The year begins brightly and so is the new malware that got added into the world of Cyber Security.
Yes, Babuk Ransomware, happens to be the first Ransomware of 2021 which targets corporate victims in human-operated attacks.
What us Babuk Ransomware?
Babuk Ransomware is a standard ransomware but uses the new techniques such as multi-threading encryption and abusing the Windows Restart Manager.
Own implementation of SHA256 hashing, ChaCha8 encryption, and Elliptic-curve Diffie–Hellman (ECDH) key generation and exchange algorithm are used as encrypting schemes.
Also, Babuk can work with or without command line paramters. If no parameter is given, it is restricted to only encrypt the local machines.
Babuk’s website:

Babuk’s encryption operation
Babuk uses RtlGenRandom to generate 4 random buffers where two are used as ChaCha8 keys, and the other two are used as ChaCha8 nonces.

Then, it will encrypt the second ChaCha8 key using the first key and nonce. After which, the first key is encrypted using the encrypted second key and nonce. This encrypted first key is treated as the Elliptic-curve Diffie–Hellman (ECDH) private key for the local machine.
Then, Babuk generates a local ECDH public key from the private key using the code from the Github ECDH library. Then, it generates a shared secret using the local private key and the author’s hard-coded public key.
This shared secret goes through a SHA256 hashing algorithm to generate 2 ChaCha8 keys, which are used to encrypt files later.
In order to be able to decrypt files, Babuk stores the local public key in the file ecdh_pub_k.bin in the APPDATA folder. Because of ECDH’s mechanism, the ransomware author can generate the shared secret using his own private key and the victim’s public key to decrypt files.
Babuk’s ransomware working
Soon after activation, the ransomware will first kills Windows services and processes known to keep files open and prevent encryption. The terminated programs include database servers, mail servers, backup software, mail clients, and web browsers.
Then Babuk Locker will use a hardcoded extension and append it to each encrypted file, as shown below.

A ransom note named How To Restore Your Files.txt will be created in each folder. This ransom note contains basic information on what happened during the attack and a link to a Tor site where the victim can negotiate with the ransomware operators.

As part of the negotiation process, the ransomware operators ask their victims if they have cyber insurance and are working with a ransomware recovery company.
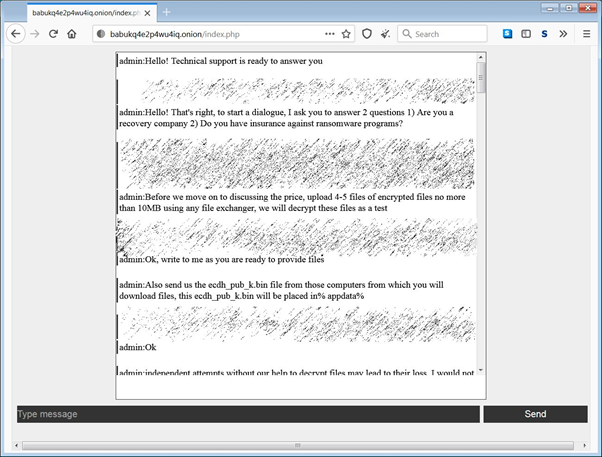
The ransomware operators will also ask victims for the %AppData%\ecdh_pub_k.bin file, which contains the victims’ public ECDH key that allows the threat actors to perform test decryption of victim’s files or provide a decryptor.
It is time for every Organization to be cautious and secure as the Ransomware attacks are growing with new techniques and the risk of the amount to be paid is unimaginable.
You can also read the complete ransomware mitigation checklist
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity, and hacking news updates.



.png
)
