A surge in cyber activity targeting critical edge technologies and management tools, including SonicWall, Zoho, F5, Ivanti, and other systems, has been flagged by cybersecurity intelligence firm GreyNoise.
The sudden spike in probing and exploitation attempts highlights an alarming trend: Hackers are increasingly targeting vulnerabilities in widely used systems, potentially exposing businesses to significant threats.
Significant Spike in Cyber Activity
GreyNoise telemetry identified an unprecedented rise in activity targeting these technologies, signaling that threat actors will likely conduct reconnaissance or actively exploit unpatched vulnerabilities.
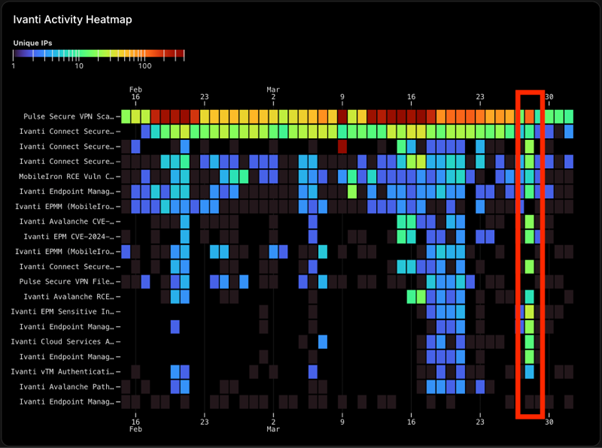
SonicWall and F5, known for their critical network and application delivery systems, along with Zoho, a popular enterprise IT tool, and Ivanti, which specializes in unified endpoint management, appear to be primary targets.
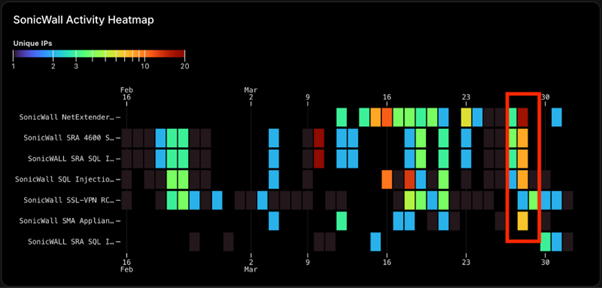
Edge systems like Zyxel and Linksys were also observed under scrutiny, underscoring that both critical infrastructure and internal IT management systems are at risk.
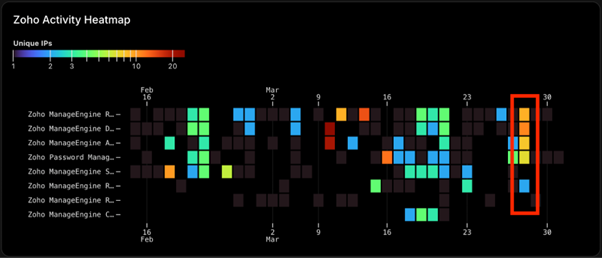
GreyNoise’s findings hint at the possibility of coordinated attacks or opportunistic exploitation campaigns by cybercriminals or advanced persistent threat (APT) groups.
Implications for Cybersecurity
The observed activity raises concerns about the security posture of businesses relying on these technologies.
For organizations, the risks are twofold: edge technologies directly face the internet and are vulnerable to external attacks, while internal systems like Ivanti and Zoho, if breached, can provide attackers with deeper access to networks.
Cybersecurity experts warn that this spike is likely just the beginning. Threat actors often capitalize on unpatched systems or newly-disclosed vulnerabilities to infiltrate networks, steal sensitive data, or deploy ransomware.
GreyNoise’s Recommendations
To mitigate potential threats, GreyNoise has outlined critical measures that organizations should implement immediately:
1. Patch Management: Ensure all systems are running the most up-to-date security patches. Unpatched vulnerabilities often serve as the entry point for attackers.
2. Network Monitoring: Analyze network traffic closely, specifically logs from March 28, for unusual patterns. Retroactive monitoring can help identify any signs of compromise during the activity spike.
3. Threat Intelligence Tools: Use real-time threat intelligence platforms such as the GreyNoise Visualizer. Organizations can search targeted vulnerabilities (CVEs) and block malicious IP addresses based on telemetry data.
The exploitation attempts underline the need for businesses to adopt proactive security measures. With the interconnected nature of edge and internal management systems, a single vulnerability can act as the gateway to widespread damage.
Organizations must stay vigilant, conduct regular risk assessments, and ensure robust cyber defenses to counter emerging threats.
Cybersecurity experts reiterate that the best protection lies in staying one step ahead of attackers—by patching systems promptly, investing in threat intelligence, and fostering a culture of awareness.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!



.png
)
