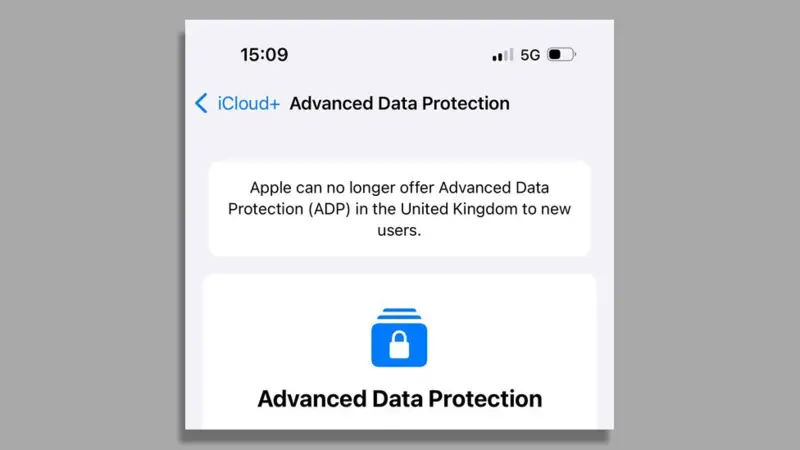
Apple has discontinued its Advanced Data Protection (ADP) feature for UK users following a legal demand from the British government to access encrypted user data.
The move marks a pivotal moment in the ongoing global debate over privacy rights and national security, with critics warning of far-reaching implications for consumer security and international tech policy.
Background and Immediate Impact
ADP, introduced globally in December 2022, offered opt-in end-to-end encryption for iCloud data, ensuring only users could access photos, documents, and backups. Until now, Apple could not decrypt this data, even under legal orders.
However, a notice served under the UK’s Investigatory Powers Act (IPA) compelled Apple to provide law enforcement access to user data, prompting the company to disable ADP activation for UK accounts starting February 24, 2024, as per a report by BBC.
Existing ADP users will lose access to the feature in the coming months, reverting their iCloud data to standard encryption, which permits Apple to comply with valid warrants.
The Home Office declined to confirm or deny issuing the IPA notice but stated it “works closely with technology firms to balance privacy with public safety”.
Apple expressed disappointment, emphasizing its refusal to create encryption backdoors: “We have never built a master key, and we never will”.
Cybersecurity experts universally condemned the decision. Professor Alan Woodward of Surrey University called it “an act of self-harm,” arguing that weakening encryption exposes UK users to heightened risks of hacking and surveillance.
Caro Robson, a digital privacy advocate, highlighted the precedent-setting nature of Apple’s withdrawal: “If companies retract security features rather than comply, it destabilizes accountability frameworks globally”.
US lawmakers, including Senator Ron Wyden, warned that the IPA’s extraterritorial application could compel Apple to undermine encryption for non-UK users, jeopardizing US national security.
Wyden urged the Biden administration to reconsider intelligence-sharing agreements with the UK unless the demand is rescinded.
Child Safety vs. Privacy Debate
The National Society for the Prevention of Cruelty to Children (NSPCC) supported the government’s stance, asserting that encryption hinders efforts to detect child sexual abuse material (CSAM).
Rani Govender, NSPCC policy manager, urged Apple to “balance privacy with robust child safety measures”.
However, cybersecurity analyst Emily Taylor countered that CSAM predominantly circulates on unencrypted platforms and the dark web, not mainstream services: “Encryption protects billions of legitimate user interactions daily”.
The dispute reflects broader tensions between governments and tech firms over encryption.
Bruce Daisley, a former Twitter executive, noted Apple’s principled stance: “Conceding to the UK would invite similar demands worldwide”. WhatsApp CEO Will Cathcart echoed this, stating on X: “A UK backdoor puts all users at risk”.
US Vice President JD Vance recently criticized foreign regulation of American tech firms at the Paris AI Summit, signaling growing political resistance to external oversight.
Apple’s withdrawal from the UK market suggests a willingness to prioritize product integrity over regulatory compliance, though the IPA’s global reach leaves lingering uncertainties.
Apple affirmed its commitment to “advancing user security” and hopes to reintroduce ADP in the UK pending legal revisions.
Meanwhile, privacy advocates urge users to employ alternative encryption tools, while governments face mounting pressure to reconcile surveillance needs with digital rights.
As Professor Woodward starkly concluded: “Today’s loss of ADP isn’t just a UK issue—it’s a blow to global trust in data privacy”.
Free Webinar: Better SOC with Interactive Malware Sandbox for Incident Response, and Threat Hunting - Register Here



.png
)
