VirusTotal has announced a major change to its Crowdsourced AI project: it has added a new AI model that can examine strange macros in Microsoft Office files.
This model, created by Dr. Ran Dubin from Ariel University and the ByteDefend Cyber Lab, is meant to help the platform find and analyze possible threats in Word, Excel, and PowerPoint files.
VirusTotal’s Crowdsourced AI project uses several AI models and community contributions to improve cyber defense tactics.
Even though AI-based models aren’t perfect, they are very helpful because they work with other technologies to find and analyze new dangers.
The addition of ByteDefend’s model improves VirusTotal’s Code Insight features. These features already use up to three separate AI systems for Microsoft Office files.
Free Webinar on Live API Attack Simulation: Book Your Seat | Start protecting your APIs from hackers
Consensus on Malicious Files
In a recent case, all three AI models agreed that an XLS file being studied was malicious, though they provided different amounts of information.
This agreement shows how useful it is to use more than one AI engine to check for possible threats.
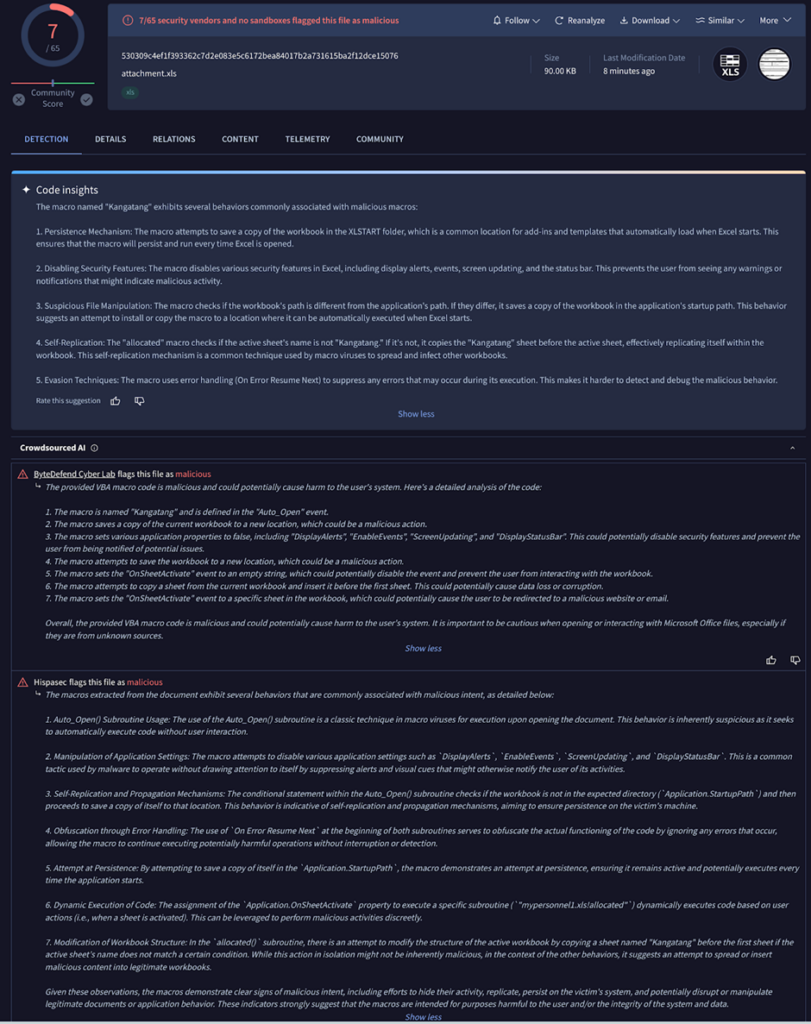
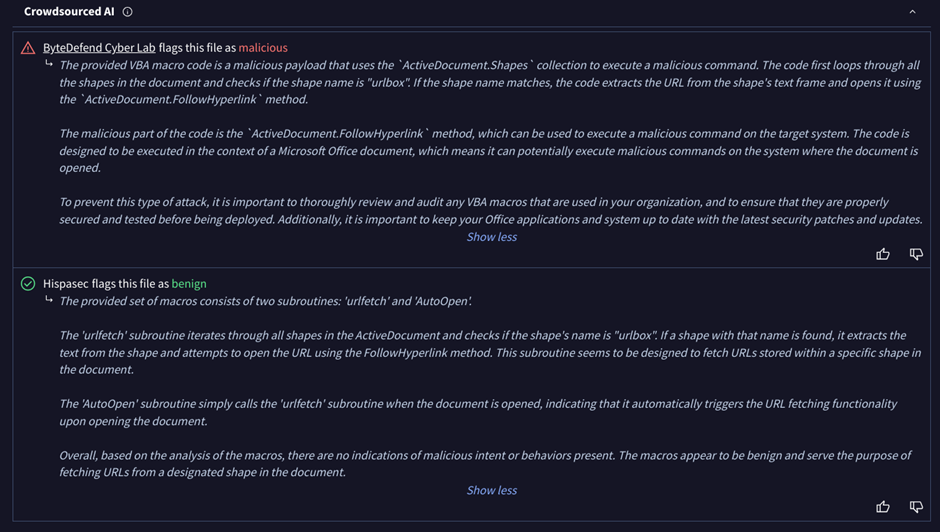
Another time, ByteDefend marked a DOC file as harmful, but Hispasec’s system thought it was safe.
These differences of opinion show how subjective danger analysis is and how important context is.
