A security flaw found in Android-based kiosk tablets at luxury hotels has exposed a grave vulnerability, potentially allowing attackers to control air conditioning, lighting, and other room functions remotely.
The investigation, highlighted by security researchers at LAC Co., Ltd., reveals how these vulnerabilities could compromise guest privacy and hotel security.
These devices, now commonplace in upscale hotels, offer convenience, controlling amenities like AC, lighting, and room service orders.

Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free
Vulnerabilities in Android Kiosk Mode Tablets
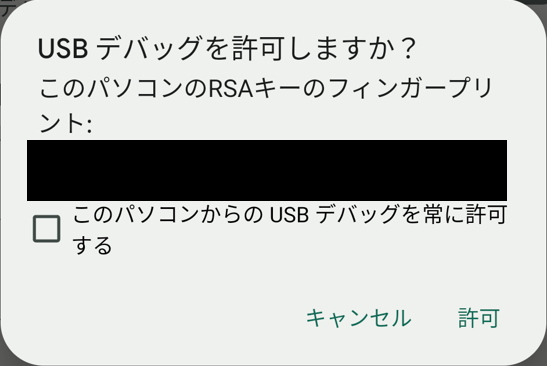
- USB Debugging Exploitation
The researchers discovered that USB debugging was activated on the tablet under certain conditions. By rebooting the device and quickly connecting it via USB, they bypassed security settings to enable debugging and accessing sensitive device data. This could allow attackers to install malicious applications or even eavesdrop through cameras and microphones.
- Temporary Settings Change on Reboot
Between the time the Android operating system launched and the kiosk app loaded, attackers could access system settings, turn on debugging, or configure other critical options.

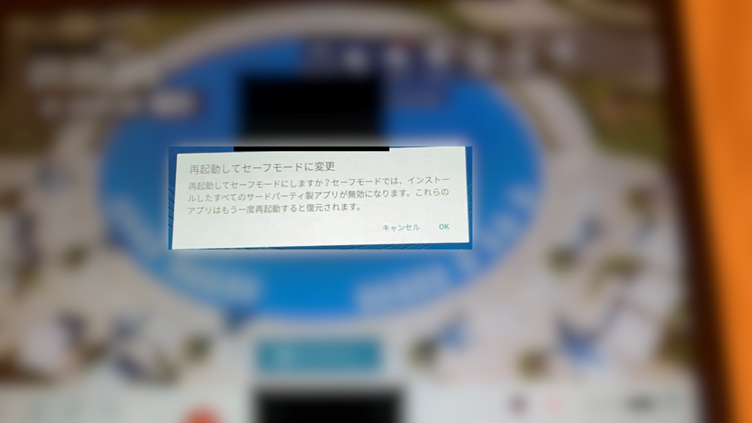
- Safe Mode Exploit
By booting the tablet in Safe Mode, the restrictive kiosk app was disabled, exposing the home screen and allowing attackers to freely navigate the device, modify settings, and exploit its features.
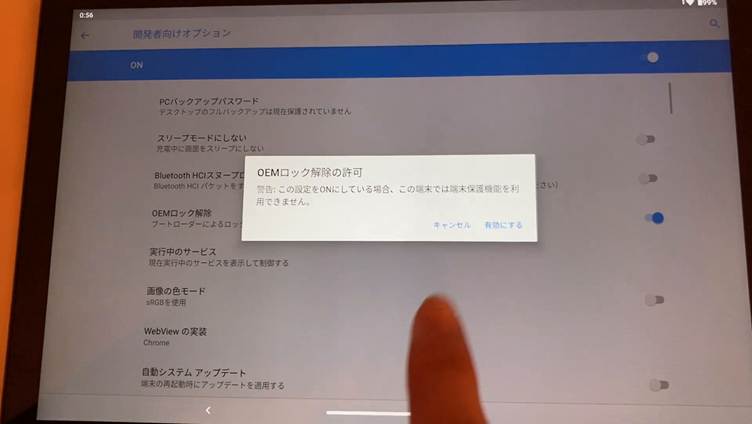
- Potential for Root Access
By unlocking the bootloader — a process surprisingly allowed on these tablets — attackers could gain root privileges, enabling them to fully control the device, install spyware, or further compromise system integrity.
- Network-Based Attacks
Guest room tablets communicated with a central server controlling lighting and air conditioning. Researchers found that authentication between tablets and this server was poorly implemented. An attacker could pose as another room’s device by manipulating specific parameters in network requests, gaining control over other rooms’ amenities or even spying on chat communications with the concierge.
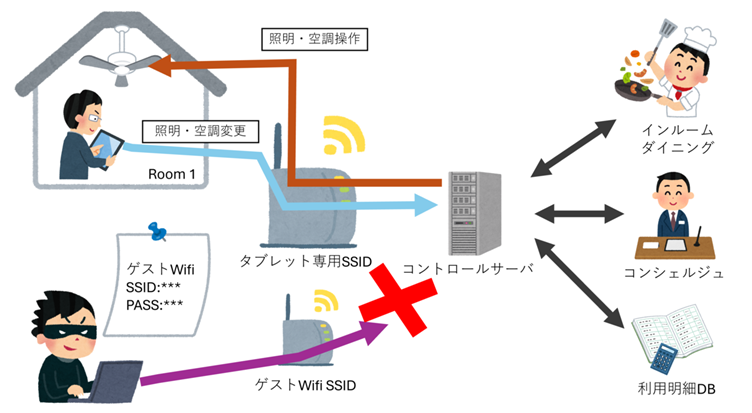
- Weak Wi-Fi Security
The tablets used a stealth SSID for Wi-Fi communication, protected only by a passphrase embedded in the app code. Once deciphered, this provided attackers with access to the entire network, rendering even more rooms vulnerable.
The investigation found identical vulnerabilities in kiosk systems used by multiple hotels nationwide, indicating that this was not an isolated issue but a systemic flaw in how such Android kiosk tablets were deployed and secured.
The consequences of these flaws are alarming:
- Remote Control of Guest Room Functions: Attackers could control AC, lights, and room service requests in other guest rooms.
- Guest Privacy Breach: By accessing cameras, microphones, or chat logs.
- Damage to Reputation: Luxury hotels could face severe backlash for compromising guest experiences and safety.
The vulnerabilities were responsibly disclosed to the affected hotels and the kiosk tablet developers through the Information-technology Promotion Agency (IPA).
All known issues have since been patched, and operational systems updated. Here are the recommended fixes for developers:
- Disable USB Debugging Permanently: Ensure USB debugging is only accessible during authorized maintenance.
- Restrict System Settings Access: Prevent changes during reboot by making the kiosk app the default launcher.
- Enhance Network Security: Use WPA Enterprise authentication and client certificates to secure Wi-Fi communication.
- Implement Server-Side Authentication: Associate unique credentials with each tablet to prevent unauthorized access to server-controlled functions.
- Obfuscate App Code: Reduce ease of analysis through code encryption and other security practices.
This vulnerability underscores the critical need for robust security in IoT (Internet of Things) devices deployed in sensitive environments like hotels.
Developers must consider not only the features of their systems but also the potential avenues attackers could exploit. Hotels, in turn, must prioritize guest safety and privacy by rigorously testing and auditing third-party systems.
The vulnerabilities found in Android kiosk tablets highlight the delicate balance between convenience and security in modern technology.
While these systems offer unparalleled comfort and customization for guests, they also introduce new risks. Ensuring these devices are airtight against exploitation must be a top priority for developers and hoteliers alike.
Integrating Application Security into Your CI/CD Workflows Using Jenkins & Jira -> Free Webinar



.png
)
