Amazon has taken a significant step forward to enhance the security of its cloud environment.
The introduction of advanced AI/ML threat detection capabilities in Amazon GuardDuty marks a major milestone in securing applications, workloads, and data against modern threats.
This new feature is designed to provide improved threat detection by leveraging AWS’s extensive cloud visibility and scale, offering users a more comprehensive and proactive approach to cloud security.
The complexity of modern cloud environments and the constantly evolving landscape of security threats pose significant challenges for organizations.
Security teams are often overwhelmed by the sheer volume of security events, and it becomes increasingly difficult to detect and respond to threats efficiently.
Leveraging 2024 MITRE ATT&CK Results for SME & MSP Cybersecurity Leaders – Attend Free Webinar
This complexity is compounded by the fact that many attacks unfold as sequences of events over time, making it crucial for security solutions to accurately correlate these sequences to identify larger attack patterns.
To address these challenges, Amazon has expanded GuardDuty’s capabilities to include sophisticated AI and machine learning algorithms that can detect both known and previously unknown attack sequences.
These new capabilities help security teams to piece together related activities that could be part of a larger attack, thereby preventing potential threats before they inflict significant damage.
Advanced AI/ML Threat Detection Capabilities
The enhancement in GuardDuty’s threat detection employs advanced AI/ML models to correlate security signals, identifying complex attack sequences in the AWS environment.
These sequences can involve multiple steps taken by adversaries, such as privilege discovery, API manipulation, persistence activities, and data exfiltration.
With the introduction of attack sequence findings, GuardDuty has unveiled a new level of critical severity for findings that represent the utmost confidence and urgency.
This enhancement not only identifies attack sequences but also enriches existing detections with improved actionability.
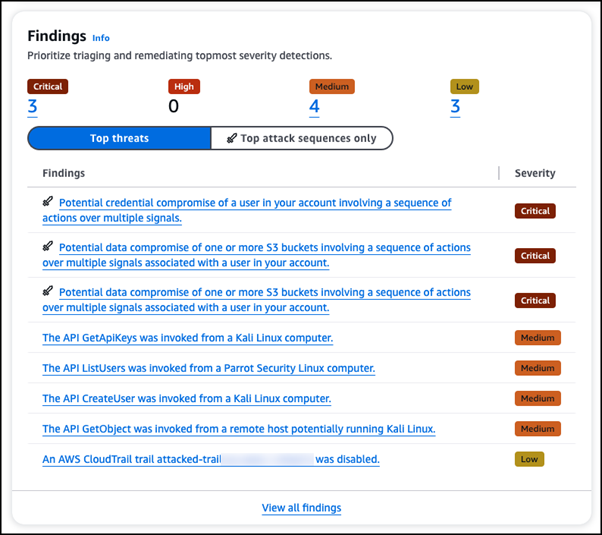
For example, the system now provides comprehensive composite detections that span multiple data sources, periods, and resources within an account.
This allows for a more holistic understanding of sophisticated cloud attacks, enhancing the organization’s ability to respond effectively.
GuardDuty’s enhanced threat detection capabilities are designed to integrate seamlessly with existing security workflows.
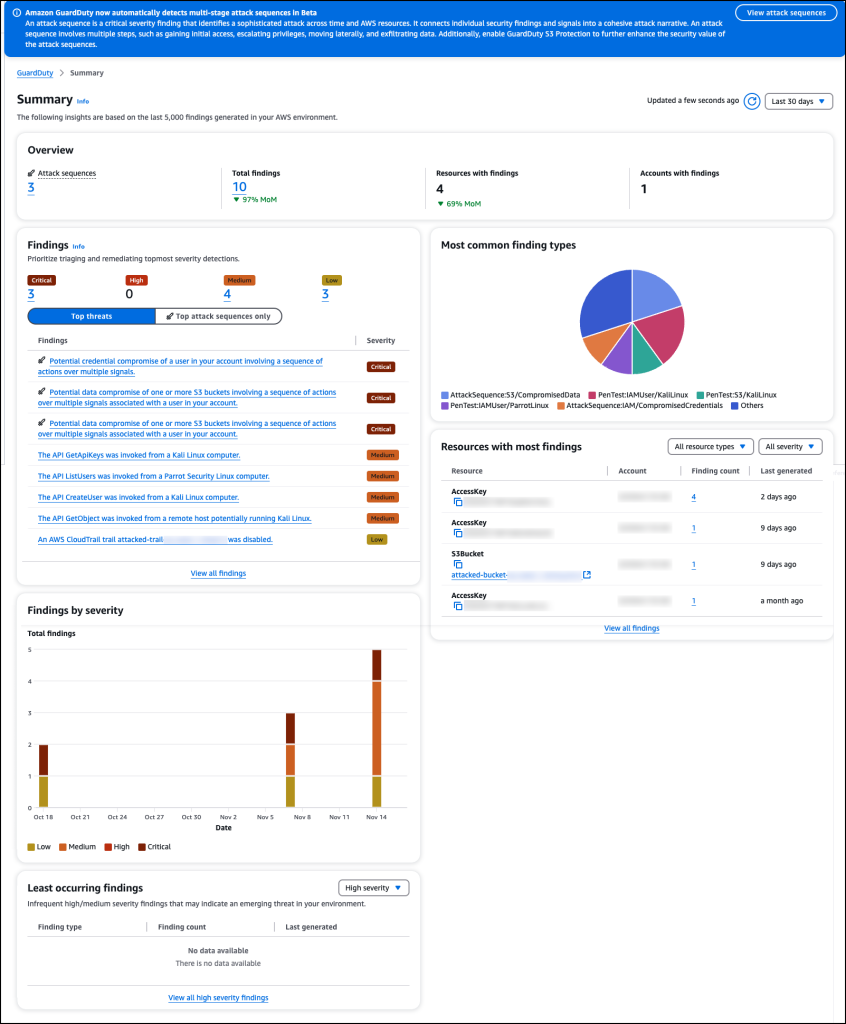
Users can access the new AI/ML capabilities by navigating to the Amazon GuardDuty console, where they will find additional widgets on the Summary page.
These widgets provide an overview of the number of attack sequences detected and help users investigate specific threats by sorting findings by severity.
The findings now include a natural language summary of the threat’s nature and significance, mapped to tactics and techniques from the MITRE ATT&CK® framework.
This summary, coupled with prescriptive remediation recommendations based on AWS best practices, provides actionable insights to swiftly address and resolve identified threats.
The enhanced threat detection is enabled by default, with no additional costs beyond the underlying charges for GuardDuty and associated protection plans.
The new capabilities integrate with existing Amazon GuardDuty workflows, including AWS Security Hub and third-party security event management systems. Notably, the system recommends activating S3 Protection to detect potential data compromises involving Amazon S3 buckets.
Amazon GuardDuty’s expansion with AI/ML-driven threat detection capabilities revolutionizes cloud security by offering a deeper, more actionable understanding of potential threats.
By automating the detection of complex attack sequences and providing actionable insights, GuardDuty empowers organizations to enhance their security posture significantly.
Analyse Advanced Malware & Phishing Analysis With ANY.RUN Black Friday Deals : Get up to 3 Free Licenses.



.png
)