Even though the models come to different conclusions, they explain in detail how the macros work, which gives human researchers the information they need to make intelligent choices.
Enhanced Search Capabilities
Users can view AI report results through VT Intelligence.
The “bytedefend_ai_analysis:” modifier lets users search the AI’s output, and the “bytedefend_ai_verdict:” modifier lets users search by verdict.
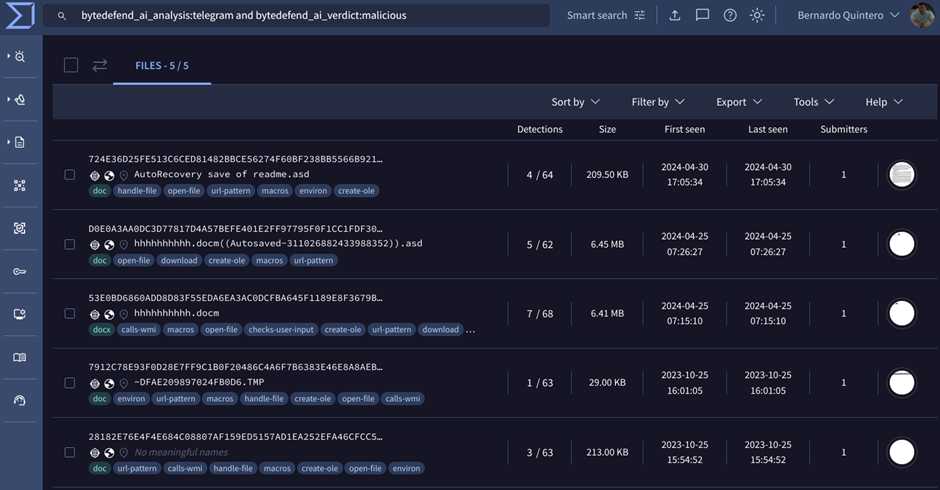
For instance, the query bytedefend_ai_analysis: telegram and bytedefend_ai_verdict:
malicious can be used to look for ByteDefend reports that mention “telegram” and have a malicious judgment.
The ByteDefend Cyber Lab and Dr. Ran Dubin deserve praise for their important work, which VirusTotal appreciates.
The platform plans to grow its Crowdsourced AI project by letting more people with a wide range of skills and knowledge contribute.
The goal is to create a strong defense plan that everyone can work on to deal with the constantly changing online threats.
VirusTotal wants other people in the security field to join this cause.
By adding ByteDefend’s AI model, VirusTotal keeps improving its ability to look for and analyze threats in Microsoft Office files.
This makes it even more of a star in cybersecurity innovation.
On-Demand Webinar to Secure the Top 3 SME Attack Vectors: Watch for Free
.webp?w=696&resize=696,0&ssl=1)


.png
)
