In our modern world, data is the most important asset for businesses. That’s why cybercriminals are generally after the data that companies hold.
These malicious actors want to steal sensitive credentials, financials, new business projects, etc. Today’s decentralized work environments increase the risk of cyber attacks.
As of 2024, all businesses can be a victim of data breaches regardless of their size. That’s mainly because cybercriminals improve malware and use more sophisticated methods to accomplish their malicious goals every day.
Additionally, cyber-attacks and data breaches have severe consequences on businesses. Just a year ago, the global average cost of data breaches was 4.24 million dollars for businesses.
Falling victim to a data breach not only has monetary costs but also intangible results like damaging the reputation and credibility of businesses in the eyes of their customers.
So, businesses have to be more aware of the most common cybersecurity attacks and take measures to prevent them. Let’s explain these cyber security attacks further.
Table of Contents
FAQ
Phishing Attacks
Social Engineering Attacks
Man-in-the-middle Attacks
Network Intrusion Attacks
Malware Attacks
Ransomware Attacks
Insider Threats
Conclusion
FAQ
1.What is a Cyber Attack?
Cyber attacks aim to hack into computer systems, networks, or data to compromise their privacy, availability, or security.
These attacks include malware outbreaks, phishing schemes, DDoS attacks, ransomware, and others.
Cyberattacks can be done for political, moral, economic, or data theft purposes.
Cyberattacks now threaten people, organizations, and nations as we become more tech-dependent. This emphasizes the need for effective cybersecurity to prevent these risks.
2. How can we best protect ourselves from cybercriminals?
Fighting cybercriminals requires active, varied cybersecurity. This includes using strong, unique passwords and two-factor authentication for online accounts, upgrading software to correct vulnerabilities, being cautious when clicking on links or downloading files, and using secure Wi-Fi, especially for critical transactions.
Knowing cyber threats, installing and upgrading antivirus software, and buying and banking online safely is also vital.
Protect mobile devices, maintain privacy settings, and be aware of unexpected personal information requests.
Financial account monitoring, credit report protection, and incident response plans improve cybersecurity. These actions and understanding can considerably reduce cyber risk and secure digital life.
3. What are the main types of cyber attacks?
Cyber attacks use a variety of methods to breach computer systems, steal data, or disrupt digital processes.
Malware attacks involving viruses and ransomware; phishing attacks that use deceptive emails to trick users into revealing personal information; DDoS attacks that overwhelm a target’s online services; MitM attacks that intercept and manipulate data in transit; insider threats from employees; and SQL injection attacks.
Individuals and organizations must be aware of these attack vectors to establish effective cybersecurity measures and protect against evolving threats.
Common Cyber Security Attacks
1- Phishing Attacks

Phishing is one of the most common cyber security attacks which malicious actors use. In these attacks, cybercriminals are after users’ credentials such as ID, passwords, credit card information, etc.
To accomplish their goal, they create fake websites that look like legitimate institutions. Then, they send emails or SMS messages which include infected attachments or links to fake websites.
- Once target individuals click on these links or download infected email attachments, hackers steal their sensitive credentials.
- After stealing these credentials; hackers can blackmail users, sell them on the internet, or use them to get into corporate networks, etc.
- So, everyone should be cautious about downloading email attachments or clicking login links.
2- Social Engineering Attacks

