

Multiple Xerox printer models, including EC80xx, AltaLink, VersaLink, and WorkCentre, have been identified as vulnerable to an authenticated remote code execution (RCE) attack.
This vulnerability tracked as CVE-2024-6333, poses a significant risk, fully allowing attackers with administrative web credentials to compromise affected devices with root privileges.
Timo Longin from SEC Consult’s Vienna office and Tamas Jos from the Zurich office discovered the vulnerability. It enables an attacker to execute arbitrary commands on the printer’s operating system.
The flaw lies in the “Network Troubleshooting” menu of the web interface, which uses the tcpdump tool. Insufficient input validation allows attackers to inject operating system commands into the tcpdump command string by manipulating the IPv4 address value.
National Cybersecurity Awareness Month Cyber Challenges – Test your Skills Now

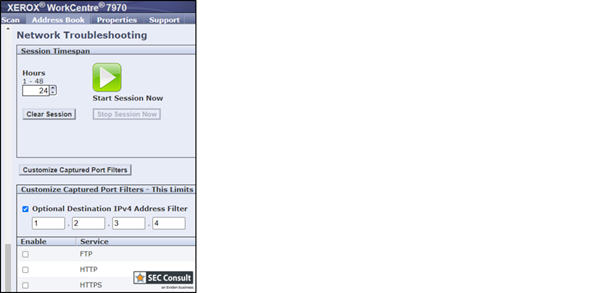
For instance, by setting the IPv4 address to “0.0.0.0$(bash $TMP~cmd)”, commands stored in “/tmp/~cmd” can be executed when initiating a network troubleshooting session.
This exploit can be further leveraged to establish a reverse shell, granting attackers full access to the printer’s system.
The vulnerability affects several Xerox printer models. Specifically those not updated to the latest firmware versions.
Xerox WorkCentre 7970 (073.200.167.09610) and WorkCentre 7855 (073.040.167.09610) were among the initially tested models found vulnerable.
SEC Consult has urged Xerox to address this critical security issue promptly. Customers are advised to install the latest updates and review Xerox’s security note XRX24-015 for detailed guidance on mitigating this vulnerability.
Additionally, SEC Consult recommends a comprehensive security review of Xerox products to identify and resolve potential further security issues.
Xerox, a leader in office and production print technology with a growing presence in digital and IT services, has emphasized its commitment to redefining workplace experiences and empowering client success through innovative solutions.
Free Webinar on How to Protect Small Businesses Against Advanced Cyberthreats -> Watch Here
Cybersecurity in Japan has hit a new low as the Financial Services Agency (FSA) reports…
The Federal Bureau of Investigation (FBI) has issued a warning regarding an emerging scam where…
The Cybersecurity and Infrastructure Security Agency (CISA) has alerted its threat hunting teams to immediately…
A critical remote code execution (RCE) vulnerability in Erlang/OTP’s SSH implementation (CVE-2025-32433) has now entered…
A newly discovered vulnerability in the Windows Update Stack, tracked as CVE-2025-21204, has sent shockwaves…
Cybersecurity researchers have uncovered a sprawling ad-fraud operation exploiting WordPress plugins to trigger over 1.4…