SmuggleShield, a recently launched browser extension, is gaining attention in the cybersecurity space for its innovative approach to mitigating HTML smuggling attacks.
With its stable version (2.0) now available, SmuggleShield provides an additional layer of protection for everyday internet users, security professionals, and red/purple team exercises.
While not a perfect or exhaustive solution, its cutting-edge features and machine learning integration make it a promising tool in the fight against malicious web-based attacks.
What Is SmuggleShield?
SmuggleShield is a browser extension developed for Chrome and Edge browsers on both macOS and Windows.
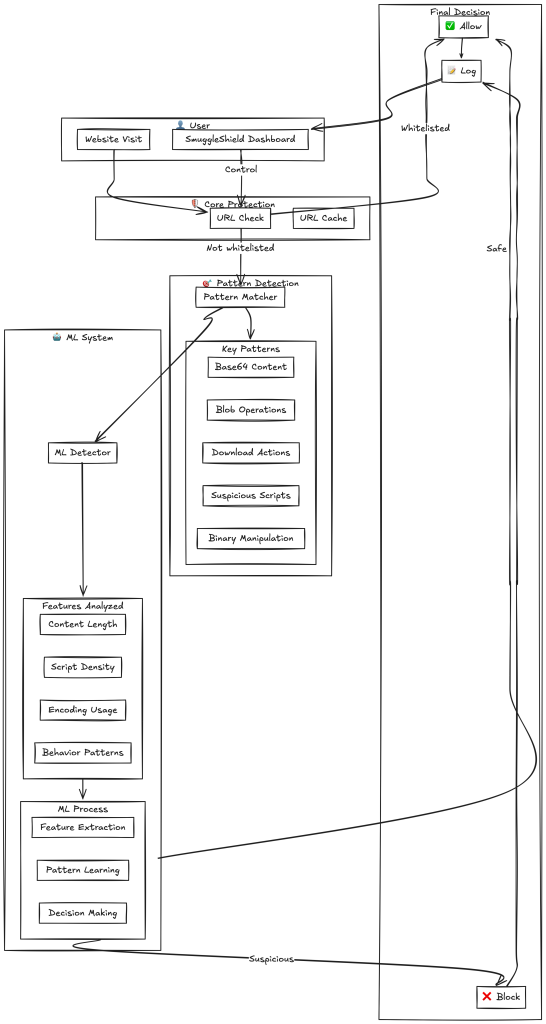
It aims to detect and block HTML smuggling—a sophisticated web-based attack technique where malicious payloads are constructed within browsers to bypass detection.
Users can install SmuggleShield by enabling developer mode in their browser’s extension settings and uploading the SmuggleShield folder via “Load unpacked.”
Once installed, the extension scans webpages for suspicious patterns, blocking potentially dangerous URLs. Blocked entries—including the URL, timestamp, and malicious pattern—are stored in its cache for up to 10 days, with logs exportable for review.
Key Features
- URL Whitelisting:
While SmuggleShield scans every webpage element for potential threats, some users may experience slight delays in webpage loading. The URL Whitelisting feature allows trusted websites to bypass this scanning, significantly reducing overhead while maintaining security elsewhere. - Machine Learning-Powered Detection:
SmuggleShield uses a hybrid approach combining pattern-based and machine-learning (ML) analysis. Its ML component extracts six critical features—such as base64Length, blobUsage, scriptDensity, and binaryManipulation—to predict threats with a confidence threshold of 0.75. The ML model undergoes continuous learning, adapting to emerging threats by storing patterns locally using chrome.storage.local. - Incognito Mode Support:
SmuggleShield can actively defend against HTML smuggling attacks in incognito mode, making it ideal for private browsing. However, users must manually enable this feature from Chrome’s extension settings due to security policies.
SmuggleShield has already demonstrated potential in preventing past real-world cyberattacks. For instance, it could have thwarted:
- The Quakbot campaign (July 2022)
- DCRat malware distribution using HTML smuggling
- Pikabot malware linked to TA577 threat actor
- Delivery of AsyncRAT via malspam campaigns
While a version of SmuggleShield is available on the Chrome Web Store, the developers recommend downloading it from GitHub for the most comprehensive functionality and updates.
With HTML smuggling attacks becoming a growing concern, tools like SmuggleShield are critical for enhancing browser security.
Its unique combination of pattern detection and machine learning integration positions it as a vital addition to personal and professional cybersecurity arsenals.
Investigate Real-World Malicious Links, Malware & Phishing Attacks With ANY.RUN – Try for Free



.png
)
