

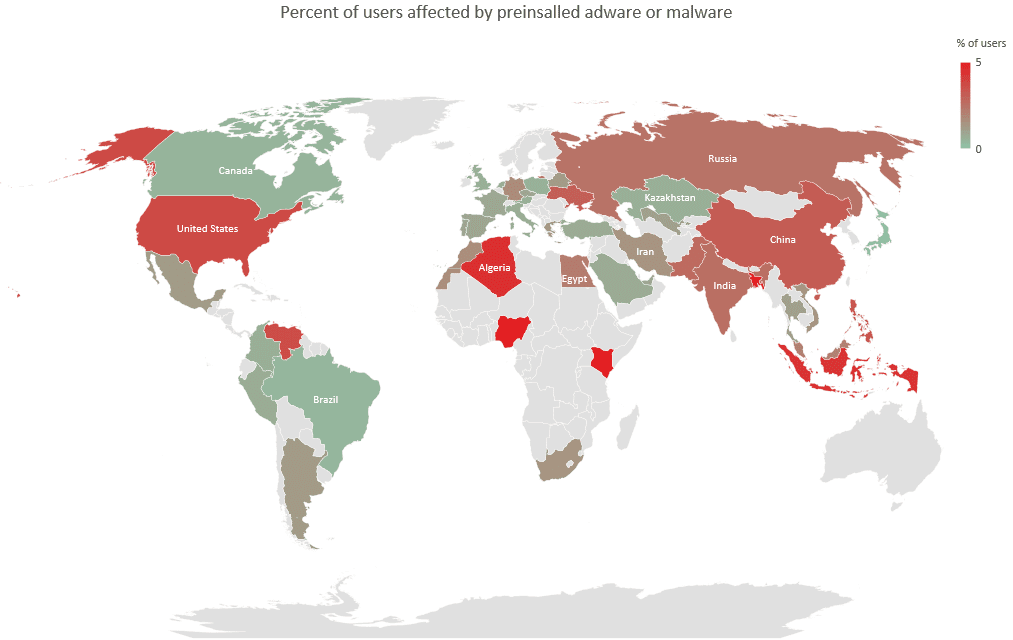
Researchers observed that 14.8% of all Android users attacked by malware or adware still have infection left in the system partition.
The problem is because of smartphones or tablets sold by certain brands in the lower segment contain malicious ad codes embedded in the firmware of the device.
For Android devices, the most common malware is Lezok and Triada. They get directly embedded in key library “libandroid_runtime” that used by every app.
“A system partition infection entails a high level of risk for the users of infected devices, as a security solution cannot access the system directories, meaning it cannot remove the malicious files,” researchers said.
The number of affected users varies between 1 to 5 percent of users with low-cost devices and reaches 27 percent in extreme cases.

The Agent trojan is obfuscated and hides behind the GUI of the system or setting utility and delivers the payload that runs arbitrary files on the device.
Next, the Sivu Trojan which masquerades as an HTMLViewer app has two modules one uses root permission to push notifications and the second one is the backdoor allowing remote control of the smartphone.
The Plague adware is another type that calls itself as Android services and installs apps to show ad notifications.
Trojan Agent.pa mimic as CIT TEST app communicates with C&C server to run apps, open URLs, download and run arbitrary DEX files, install/uninstall apps, show notifications, and start services.
Penguin, Necro, Facmod, Guerrilla, Virtualinst and Secreted, or some other malware that often resides in the system partition.
“Some smartphones contain adware modules pre-installed by the manufacturers themselves. A few vendors openly admit to embedding adware under the hood of their smartphones; some allow it to be disabled, while others do not, describing it as part of their business model to reduce the cost of the device for the end-user,” reads Kaspersky statement.
This research shows that some mobile device sells the phones with built-in ad scripts to maximize the profit which causes inconvenience to the device owners. The pre-installed advertising scripts are hard to remove without damaging the system.
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity and hacking news updates.
Read More
Top 5 Best Adware Removal Tool to Block Annoying Ads in 2019
A startling discovery by BeyondTrust researchers has unveiled a critical vulnerability in Microsoft Entra ID…
The Cofense Phishing Defense Center has uncovered a highly strategic phishing campaign that leverages Google…
Cybersecurity researchers from Trustwave’s Threat Intelligence Team have uncovered a large-scale phishing campaign orchestrated by…
Cisco Talos has uncovered a series of malicious threats masquerading as legitimate AI tool installers,…
Pure Crypter, a well-known malware-as-a-service (MaaS) loader, has been recognized as a crucial tool for…
A recent discovery by security researchers at BeyondTrust has revealed a critical, yet by-design, security…