Amazon has confirmed that sensitive employee data was exposed due to a breach at a third-party vendor. The breach arose from exploiting a critical vulnerability in MOVEit, a widely used file transfer software.
The vulnerability, first reported in mid-2023 under the code CVE-2023-34362, has been linked to a massive leak of corporate information affecting multiple global companies across various industries.
The breach was discovered by a hacker operating under the alias Nam3L3ss, who posted the stolen data on a prominent cybercrime forum.
The compromised data includes extensive employee details from several major organizations, including Amazon, which was most severely impacted.
Attend a Free Webinar on How to Maximize Cybersecurity Program ROI
The breach has exposed over 2.8 million Amazon employee records, making it one of the largest data leaks of its kind. Other significant companies affected include HSBC, MetLife, and Cardinal Health.
The vulnerability in MOVEit, discovered in May 2023, allowed unauthorized parties to bypass authentication and access sensitive data transferred through the software.
Despite releasing security patches, the delay in applying these updates exposed several organizations to potential attacks.
Cybercriminals quickly weaponized this vulnerability, leading to a series of high-profile data breaches.
The data stolen during the MOVEit breach includes employee directories containing personally identifiable information (PII) such as names, email addresses, phone numbers, organizational roles, and cost center details.
These datasets, organized by company, have been circulating on underground forums, potentially opening the door to more sophisticated cyberattacks such as phishing, social engineering, and identity theft.
Companies Impacted and Scope of the Breach
According to the report from Infostealers, the leaked data includes detailed employee records from 25 major companies.
The scale of the breach is staggering, with millions of records compromised. Here’s a breakdown of some of the companies involved and the number of records exposed:
| Company Name | Records Exposed |
| Amazon | 2,861,111 |
| MetLife | 585,130 |
| Cardinal Health | 407,437 |
| HSBC | 280,693 |
| Fidelity | 124,464 |
| U.S. Bank | 114,076 |
| HP | 104,119 |
| Canada Post | 69,860 |
| Delta Airlines | 57,317 |
| Applied Materials (AMAT) | 53,170 |
| Leidos | 52,610 |
| Charles Schwab | 49,356 |
| 3M | 48,630 |
| Lenovo | 45,522 |
| Bristol Myers Squibb | 37,497 |
| Omnicom Group | 37,320 |
| TIAA | 23,857 |
| Union Bank of Switzerland (UBS) | 20,462 |
| Westinghouse | 18,193 |
| Urban Outfitters (URBN) | 17,553 |
| Rush University | 15,853 |
| British Telecom (BT) | 15,347 |
| Firmenich | 13,248 |
| City National Bank (CNB) | 9,358 |
| McDonald’s | 3,295 |
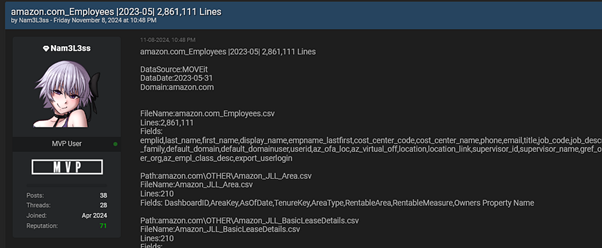
The stolen data from Amazon contains sensitive employee information, including names, email addresses, phone numbers, and organizational structures.
This level of detail poses a significant risk to Amazon’s internal security as it could be used for targeted phishing and corporate espionage. Similarly, HSBC’s dataset includes information on its global workforce, listing employees across multiple countries and divisions.
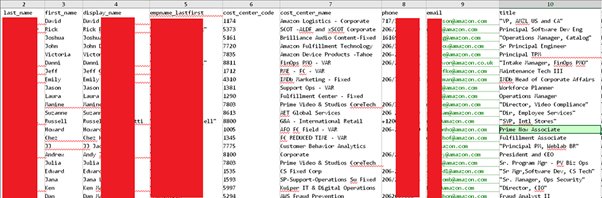
Snippet from the data related to Amazon.com containing entries for over 2,500,000 Amazon employees
The hacker Nam3L3ss posted a public message along with the data, warning companies to “pay attention” to the significance of the breach.
The hacker emphasized that many of the exposed datasets include internal organizational structures, which could be exploited for malicious purposes. The breach raises several key risks for the affected companies and their employees:
- Phishing and Social Engineering: With detailed contact information, cybercriminals can craft compelling phishing attacks aimed at individuals and companies.
- Corporate Espionage: Access to internal organizational structures provides insights into company operations, which competitors or malicious entities could exploit.
- Reputational Damage: High-profile companies like Amazon and HSBC may face long-term reputational harm as customers and stakeholders question their data security practices.
- Financial Theft and Fraud: Due to the nature of the exposed data, companies in sectors such as finance and healthcare, including Cardinal Health and UBS, are at heightened risk of financial fraud and theft.
Amazon has stated that it is working closely with cybersecurity experts to investigate the full extent of the breach and implement additional security measures to safeguard its employees’ data.
However, the true impact of this breach may unfold in the coming months as the compromised data continues to circulate in cybercriminal forums.
Run private, Real-time Malware Analysis in both Windows & Linux VMs. Get a 14-day free trial with ANY.RUN!



.png
)
