A recent blog post by developer Jeff Johnson has brought to light a new feature in Apple’s Photos app within the recently launched iOS 18.
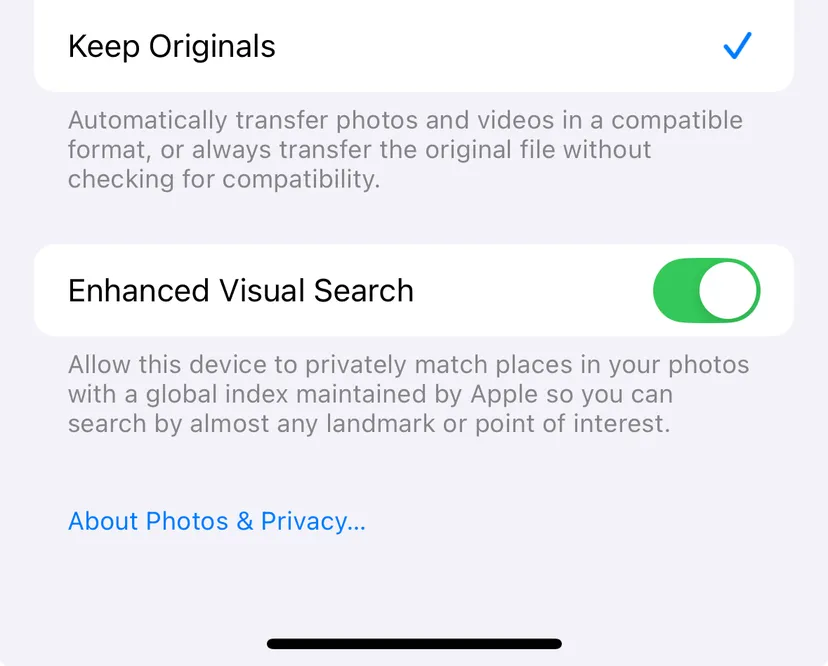
Titled “Enhanced Visual Search,” this toggle permits iPhones to transmit photo data to Apple by default, raising concerns about user privacy and data-sharing practices.
Enhanced Visual Search: A New Feature in iOS 18
The Enhanced Visual Search function, reminiscent of Apple’s existing “Visual Look Up” feature, allows users to identify landmarks and natural elements in their photos through advanced machine learning algorithms.
When activated, users can simply swipe up on an image featuring a building or landmark and select “Look Up Landmark” to obtain information about it. However, its default activation means that many users may be unknowingly sharing their photo metadata with Apple.
Investigate Real-World Malicious Links, Malware & Phishing Attacks With ANY.RUN – Try for Free
Johnson’s post in The Verge highlighted that while the toggle is designed to help users find and identify places within their photo library, the underlying mechanics involve sending potentially sensitive data to Apple’s servers.
According to Apple’s research, the process entails creating vector embeddings of parts of images containing landmarks and sending these along with several artificial queries to Apple for further analysis. The company then returns possible matches to the user’s device.
Despite its innovative capabilities, the default setting has sparked privacy discussions. Johnson referenced Apple’s 2019 marketing slogan: “What happens on your iPhone, stays on your iPhone.”
He argued that the very act of transmitting data to Apple undermines this claim. The risk of software bugs and potential data breaches raised further questions about the integrity of user privacy.
Johnson expressed skepticism toward Apple’s assurances, stating that even without any ill intentions from the company, the mere possibility of vulnerability is enough to warrant concern.As of now, Apple has not responded to inquiries regarding these privacy concerns.
Users interested in adjusting this setting can find the Enhanced Visual Search option nestled within the iOS and iPadOS under Settings > Apps > Photos, or for Mac users, under the “Search” heading in Photos > Settings.
The integration of the Enhanced Visual Search feature in iOS 18 serves as a testament to Apple’s commitment to enhancing user experience through technology.
However, as the tech giant continues to innovate, it is crucial for users to remain vigilant about their privacy settings. Transparency from Apple concerning data handling practices will be essential in maintaining user trust in an era where digital privacy is increasingly at stake.
Find this News Interesting! Follow us on Google News, LinkedIn, and X to Get Instant Updates!



.png
)
