

A recently disclosed Windows kernel-level vulnerability, identified as CVE-2024-49138, has raised significant security concerns in the cybersecurity community.
Leveraging a buffer overflow vulnerability within the Windows Common Log File System (CLFS), researchers have released a proof-of-concept (PoC) exploit, showcasing the critical risks associated with the flaw.
The vulnerability, which was identified and patched by Microsoft in December 2024 (Patch KB5048685), impacts Windows 11 22H2 and 23H2 systems.
This heap-based buffer overflow resides in functions linked to the Windows kernel driver clfs.sys, specifically in the methods LoadContainerQ() and WriteMetadataBlock().

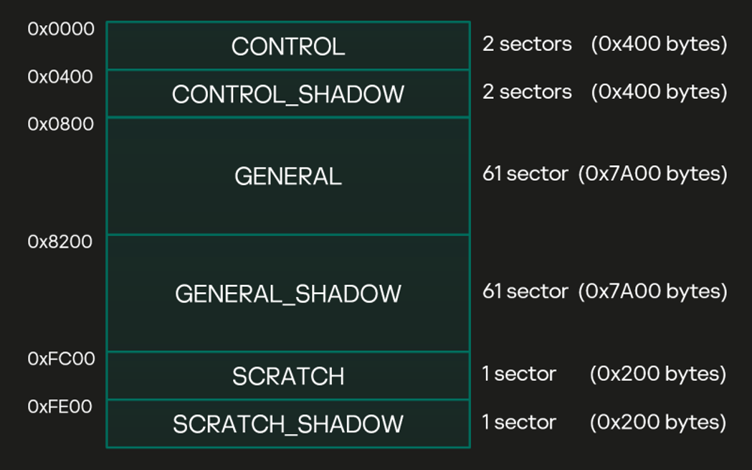
If successfully exploited, the vulnerability grants attackers arbitrary read and write capabilities in ring 0, ultimately allowing them to escalate privileges to the SYSTEM level.
Integrating Application Security into Your CI/CD Workflows Using Jenkins & Jira -> Free Webinar
The Common Log File System (CLFS) is a high-performance subsystem used in Windows for managing log files.
By manipulating metadata structures (specifically the General Metadata Block in memory), attackers can bypass kernel safeguards and execute malicious operations.
Exploiting this vulnerability involves carefully crafted metadata blocks to trigger a mismatch during block encoding and decoding, leading to use-after-free conditions that are weaponized to hijack the execution flow of the Windows kernel, as per a report by Huma Nativa Spa..
The exploit chain specifically targets memory structures such as the CLFS_CONTAINER_CONTEXT and CLFS_LOG_BLOCK_HEADER within the General Metadata Block.
Through intricate manipulations, the PoC exploit removes safety checks that would ordinarily safeguard the integrity of these structures.
By exploiting the handling of metadata block references during processing, attackers can tamper with the kernel pointers to execute arbitrary code.
The PoC exploit, publicly available in a GitHub repository, demonstrates the following attack steps:
This exploit is particularly dangerous for targeted attacks against enterprise environments where attackers could gain complete control over systems.
The exploit uses the following method to tamper metadata:
typedef struct _CLFS_CONTAINER_CONTEXT {
CClfsContainer* pContainer; // Tampered pointer
CLFS_CONTAINER_STATE eState; // Set to deliberately fail flush
ULONG cbPrevOffset;
ULONG cbNextOffset;
} CLFS_CONTAINER_CONTEXT, *PCLFS_CONTAINER_CONTEXT;
containerContext->pContainer = (CClfsContainer*)0x2100000;
// Fake pointer used for kernel hijack
containerContext->eState = 1; // Force error in FlushImage()Additionally, the PoC uses this Python snippet to calculate CRC32 checksums for metadata tampering:
import binascii
def calculate_crc32(file_path):
with open(file_path, "rb") as f:
data = f.read()
checksum = binascii.crc32(data) & 0xFFFFFFFF
print(f"CRC32: {checksum:08x}")Microsoft’s patch (KB5048685), released in December 2024, addresses the flaw by strengthening safety checks in the CLFS methods LoadContainerQ() and WriteMetadataBlock().
The update ensures that improperly processed blocks no longer expose the kernel to memory corruption. Users and organizations that have not yet applied the patch are strongly advised to do so promptly.
For additional protection, organizations can:
With the PoC exploit for CVE-2024-49138 now accessible to the public, Windows systems remain an attractive target for threat actors.
Organizations must adopt a proactive approach to address this vulnerability by applying Microsoft’s patch and fortifying their defenses against kernel-level attacks.
Collect Threat Intelligence with TI Lookup to improve your company’s security - Get 50 Free Request
Verizon Business's 2025 Data Breach Investigations Report (DBIR), released on April 24, 2025, paints a…
A recent cyber espionage campaign by the notorious Lazarus Advanced Persistent Threat (APT) group, tracked…
In a alarming cybersecurity breach uncovered by Cisco Talos in 2023, a critical infrastructure enterprise…
In a startling revelation from Microsoft Threat Intelligence, threat actors are increasingly targeting unsecured Kubernetes…
A recently uncovered cyberattack campaign has brought steganography back into the spotlight, showcasing the creative…
Threat actors exploited a zero-day vulnerability in Ivanti Connect Secure, identified as CVE-2025-0282, to deploy…