Microsoft has introduced “Administrator Protection” (AP), a sophisticated security feature aimed at elevating Windows operating system security by redefining how administrative privileges are managed and reducing the risk of privilege escalation attacks.
Detailed in its latest technical blog post, this feature marks a pivotal step in advancing user protection and mitigating vulnerabilities rooted in legacy designs.
Key Principles of Administrator Protection
Administrator Protection is built on five foundational principles designed to tighten security boundaries while maintaining usability.
It enforces the Principle of Least Privilege, ensures administrative privileges persist only for active tasks, and establishes strict separation between elevated and non-elevated user contexts.
Additionally, elevation actions must be deliberate, and applications can now obtain more granular, task-specific elevated privileges rather than relying on broad, upfront elevation models common in User Account Control (UAC).

Among the transformative changes, System Managed Administrator Accounts (SMAA) play a central role.
These local administrator accounts are dynamically linked to standard user accounts, ensuring administrative privileges are accessed securely.
SMAAs are created as password-less accounts with strict logon constraints, leveraging robust process validations and allowlists to prevent unauthorized access.
Addressing Legacy Vulnerabilities
Microsoft’s approach directly addresses long-standing vulnerabilities with the previous split-token administrator model.
Historically, issues like registry and file system exploitation enabled attackers to elevate privileges, bypassing UAC mechanisms.
Classic attacks, such as leveraging the Event Viewer’s registry keys or exploiting Task Scheduler’s environment variables, are now rendered ineffective due to the decoupling of user profiles and the removal of shared registry hives between standard and elevated contexts.
Furthermore, Administrator Protection discontinues auto-elevation introduced in Windows 7, which had inadvertently expanded the attack surface.
The removal of auto-elevation mitigates 92 auto-elevating COM interfaces, 11 DLL hijacking risks, and 23 auto-elevating apps.
Despite the trade-off in user convenience, this shift substantially reduces the risk of privilege escalation by requiring explicit consent through Windows Hello or other credential-based mechanisms for elevation.
Beyond security, AP aims to enhance user experience by eliminating dead-end pathways that previously rendered essential functionalities inaccessible to standard users.
For instance, tools like the Group Policy Editor (gpedit.exe), which were unusable when launched by standard users, can now leverage AP’s structured elevation pathways for seamless functionality.

However, challenges remain. Microsoft acknowledges that specific attack vectors, including token manipulation and DLL hijacking in insecure paths, still require attention.
While mitigated significantly, these vulnerabilities highlight the need for continuous updates to close emerging gaps.
Administrator Protection represents a groundbreaking advancement in Windows security architecture.
Though the feature requires adjustment from users accustomed to auto-elevation workflows, its benefits in mitigating privilege escalation attacks vastly outweigh the temporary inconvenience.
Microsoft has urged developers to update applications for compatibility with AP, signaling its intent to make this feature the default in future releases.
For security-conscious users, Administrator Protection is poised to redefine secure computing on Windows, offering a robust framework to protect against sophisticated threats while encouraging feedback for further refinement.
Are you from SOC/DFIR Teams? – Analyse Malware Files & Links with ANY.RUN Sandox -> Try for Free







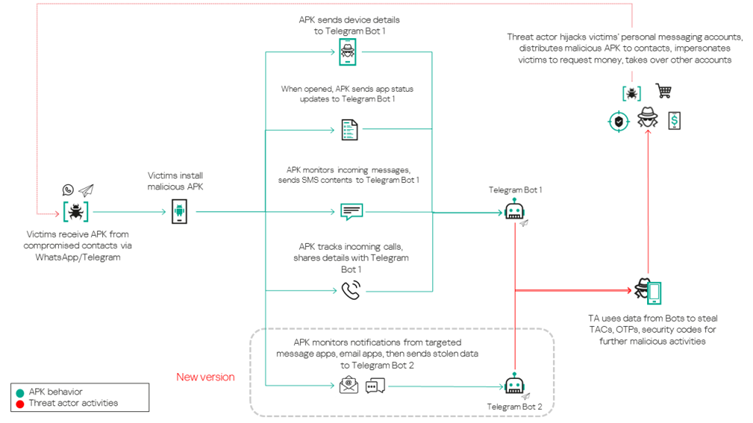
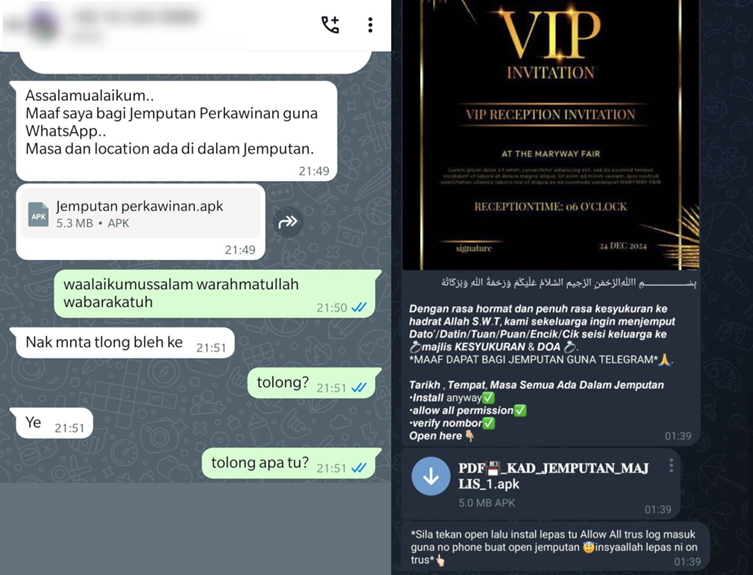

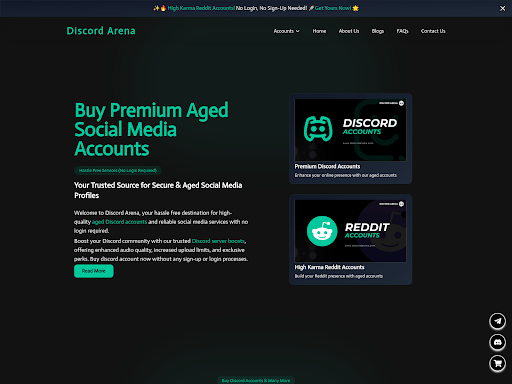
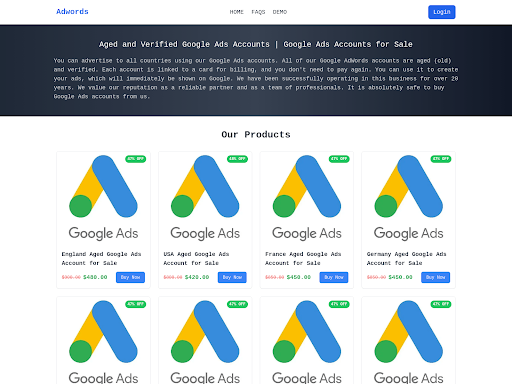



![Here are two of the largest domains identified across thousands of websites - blackshelter[.]org blacksaltys[.]com](https://gbhackers.com/wp-content/uploads/2025/01/image-72.png)