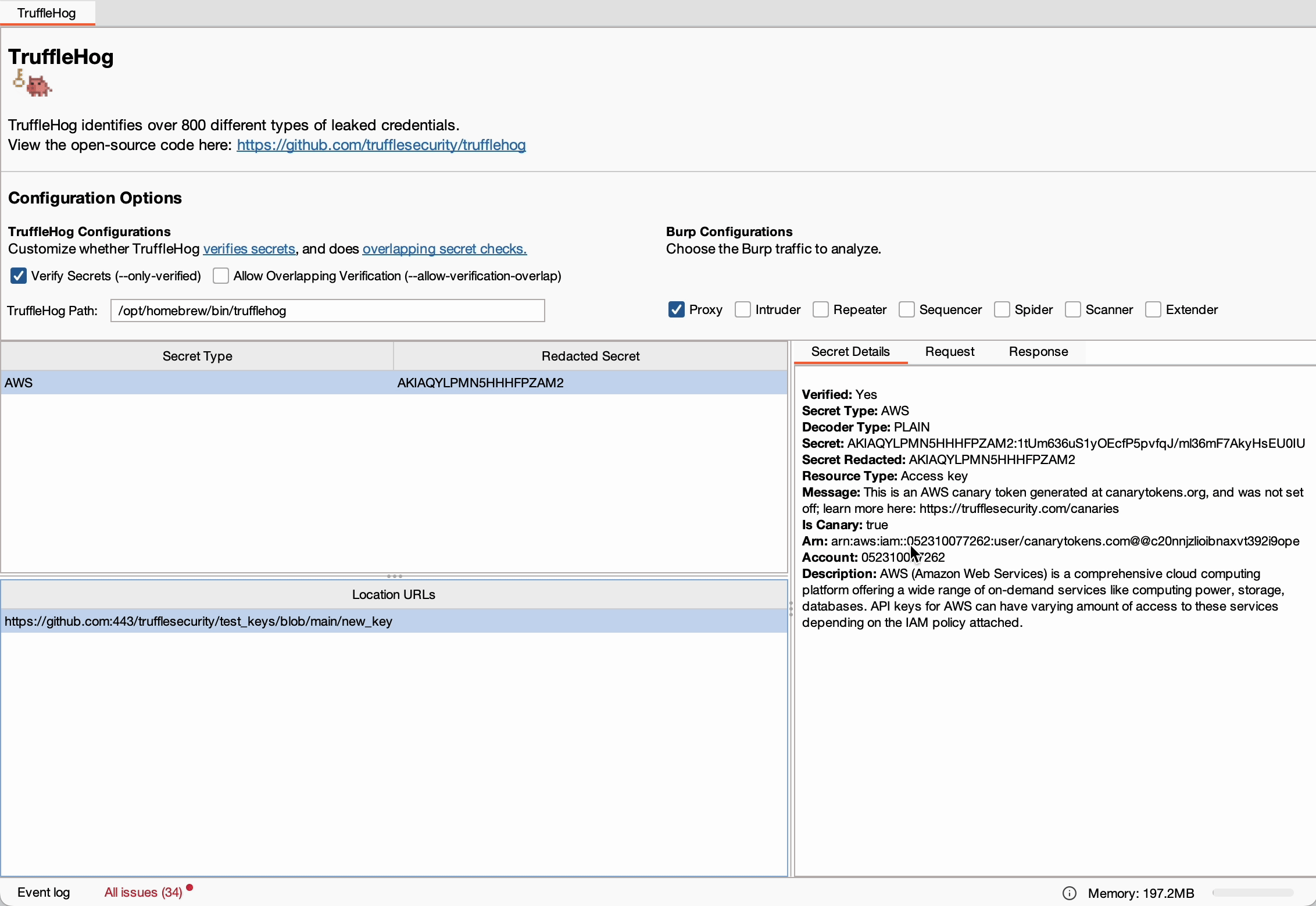
The extension operates by creating a child process that runs TruffleHog on temporary files containing HTTP traffic every ten seconds.
This approach ensures that detected secrets are efficiently reported in the Burp Suite UI without requiring manual intervention.
One notable limitation is the lack of support for scanning WebSocket traffic. This presents an opportunity for future development and could be a rewarding project for those interested.
The release of the TruffleHog Burp Suite extension marks a significant step forward in enhancing web security by providing an accessible tool for detecting and managing sensitive information in HTTP traffic.
By leveraging the strengths of both TruffleHog and Burp Suite, security professionals can now more effectively identify and address potential security vulnerabilities in web applications.
Are you from SOC/DFIR Teams? – Analyse Malware Incidents & get live Access with ANY.RUN -> Start Now for Free.
A new project has exposed a critical attack vector that exploits protocol vulnerabilities to disrupt…
A threat actor known as #LongNight has reportedly put up for sale remote code execution…
Ivanti disclosed two critical vulnerabilities, identified as CVE-2025-4427 and CVE-2025-4428, affecting Ivanti Endpoint Manager Mobile…
Hackers are increasingly targeting macOS users with malicious clones of Ledger Live, the popular application…
The European Union has escalated its response to Russia’s ongoing campaign of hybrid threats, announcing…
Venice.ai has rapidly emerged as a disruptive force in the AI landscape, positioning itself as…