Threat actors advertising a new Combolists-as-a-Service model to sell credentials on the underground hacking forums that enable account takeovers. Attackers employ several methods to gain access to the account that includes breached login credentials, phishing, malware, and bulk passwords.
Pony or TrickBot are the commonly used malware variants used by attackers to harvest login credentials form the compromised systems. By having the unique credentials attackers can launch credential stuffing attacks.
The credential stuffing attacks is an automated process that uses breached username/passwords to gain unauthorized access of user accounts at a very large scale.
Combolists-as-a-Service
According to Photon Research Team’s report, the crooks selling combo lists of passwords dubbed “combo lists-as-a-service”, that includes cracked passwords from and the passwords harvested in other farms.
“Scanning chatter on underground cracking sites, we identified threat actors on the cracking forum CrackedTO actively branding and marketing combo-lists, as if they are tradable commodities.”
The post at Datasense claims that the combo lists are up-to-date and claims itself as a quality product. “Like most marketing narratives, the advertisement goes on to list why users should choose this service, highlighting that the team is made up of “experienced crackers.”

Crooks also offering monthly subscription packages for $50 that let the users access the entire package for 30 days. the database hub advertisement shows collections of passwords based on the categories like Gaming, Crypto, Mix and more.
To get the password’s users needs to have an account and to purchase token’s, by having the token users can retrieve the data. The CaaS’s method is a shift in cybercriminals method to distribute the credentials.
Previously crooks used to advertise as an individual combo list and now that has been streamlined to dedicated services and to automate the process.
Once the attackers have access to the password they can use credentials stuffing tools like SNIPR, Cr3d0v3r and more to launch attacks at a large scale.
Account Takeover Impacts & How to compact
The take over account can be used for malicious purposes, it possesses real thread for account owners, the attackers may change details, withdraw money and if the password reused, they gain access to other accounts also.
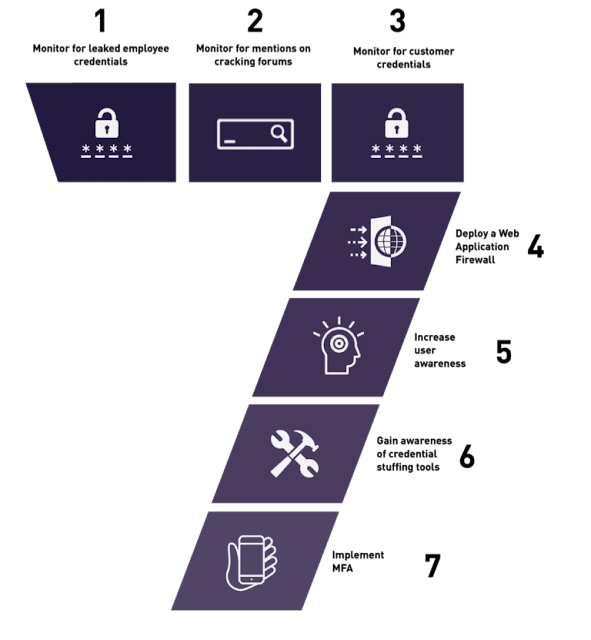
To compact the account takeovers a shifting practice is required.
Solutions to Secure your Account
1.) Never reuse the same password for all the apps/sites.
2.) Increase the strength of the password by adding more mixe characters.
3.) Get a password manager.
4.) Enable 2-Factor-Authentication on social media platforms
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity updates also you can take the Best Cybersecurity course online to keep yourself updated.



.png
)
