Apple now officially dropped plans to let iPhone users have their device backup in an encrypted form in Apple’s iCloud service after the FBI complained.
iCloud is an Apple cloud platform that allows Apple users to store and access their photos, videos, documents, notes, contacts, and more.
Since the FBI has a concern about breaking the icloud more difficult if the company implements the end-to-end encryption, the FBI wouldn’t be able to unlock the encrypted data during the investigation.
Now the Apple decision makes easier for the FBI to unlock the devices and access the backup data stored in the icloud.
Recently Trump attack Apple for refusing to unlock the device used by criminals and stats in his twitter feed “We are helping Apple all of the time on TRADE and so many other issues, and yet they refuse to unlock phones used by killers, drug dealers, and other violent criminal elements.”
According to the Reuters who have gathered this information from the secret source “When Apple spoke privately to the FBI about its work on phone security the following year, the end-to-end encryption plan had been dropped “
Another former employee told that “Legal killed it, for reasons you can imagine,” but there is no specific information he was given that neither why Apple has dropped this plan nor if the FBI was a factor in the decision.
The decision made by Apple seems to be not to make the FBI job easier to break the iPhone during the investigation but it might be a reason for reducing or stop Agencies to relies on hacking software offered by the private security companies that exploit security flaws to break into a phone which requires a direct access to the phone which would ordinarily tip off the user, who is often the subject of the investigation, Reuters reported.
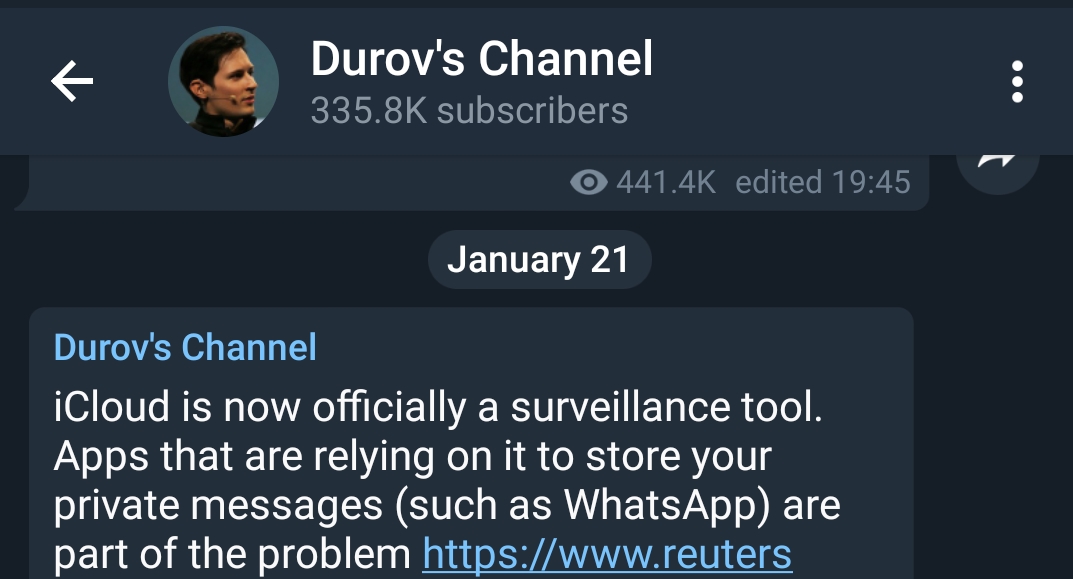
Telegram founder Pavel Durov said today that “Now icloud is an official Officially a Suvillence Tool, Apple that relying on it to Store your private Message including WhatsApp is part of the problem.”
In the first half of the last year, Apple mostly received requests for data from government agencies, U.S. authorities.
Apple said this in their transparency report, Authorities are armed with regular court papers asked for and obtained full device backups or other iCloud content in 1,568 cases, covering about 6,000 accounts.
Due to this Plan, Apple wouldn’t have been able to turn over any readable data belonging to users who opted for end-to-end encryption and focus to protect some of the user’s most sensitive information such as health data and saved password.
“But backed-up contact information and texts from iMessage, WhatsApp, and other encrypted services remain available to Apple employees and authorities,” Router said.



.png
)
