

Researchers have uncovered a dangerous new mobile banking Trojan dubbed Crocodilus actively targeting financial institutions and cryptocurrency platforms.
The malware employs advanced techniques like remote device control, stealthy overlays, and social engineering to steal sensitive data, marking a significant escalation in mobile threat sophistication.
Early campaigns focus on banks in Spain and Turkey, but experts warn of imminent global expansion as the malware evolves.
Crocodilus distinguishes itself from older banking Trojans like Anatsa or Octo by incorporating “hidden” remote control features from its inception.
Once installed via a dropper that bypasses Android 13+ security, the malware abuses Accessibility Services to monitor device activity and deploy malicious overlays.

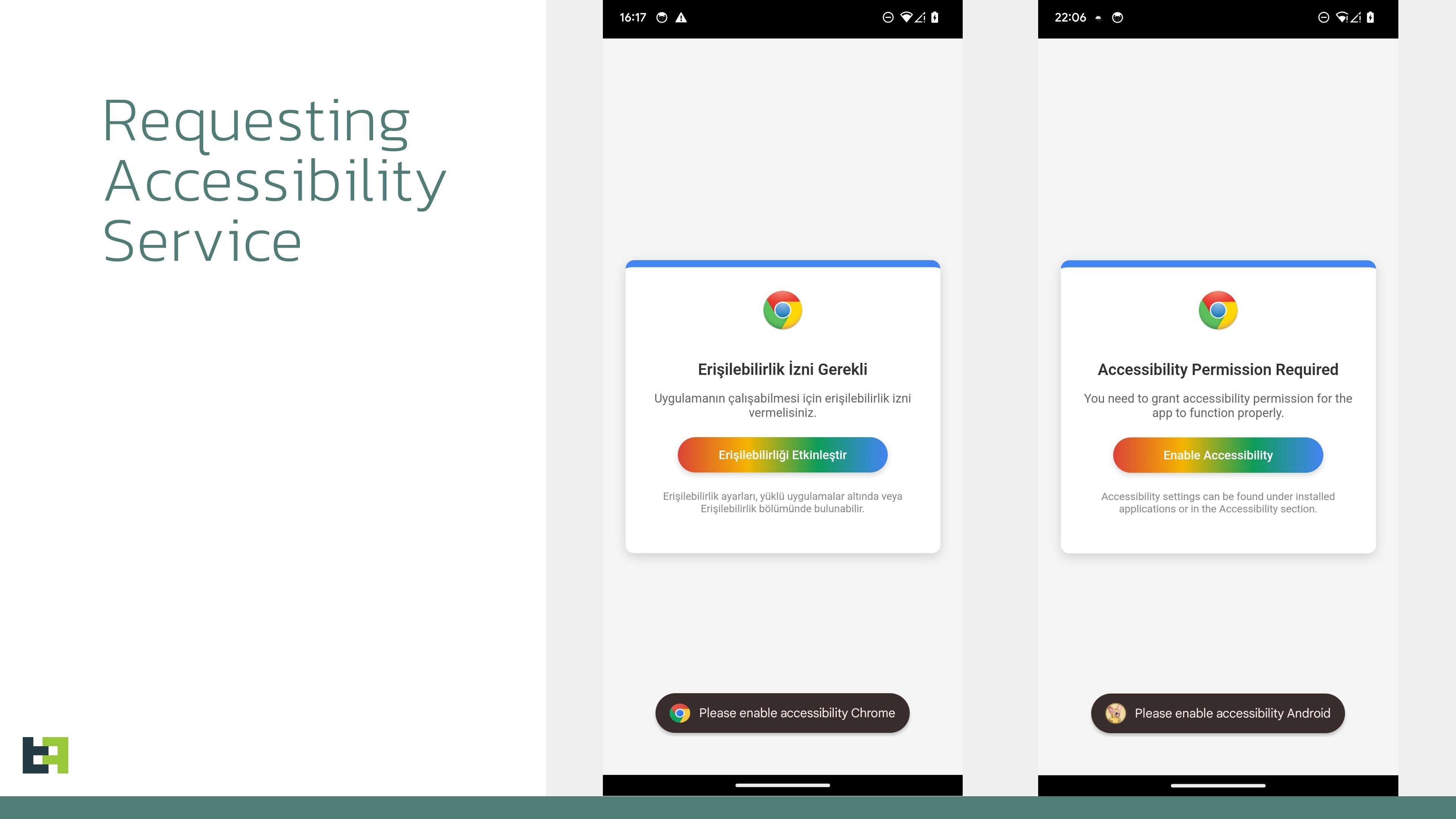
These overlays mimic legitimate banking apps, tricking users into entering credentials, which are harvested in real time.
A novel “black screen overlay” conceals fraudulent transactions by masking the device screen while muting audio, ensuring victims remain unaware of unauthorized activities.
Crocodilus also uses Accessibility Logging a superset of traditional keylogging to capture every text change and UI element displayed, including one-time passwords (OTPs) from apps like Google Authenticator. This enables attackers to bypass multi-factor authentication seamlessly.
Evidence within Crocodilus’ code points to Turkish-speaking developers, with debug messages and tags like “sybupdate” suggesting potential links to “sybra”—a threat actor previously linked to Ermac, Hook, and Octo malware variants.
However, researchers caution that “sybra” could be a customer testing Crocodilus rather than its creator, highlighting the malware’s likely availability in underground markets.
The Trojan’s infrastructure already supports dynamic targeting, allowing operators to push updated overlay templates and app target lists via its C2 server.
Early targets include major Spanish banks, Turkish financial apps, and cryptocurrency wallets like Bitcoin Wallet and Trust Wallet.
ThreatFabric anticipates rapid diversification of targets as Crocodilus gains traction among cybercriminals.
In a devious twist, Crocodilus manipulates cryptocurrency users into voluntarily revealing wallet recovery phrases.
After stealing a wallet’s PIN via an overlay, the malware displays a fake warning: “Back up your wallet key in the settings within 12 hours. Otherwise, the app will be reset…”
Panicked victims then navigate to their seed phrase, which Accessibility Logger captures and transmits to attackers, which grants full control over wallets, enabling instant asset theft.
According to the Report, Crocodilus’ rapid maturation underscores the inadequacy of traditional antivirus tools against modern banking Trojans.
ThreatFabric urges financial institutions to adopt behavior-based detection and device risk profiling to identify compromised devices.
Users are advised to avoid sideloading apps, scrutinize app permissions, and distrust urgent security warnings without verification.
As mobile threats grow more sophisticated, the battle against fraud increasingly hinges on disrupting the social engineering tactics that make tools like Crocodilus devastatingly effective.
Find this News Interesting! Follow us on Google News, LinkedIn, and X to Get Instant Updates!
The eSentire’s Threat Response Unit (TRU) in early March 2025, a sophisticated cyberattack leveraging SocGholish…
The NSFOCUS Fuying Laboratory’s global threat hunting system identified 19 sophisticated Advanced Persistent Threat (APT)…
The FBI’s Internet Crime Complaint Center (IC3) has reported a record-breaking loss of $16.6 billion…
Cybersecurity researchers from The DFIR Report’s Threat Intel Group uncovered an open directory hosted at…
A newly analyzed Python-based Remote Access Trojan (RAT) has emerged as a significant cybersecurity threat,…
A multi-stage carding attack has been uncovered targeting a Magento eCommerce website running an outdated…