

Zoom announced Two-Factor Authentication (2FA) for all users that let admins and organizations prevent security breaches & data thefts.
The two factor authentication (2fa) brings an additional security layer to the authentication process, blocking attackers from taking control of meetings by guessing the password or using compromised credentials.
“With Zoom’s 2FA, users have the option to use authentication apps that support Time-Based One-Time Password (TOTP) protocol (such as Google Authenticator, Microsoft Authenticator, and FreeOTP), or have Zoom send a code via SMS or phone call, as the second factor of the account authentication process,” Zoom explained in an announcement published today.
Zoom offers a range of authentication methods such as SAML, OAuth, and/or password-based authentication, which can be individually enabled or disabled for an account.

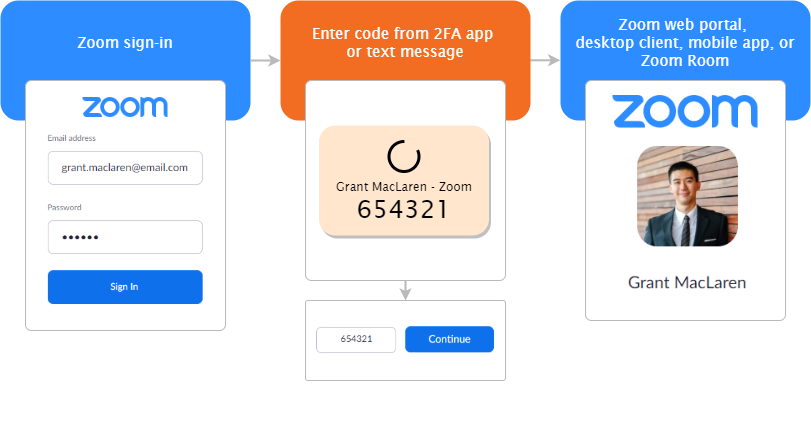
To enable Zoom’s 2FA at the account-level for password-based authentication, account admins should take the following steps:
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity, and hacking news updates.
Also Read
A New Zoom URL Flaw Let Hackers Mimic Organization’s Invitation Link
Zoom 0day Vulnerability Let Remote Attacker to Execute Arbitrary Code on Victim’s Computer
New Zoom Flaw Let Attackers to Hack into the Systems of Participants via Chat Messages
Microsoft Teams users across the globe are experiencing significant disruptions in file-sharing capabilities due to…
Cloud computing has transformed the way organizations operate, offering unprecedented scalability, flexibility, and cost savings.…
Security awareness has become a critical component of organizational defense strategies, particularly as companies adopt…
Security researchers have unveiled a new malware process injection technique dubbed "Waiting Thread Hijacking" (WTH),…
The global regulatory landscape for cybersecurity is undergoing a seismic shift, with the European Union’s…
A sophisticated new malware suite targeting macOS, dubbed "PasivRobber," has been discovered by security researchers.…