In an alarming development, Denmark faced its most extensive cyber attack in May 2023, targeting crucial components of its energy infrastructure.
A total of 22 companies fell victim to a meticulously coordinated attack, breaching their industrial control systems and prompting some to activate island mode operation.
This cyber onslaught marks an unprecedented scale of attack on Danish critical infrastructure, signaling a new level of threat.
The assailants exhibited a deep understanding of their targets, successfully infiltrating 22 companies within a short timeframe, indicating a level of preparation rarely witnessed.
The sophistication of the attack prompts speculation about state involvement, with indications suggesting a possible connection to one or more nation-states.
This revelation adds a layer of complexity to the incident, requiring careful examination of geopolitical implications.
SektorCERT’s sensor network and collaborative efforts with members, suppliers, and authorities made rapid detection and response to the attacks possible.
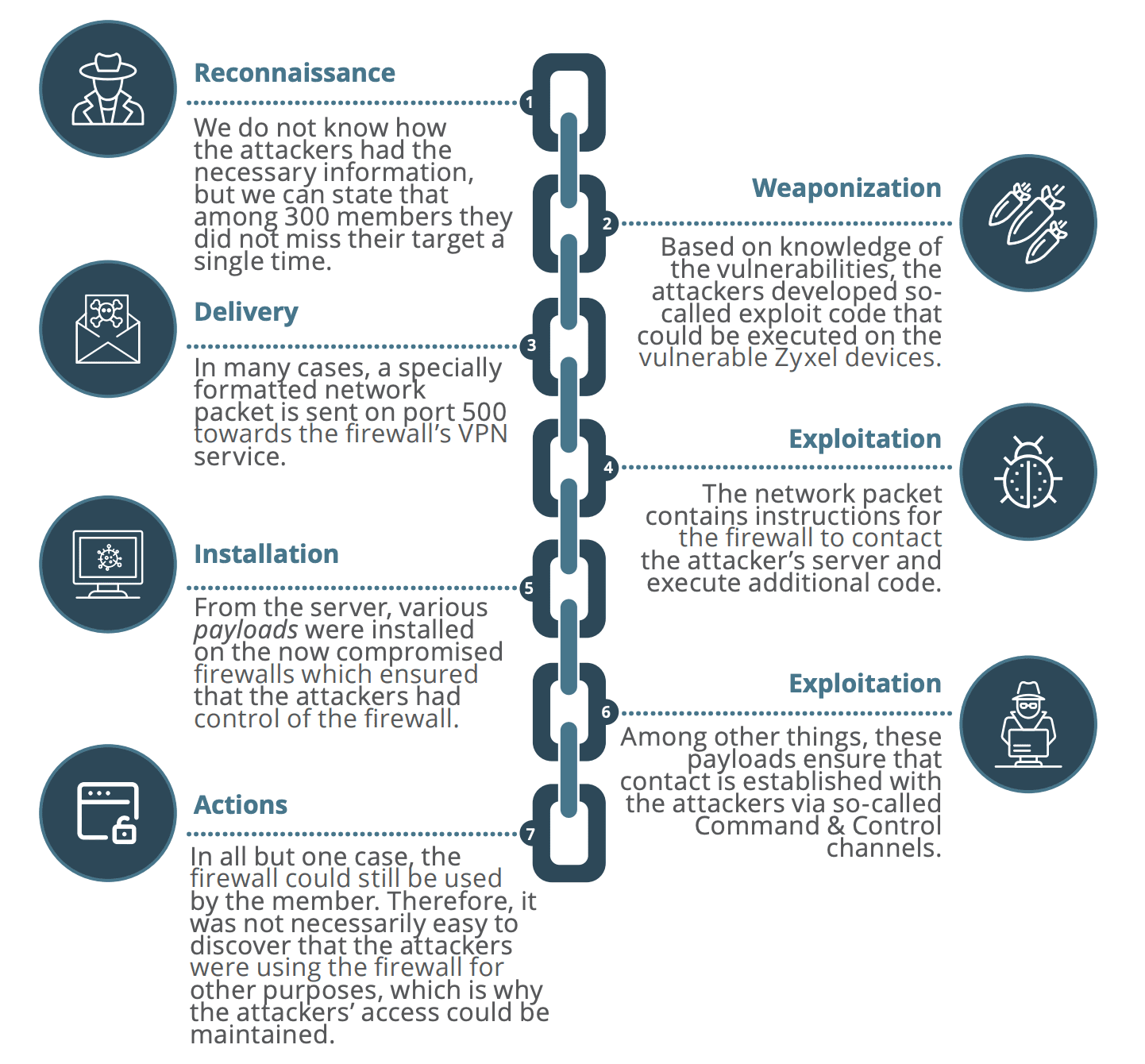
Without this proactive approach, the consequences for Denmark’s infrastructure could have been severe.
SektorCERT’s post-attack recommendations emphasize the importance of implementing all 25 of their proposed measures for those operating critical infrastructure in Denmark.
The focus extends beyond the specific attack techniques, addressing systemic vulnerabilities and enhancing overall cybersecurity resilience.
Detailed Analysis and Objective Timeline
The report provides a comprehensive cyber attack analysis, distinguishing between subjective analysis and objective timelines.
This division ensures a nuanced understanding of the events, enabling readers to delve into technical details or opt for a broader perspective.
SektorCERT’s sensor network was pivotal in detecting and responding to attack patterns across multiple companies.
The ability to analyze data collectively enabled the identification of attackers and their methods, preventing potential damage to critical infrastructure.
The report acknowledges the difficulty in attributing the attack to specific actors, highlighting the intricate nature of cybersecurity.
While indicators may point to entities like Sandworm, definitive conclusions remain elusive, emphasizing the need for vigilant monitoring and advanced analysis.
Systemic Vulnerabilities and Societal Impact
The attack exposed systemic vulnerabilities within Denmark’s decentralized energy system.
The report underscores the potential societal impact when a common vulnerability exists across multiple companies, urging a collective focus on addressing these vulnerabilities.
Highlighting the perpetual threat to Denmark’s critical infrastructure, the report urges heightened attention and proactive measures to prevent, detect, and respond to cyber-attacks.
SektorCERT’s role in swiftly shutting down attackers’ access averted potentially severe consequences.
The successful cooperation between SektorCERT, members, suppliers, and authorities minimized the consequences of the attacks on critical infrastructure.
The report acknowledges the collaborative efforts that played a crucial role in mitigating the impact.
While indications suggest state actor involvement, the report refrains from delving into geopolitical consequences, focusing on technical aspects.
SektorCERT’s analysis concludes with recommendations, emphasizing the need for a collective effort to secure Denmark’s critical infrastructure.
Patch Manager Plus, the one-stop solution for automated updates of over 850 third-party applications: Try Free Trial.


.png
)
