Cybersecurity researchers have uncovered a sophisticated attack campaign where threat actors utilized a trojanized Zoom installer to infiltrate systems, gain remote desktop protocol (RDP) access, and ultimately deploy the BlackSuit ransomware.
The operation demonstrates a highly coordinated, multi-stage malware delivery chain designed to evade detection and maximize impact.
Multi-Stage Malware Deployment
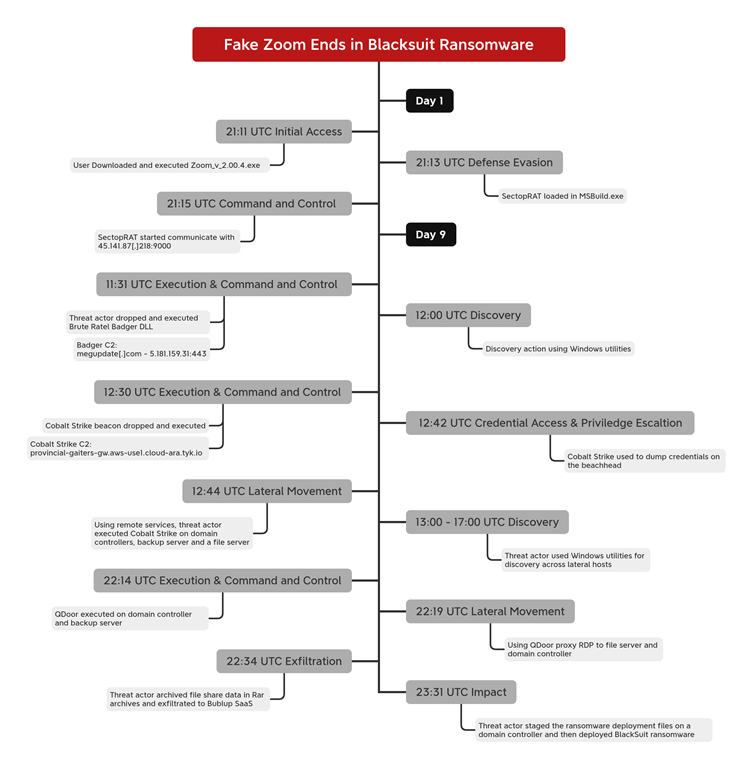
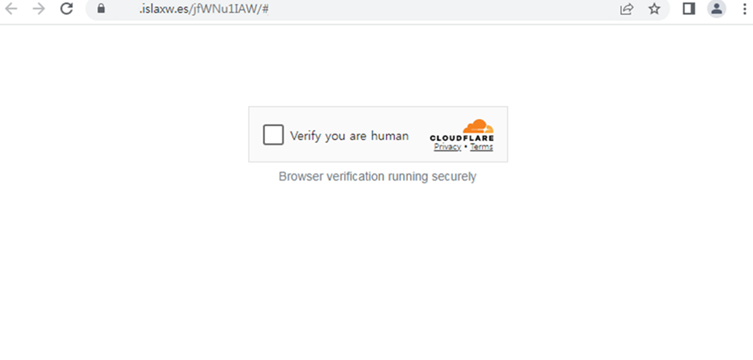
The attack began with a fake Zoom installer hosted on a cloned website resembling the legitimate Zoom application page.

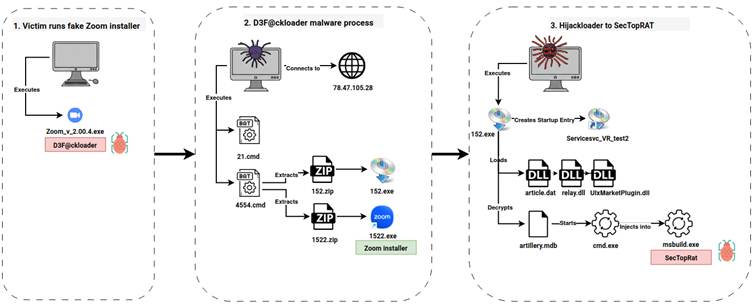
Users downloading the installer unknowingly executed a malicious program embedded with the “d3f@ckloader” downloader.
This loader initiated a series of steps, including disabling security measures, connecting to command-and-control (C2) servers via Pastebin, and downloading additional payloads.
Among these was SectopRAT malware, which was injected into legitimate processes like MSBuild.exe to establish persistence and facilitate further stages of the attack.
After an eight-day dwell period, SectopRAT deployed Brute Ratel and Cobalt Strike payloads for reconnaissance and credential harvesting.
According to the DFIR Report, these tools enabled lateral movement across the network using PsExec and RDP connections tunneled through a proxy malware called QDoor.
QDoor allowed attackers to bypass network defenses by routing traffic through compromised systems.
Data Exfiltration and Ransomware Deployment
Once inside the network, the attackers used WinRAR to compress sensitive files and exfiltrated them to a cloud-based storage service named Bublup.
Following data exfiltration, they staged BlackSuit ransomware for deployment. Using batch scripts and PsExec, the ransomware was distributed across all Windows hosts in the environment.
It encrypted files, deleted shadow copies using vssadmin, and left ransom notes demanding payment.
The entire operation spanned nine days, with a Time-to-Ransomware (TTR) of approximately 194 hours.
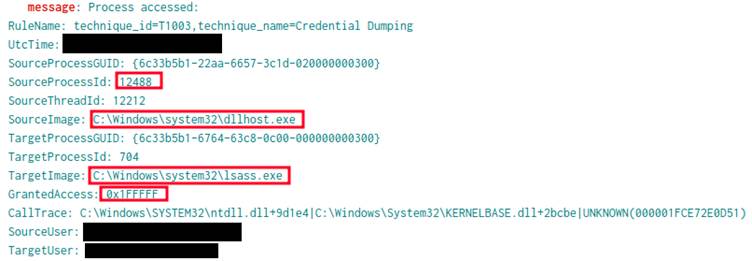
The attackers leveraged advanced techniques such as DLL hijacking, credential dumping from LSASS memory, and API abuse for stealthy execution.
This incident highlights the increasing sophistication of ransomware campaigns that combine social engineering (via fake installers) with advanced post-exploitation frameworks like Brute Ratel and Cobalt Strike.
Organizations are urged to enhance endpoint detection capabilities, monitor for unusual network traffic patterns, and educate users on identifying phishing attempts involving cloned websites.
By employing multiple malware strains and leveraging legitimate tools like RDP and WinRAR, the attackers were able to evade traditional defenses while achieving their objectives.
This case underscores the need for proactive threat hunting and robust incident response mechanisms to mitigate similar attacks in the future.
Find this News Interesting! Follow us on Google News, LinkedIn, and X to Get Instant Updates!









![Initial Malicious Zoom via zoommanager[.]com](https://gbhackers.com/wp-content/uploads/2025/03/image-89.png)