

Firefox Starts rolling out the DNS over HTTPS by default for U.S users to bring fully encrypted browsing experience, and the rollout continues over the next few weeks.
The processing of rolling out takes a little longer time to ensure that no major issues are discovered as this new protocol when users experience this feature in Firefox.
Current DNS systems are leaving billion of users vulnerable since the internet is not encrypted, and it allows ISP’s and law enforcement agencies to spy your browsing activities due to unencrypted DNS queries.
By Implementing DNS over HTTPS, DNS traffic will be fully encrypted from clients (browsers) to resolvers through HTTPS, and it never lets anyone intercepted or tampered the browsing activities and spying on the network.
DNS over HTTPS also helps hide your browsing history from attackers on the network, helps prevent data collection by third parties on the network that ties your computer to websites you visit.
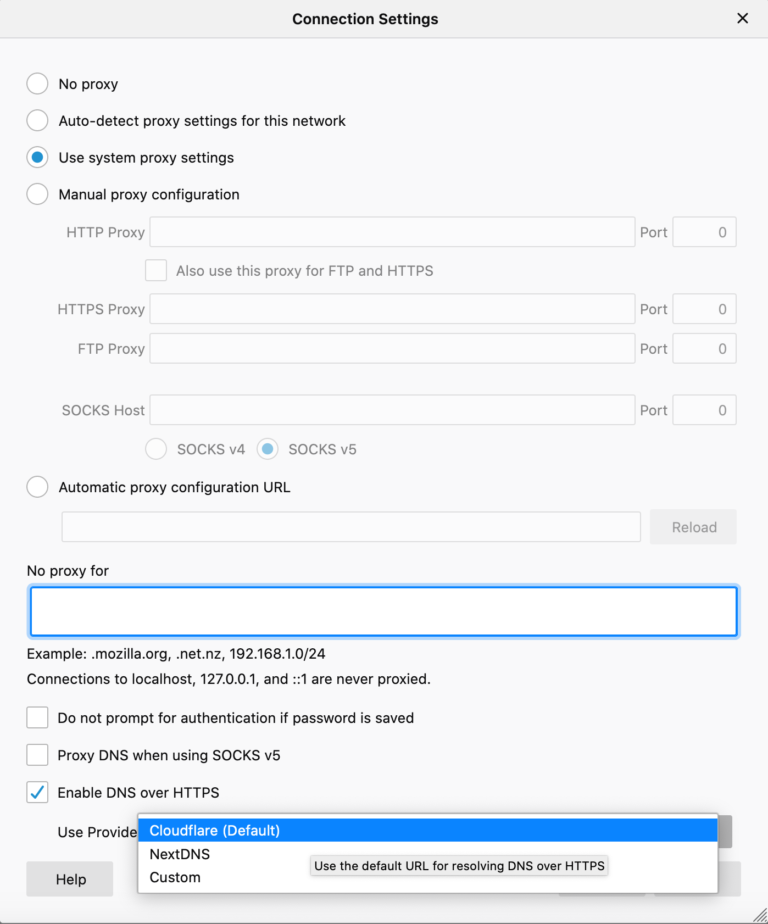
Currently, Firefox brings DNS over HTTPS by Default only for US users. But outside of the U.S users can enable this feature manually by enable the following settings.
Settings -> General – > Network Setting (Scroll down to bottom) -> Enable DNS over HTTPS.
In this setting, you can enable DNS over HTTPS by clicking a checkbox and By default, this change will send your encrypted DNS requests to Cloudflare.

“We continue to explore enabling DoH in other regions and are working to add more providers as trusted resolvers to our program. DoH is just one of the many privacy protections you can expect to see from us in 2020.” Firefox Said.
Mozilla Recently added NextDNS in Firefox 73 update along with Cloudflare as an additional provider with DNS over HTTPS that provides an encryption connection for every DNS request from users.
Follow us on Twitter, Linkedin, Facebook for Daily cyber security & hacking news updates.
NVIDIA has issued an urgent security advisory addressing three high-severity vulnerabilities in its NeMo Framework,…
Cisco has issued a high-severity advisory (cisco-sa-erlang-otp-ssh-xyZZy) warning of a critical remote code execution (RCE)…
Enterprises and managed service providers globally are now facing urgent security concerns following the disclosure…
Security researcher Alessandro Sgreccia (aka "rainpwn") has revealed a set of critical vulnerabilities in Zyxel’s…
A high-severity denial-of-service (DoS) vulnerability in Redis, tracked as CVE-2025-21605, allows unauthenticated attackers to crash servers…
Google’s Mandiant team has released its M-Trends 2025 report, highlighting the increasing sophistication of threat…