Malicious PDF files have emerged as a dominant threat vector in email-based cyberattacks, accounting for 22% of all malicious email attachments, according to a recent report by Check Point Research.
With over 87% of organizations relying on PDFs for business communication, the ubiquitous file format has become a prime target for cybercriminals, who exploit its complexity and trusted reputation to bypass security measures.
Why PDFs Are Cybercriminals’ Favorite Tool
The Portable Document Format (PDF) is widely recognized as user-friendly and secure, but its intricate structure—defined in a nearly 1,000-page specification—makes it a fertile ground for exploitation.
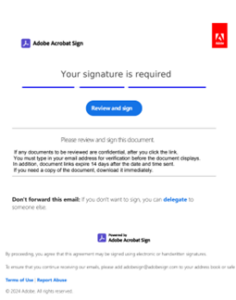
Attackers often hide malicious links, harmful code, or phishing schemes within PDFs, making them particularly difficult for traditional security tools to detect.
Threat actors have shifted tactics over the years. While past attacks relied on exploiting vulnerabilities in outdated PDF readers, modern attempts focus on sophisticated evasion and social engineering techniques.
For example, attackers embed links to phishing sites or malware in PDFs, often accompanied by images or text that mimic trusted brands like Amazon or DocuSign.
These deceptive tactics exploit users’ trust in the format while flying under the radar of automated detection systems.
Advanced Evasion Techniques
Modern malicious PDF campaigns employ innovative methods to evade detection:
- URL Evasion: Attackers use redirect services from trusted platforms like Bing or Google AMP to mask malicious destinations. QR codes embedded in PDFs are another rising trend, bypassing traditional URL scanners.
- File Obfuscation: Complex encryption and encoding techniques hide malicious content within the PDF, making static analysis tools ineffective. Annotations, clickable areas, and other dynamic elements are used ingeniously to escape detection.
- Machine Learning Manipulation: Cybercriminals now embed malicious instructions in images or invisible text to confuse machine learning and optical character recognition (OCR) systems, undermining next-gen security measures.
The simplicity of clicking a link within a PDF belies the sophistication of the attacker’s strategy.
By relying on human interaction (e.g., convincing the recipient to click a link), attackers bypass security sandboxes and automated tools that struggle with human decision-making.
Implications for Businesses
The increasing prevalence of malicious PDFs is a major concern for organizations that rely heavily on email-based communication.
Cybercriminals have developed a keen understanding of how security providers scan and analyze files, allowing them to exploit gaps in detection.
Businesses are also encouraged to educate employees about phishing risks, adopt multi-layered security protocols, and ensure regular updates for PDF readers and email protection tools.
As the landscape of cyber threats continues to evolve, PDFs are likely to remain a favored attack vector. By understanding the tactics employed by cybercriminals, organizations can stay one step ahead and reinforce their defenses against these insidious threats.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!



.png
)