Cybercriminals are aware that bypassing security systems is difficult and complex. So, social engineering attacks’ goal is to steal credentials or get into the corporate systems by exploiting human error.
They deceive individuals to reveal their sensitive credentials. These attacks can happen via phone calls, infected flash disks, emails, etc.
3- Man-in-the-middle Attacks
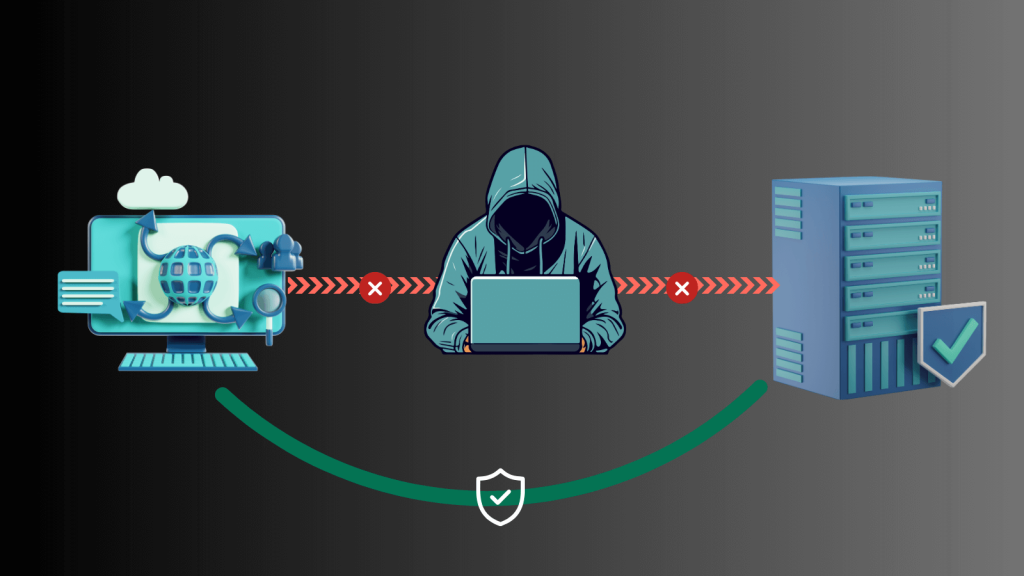
A Man-in-the-Middle (MitM) attack is when someone listens in on two people talking to each other online and might change what they are saying without them knowing or agreeing.
Most of the time, this kind of attack happens when there aren’t any safe ways to communicate or when an attacker gets in between the real sender and receiver.
MitM attacks are a big security risk because they can cause data breaches, identity theft, money losses, and people to get to private information without permission.
These attacks can happen on public Wi-Fi networks, routers that have been hacked, email messages, and even encrypted connections if the attacker knows how to decrypt the information.
4- Network Intrusion Attacks

Network intrusion attacks’ goal is to gain unauthorized access to online or corporate networks.
If cybercriminals can bypass network security, they can reach all of the data a company holds.
Network intrusion attacks happen via some malware types that give hackers unrestricted access to corporate networks. So, they can reach and possess sensitive data.
5- Malware Attacks

Malware is a malicious code constructed by cybercriminals to do certain tasks in the target machine’s systems.
Additionally, there are numerous malware types, and these differ according to their purpose.
But, a malware attack’s goal is to steal sensitive data, create a hole in the target’s cybersecurity posture, and disable the security system’s functions.
- Today, cybercriminals try to use improved malware that can slip through security systems without security systems noticing it.
- Especially, when companies use out-of-date security tools, malware attacks are difficult to detect.
- So, businesses should be more aware of these constantly evolving malware types and adopt enhanced malware detection tools because these are critical for immediate response against attacks.
6-Ransomware Attacks

Ransomware attacks are generally after financial earnings. These attacks’ goal is to infect the target’s systems with a specific type of malware and get hold of data storage.
Once cybercriminals access the storage, they encrypt all the data and demand ransom in exchange for decryption.
- Most of the time, businesses accept to pay the ransom because encrypted data is critical for them.
- But, in the cases where businesses don’t accept to pay the ransom or can’t afford it, ransomware threatens to share or sell the data on the internet.
- During the last few years, ransomware attacks have been increasing drastically. By 2031, ransomware damage costs are forecasted to exceed 265 billion dollars globally.
- That’s why businesses should be more aware of ransomware attacks.
7- Insider Threats
Generally, businesses want to trust their employees fully. But, giving unlimited access to them can be very risky.
In the cases where a business gives unlimited access to its employees, insider attacks can have severe consequences.
In these types of attacks, employees can work with cybercriminals in exchange for money. They can install malware that creates backdoors on the target’s cybersecurity posture or use their unlimited access to leak data to these criminals.
To eliminate the massive impacts of insider attacks, businesses can implement network segmentation, Zero Trust Access Network (ZTNA), and Secure Access Service Edge (SASE) solutions.
Conclusion
The more our work environments become decentralized and web-oriented, the more we are up against cyber-attacks.
A single successful data breach has severe outcomes for a business. So, it is important to acknowledge potential threats and take measures accordingly.
People and businesses should stay alert, learn about new threats, and take strong cybersecurity steps to protect themselves from a wide range of possible attacks in order to stay safe in the future.
This means that they need to keep their software up to date, use strong authentication methods, teach their workers and users about best practices for security, and regularly test and improve their cybersecurity defenses.
It’s important to read cybersecurity news and talk to experts in the field to stay up to date on the newest cyber risks in 2024 and beyond.
-1.webp?w=696&resize=696,0&ssl=1)


.png
)
