VulnCheck’s latest report for Q1 2025 has identified 159 Common Vulnerabilities and Exposures (CVEs) publicly disclosed as exploited in the wild for the first time.
Alarmingly, 28.3% of these Known Exploited Vulnerabilities (KEVs) saw evidence of exploitation within just one day of their CVE disclosure, underscoring the lightning-fast pace at which threat actors capitalize on newly revealed flaws.
This trend, consistent with patterns observed in 2024, signals an urgent need for defenders to accelerate their response to emerging threats while simultaneously addressing lingering vulnerability debt.
With data sourced from 50 distinct organizations, including major contributors like Shadow Server (31 disclosures) and GreyNoise (17 disclosures), the report paints a comprehensive picture of a dynamic threat landscape.
Key Product Categories and Vendors Under Siege
The exploitation focus in Q1 2025 predominantly targeted internet-facing and end-user-accessible systems, with Content Management Systems (CMS) leading the pack at 35 KEVs, followed by Network Edge Devices (29), and Operating Systems (24).
Notably, categories like desktop applications and browsers, historically frequent targets, recorded lower exploitation rates, hinting at a potential shift in attacker priorities that bears monitoring.

Among vendors, Microsoft Windows topped the list with 15 exploited vulnerabilities, trailed by Broadcom VMware (6) and Cyber PowerPanel (5), reflecting the critical nature of these widely used technologies.
The report also highlights a surge in exploitation disclosures toward the latter half of the quarter, averaging 11.4 KEVs weekly and 53 monthly, providing defenders with crucial insights for capacity planning.
Meanwhile, the CISA KEV catalog added 80 vulnerabilities, though only 12 lacked prior public exploitation evidence, emphasizing the gap between official reporting and real-world activity.
NVD Gaps and Scoring System Limitations
A deeper dive into the National Vulnerability Database (NVD) statuses reveals coverage gaps, with 25.8% of KEVs still awaiting or undergoing analysis and 3.1% marked as “Deferred,” while 69.2% are categorized as “Analyzed” or “Modified.”
Additionally, two KEVs remain in reserved status, and one has been rejected, complicating timely risk assessment.
When mapped to scoring systems like CVSS and EPSS, the data suggests a significant limitation: only a handful of vulnerabilities showed elevated EPSS scores on the day exploitation evidence emerged, positioning EPSS as a trailing rather than predictive indicator.
This finding cautions organizations against over-reliance on such metrics for emerging threat prioritization, advocating instead for real-time threat intelligence and rapid response mechanisms.
The Q1 2025 findings from VulnCheck illuminate a cybersecurity environment where speed is paramount.
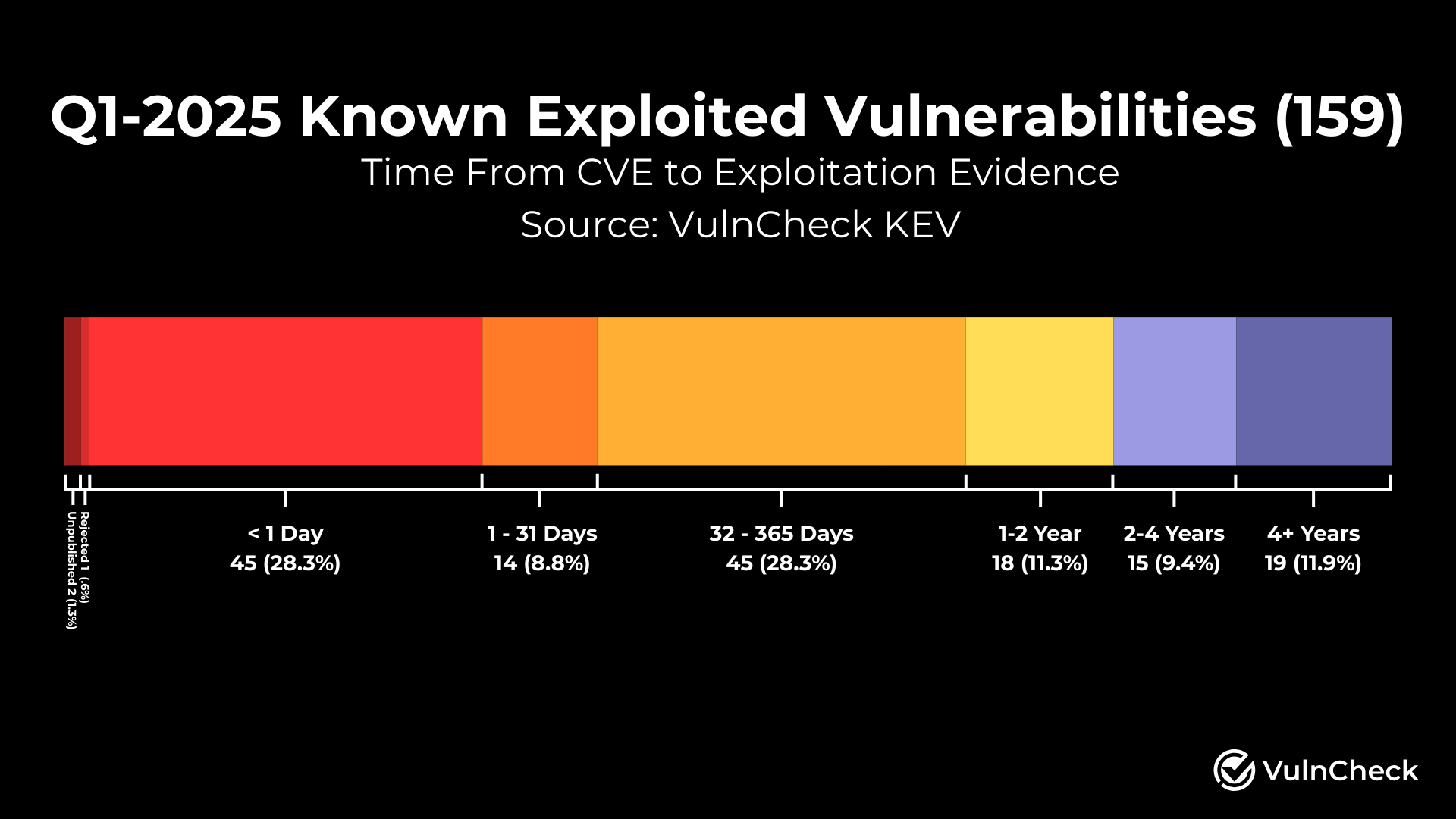
With nearly a third of vulnerabilities exploited within 24 hours of disclosure, and persistent gaps in NVD analysis, defenders must adopt agile strategies to stay ahead.
The focus on CMS, network devices, and operating systems as prime targets further stresses the need for robust patching and monitoring of critical infrastructure.
As threat actors continue to exploit vulnerabilities at an unrelenting pace, the call to action for the cybersecurity community has never been clearer: act fast, prioritize effectively, and fortify defenses against both new and lingering threats.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!



.png
)
